Investigate and Respond with Ease
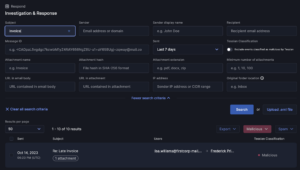
Introducing a game-changing enhancement to our platform: Investigation and Response. Streamline your email threat management with powerful search capabilities, drastically reducing response times and enhancing risk reduction.
Precision in Search
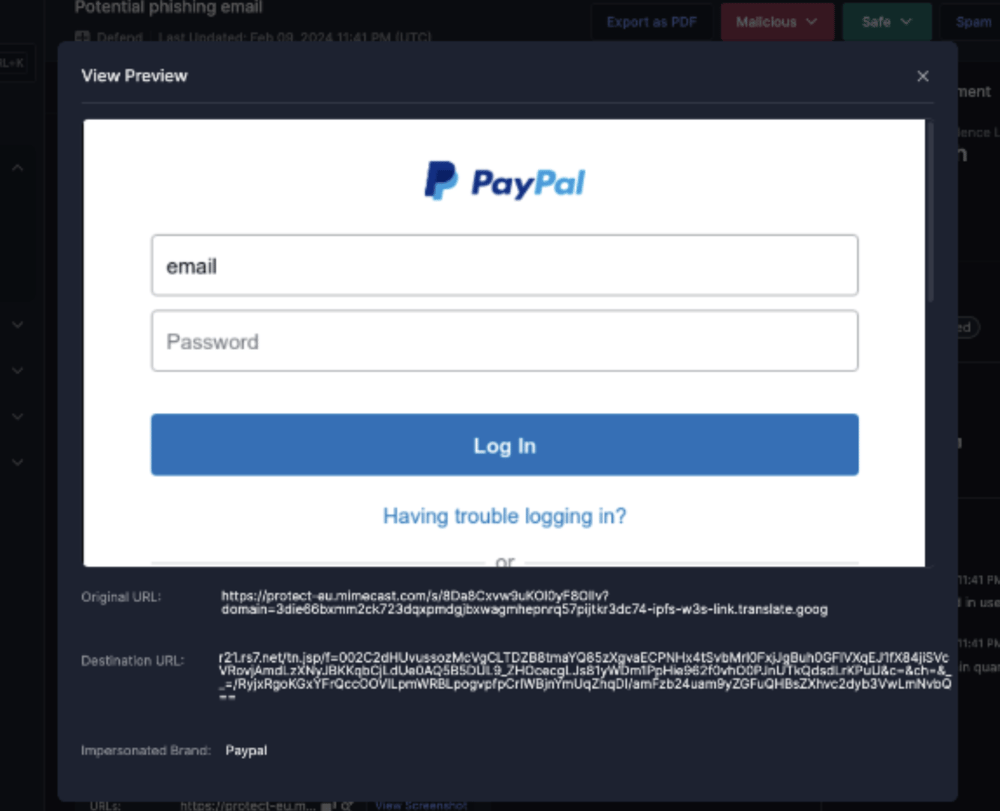
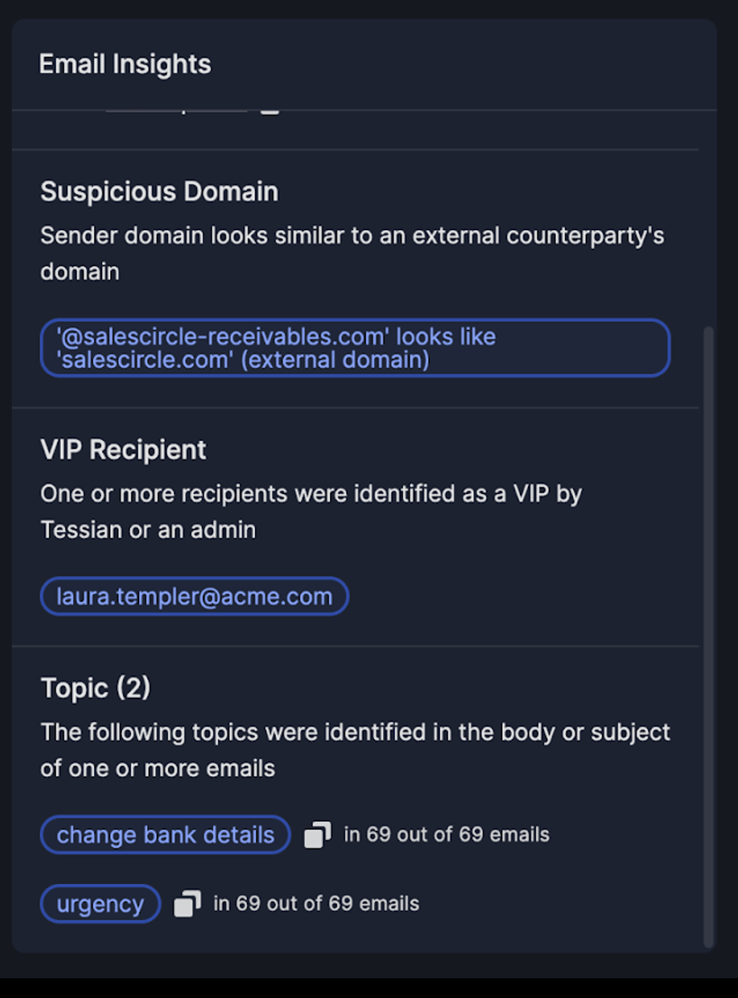
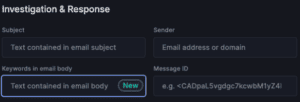
