-
 Advanced Email Threats
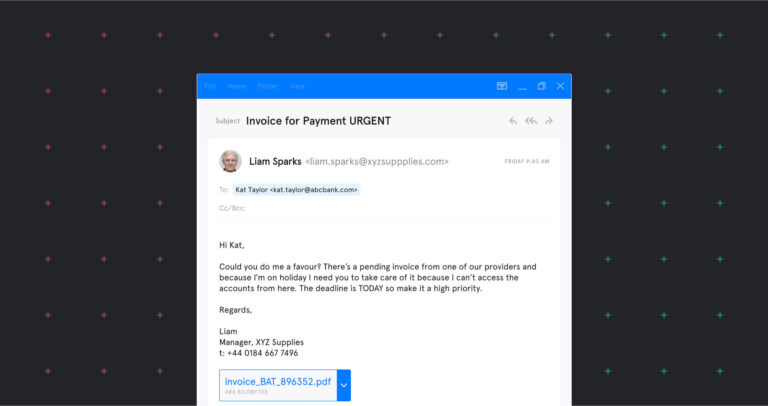
Advanced Email Threats14 Real-World Examples of Business Email Compromise (Updated 2022)
-
 Email DLP, Remote Working, Insider Risks
Email DLP, Remote Working, Insider RisksKeeping Your Data Safe During The Great Re-Evaluation
-
 Advanced Email Threats
Advanced Email ThreatsWhat are Deepfakes? Are They a Security Threat?
-

Introducing HumanLayerSecurity.com: An Online Magazine for Security Leaders
-
 Email DLP
Email DLPThe Ultimate Guide to Data Loss Prevention
-
 Life at Tessian
Life at TessianTessian Named One of ‘Next Big Things in AI and Data’ by Fast Company
-
 Advanced Email Threats
Advanced Email ThreatsWhat Is Credential Phishing and How Does it Work?
-
 Integrated Cloud Email Security
Integrated Cloud Email SecuritySeven Things We Learned at Our Fall Human Layer Security Summit
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityHere’s What’s Happening at our SIXTH Human Layer Security Summit on Nov 4th
-
 Email DLP, Integrated Cloud Email Security, Insider Risks, Compliance
Email DLP, Integrated Cloud Email Security, Insider Risks, ComplianceYou Sent an Email to the Wrong Person. Now What?
-
 Life at Tessian
Life at Tessian200 Reasons to Love Tessian
-
 Advanced Email Threats
Advanced Email ThreatsHow Does Tessian Help Prevent Ransomware Attacks?
-
 Email DLP, Advanced Email Threats, Remote Working, Insider Risks
Email DLP, Advanced Email Threats, Remote Working, Insider RisksHow to Keep Your Data Safe in The Great Resignation
-
 Remote Working
Remote Working5 Reasons to Download Our Back to Work Security Behaviors Report
-
 Threat Stories
Threat StoriesUS Legal Education Provider Spam Campaign Detected
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityMachine vs. Machine: Setting the Record Straight on Offensive AI
-
 Advanced Email Threats
Advanced Email ThreatsHow to Prevent Email Impersonation | What You Can Do Now
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityEmail is the #1 Threat Vector. Here’s Why.
-
 Integrated Cloud Email Security
Integrated Cloud Email Security7 Things We Learned at Tessian Human Layer Security Summit
-
 Advanced Email Threats
Advanced Email ThreatsWhat is Spear Phishing? Targeted Phishing Attacks Explained
Platform
Complete Cloud Email Security
-
Defend-->AI based security to stop the most advanced email threats.
-
Protect-->Behavior based protection to prevent accidental & intentional data loss over email.
-
Respond-->Rapid threat hunting, investigation, and automation for end user reported emails.
-
Coach-->Teach users to assess risk and recognize threats with in-the-moment coaching.
Solutions
Tessian solutions by use case and threat types
-
By Initiative
-
Email Defense in Depth-->
-
Stop Sensitive Data Loss-->
-
By Platform
-
Microsoft 365-->
-
Google-->
Customers
Tessian case studies by use case and industry
Resources
Tessian content by use case and industry
Company
About Tessian's mission and career opportunities