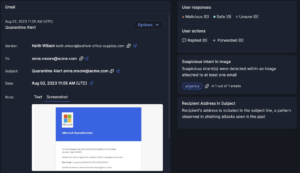
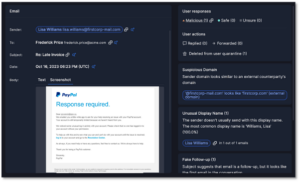
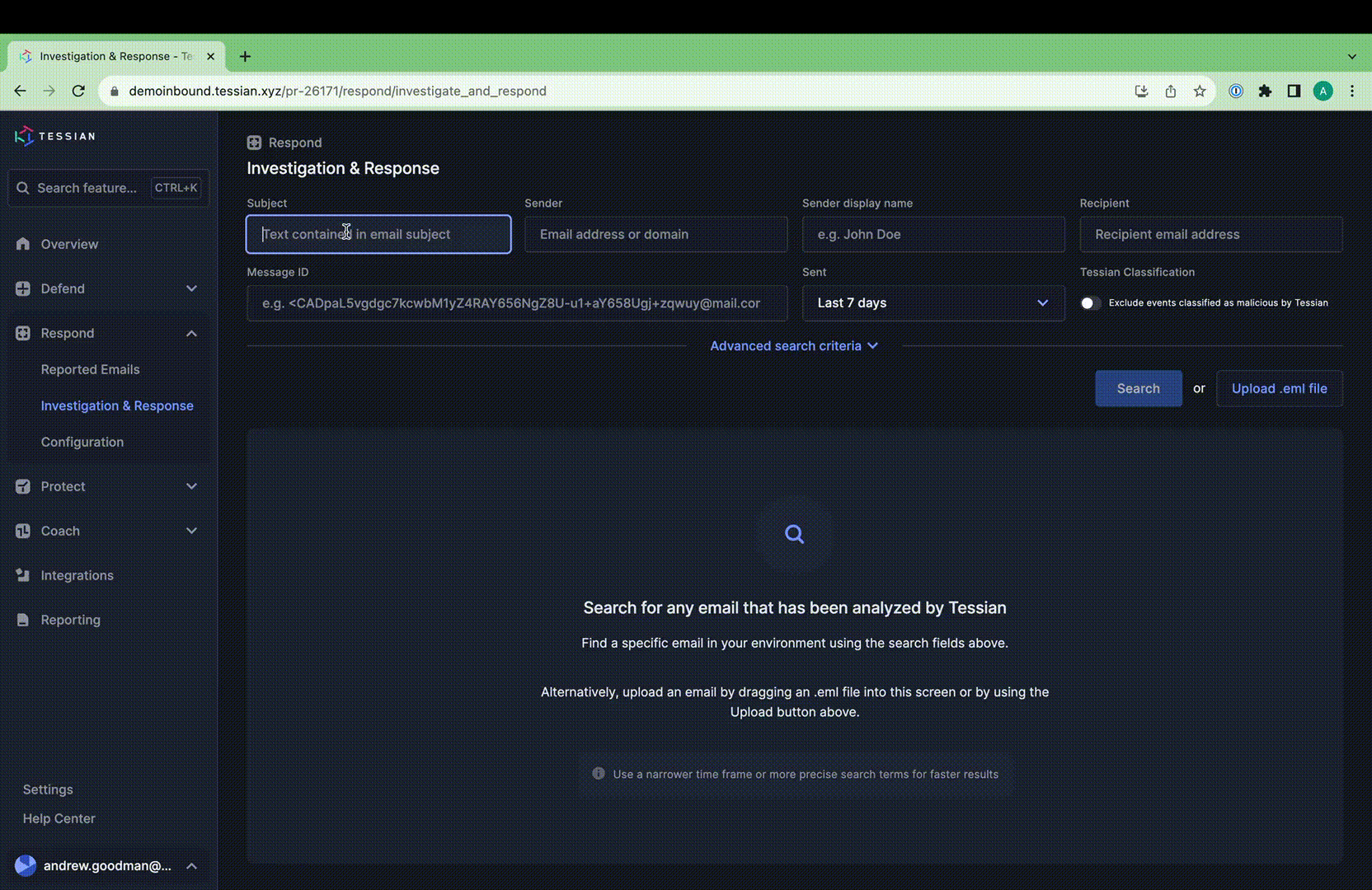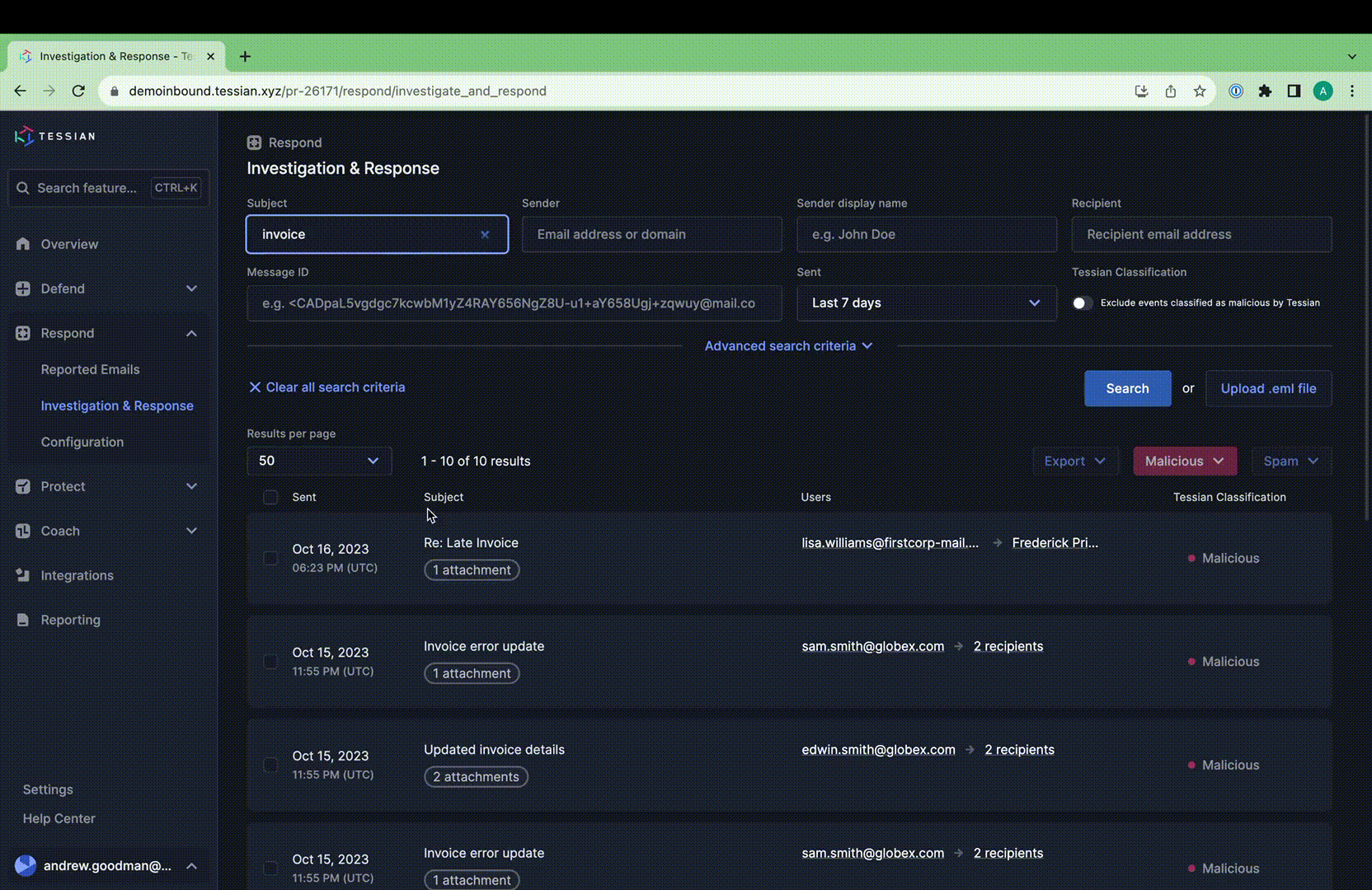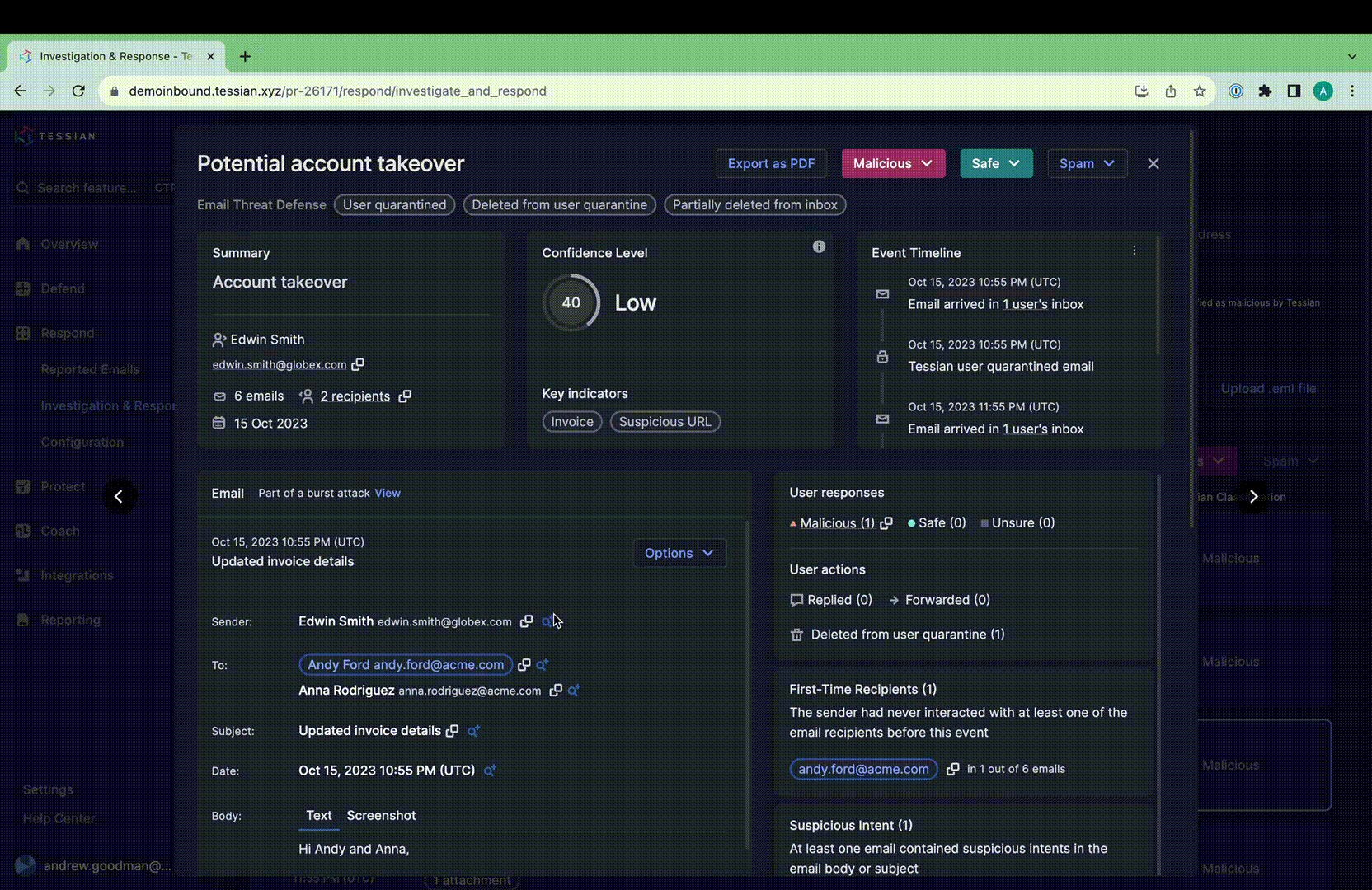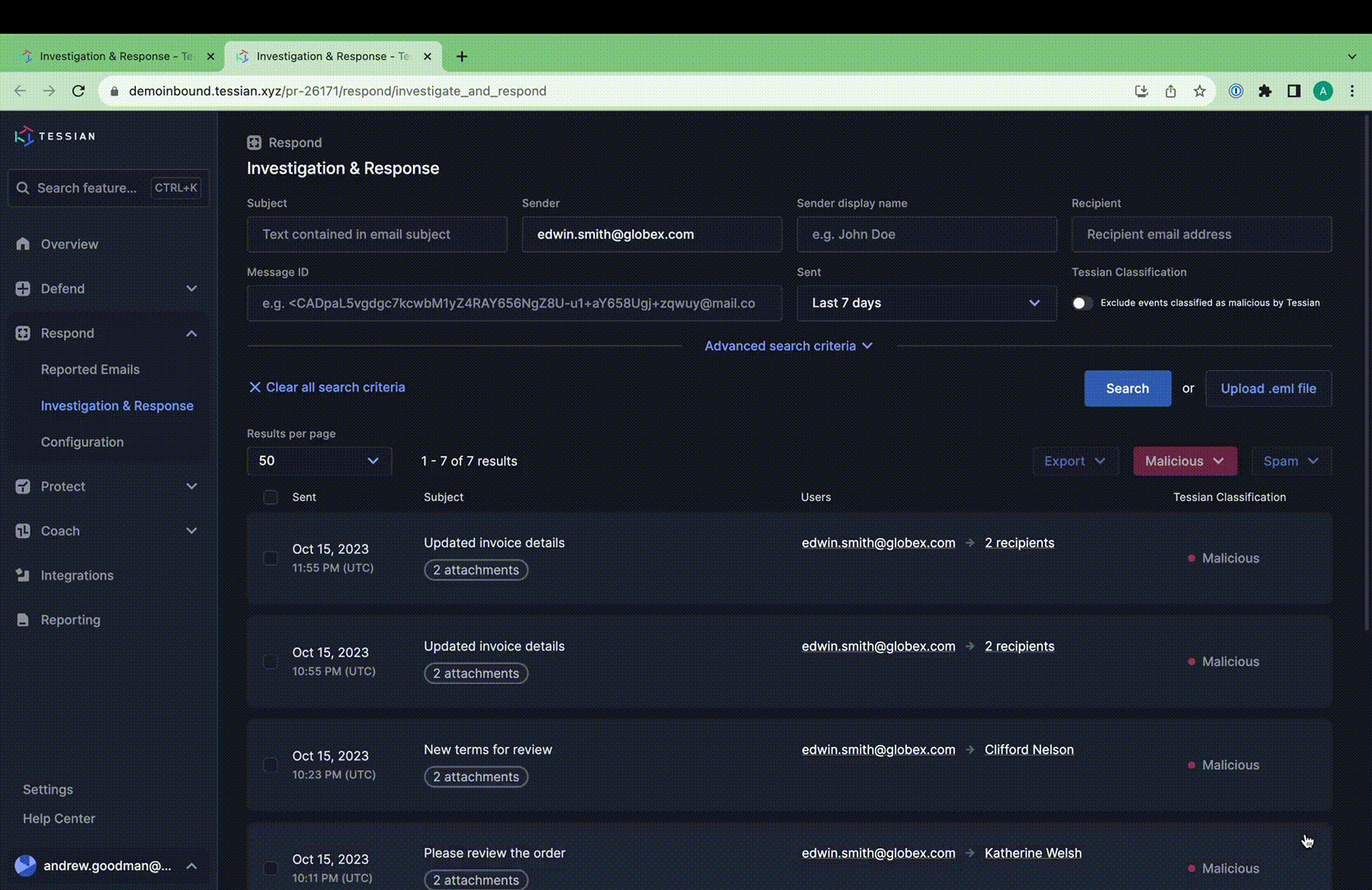
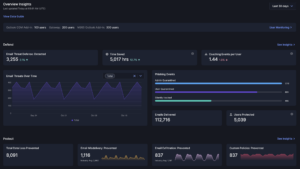
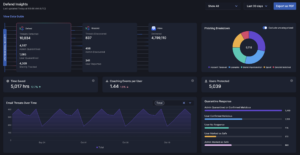
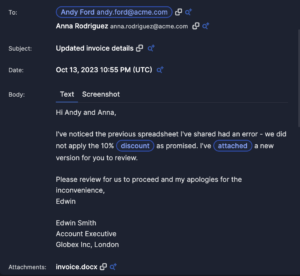
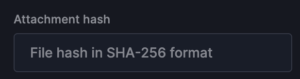
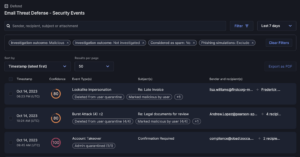
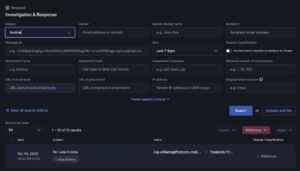
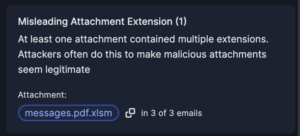
I&R revolutionizes how you locate emails swiftly. Quick identification and resolution of threats significantly mitigate risks. Our array of new search fields empowers you to execute highly specific searches across sender, recipient, and email attributes. For instance, you can identify emails with more than 2 attachments and “Pay” in the subject line.
Proactive Threat Hunting
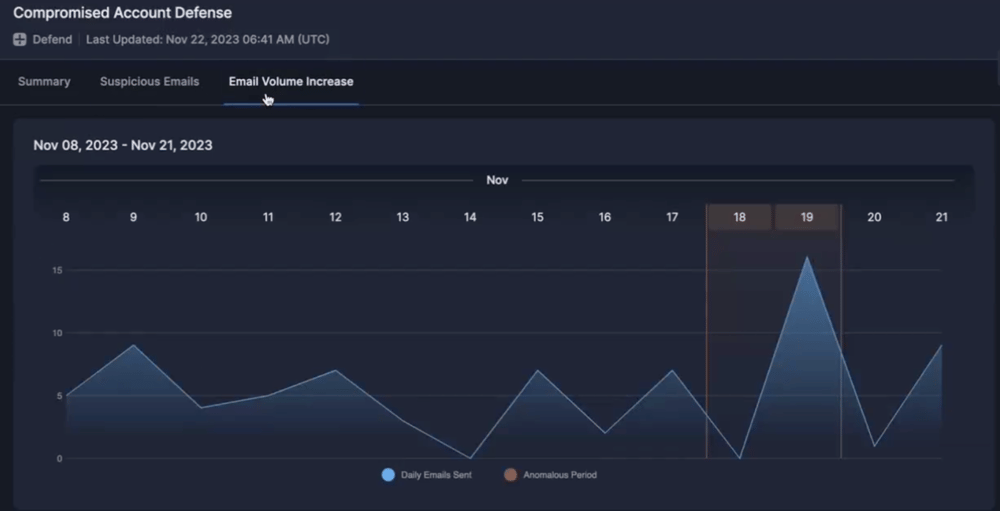
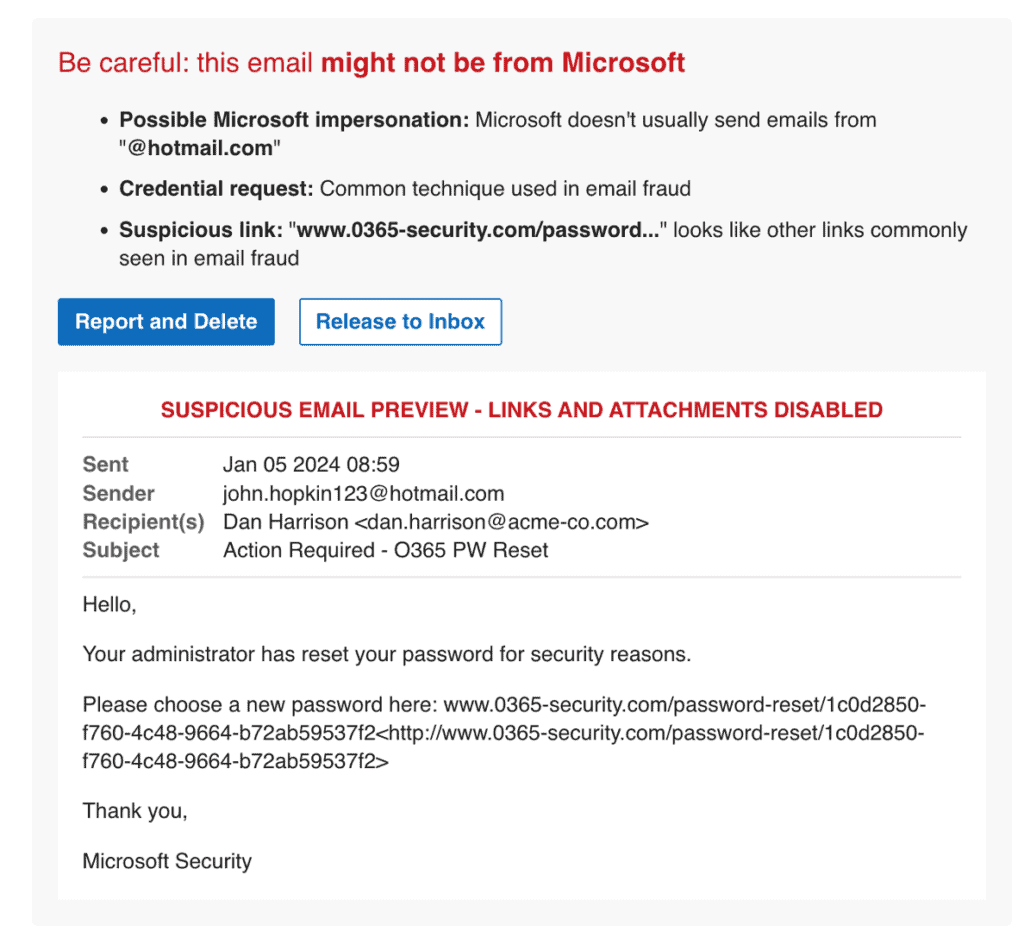
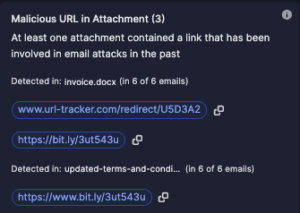
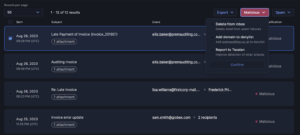
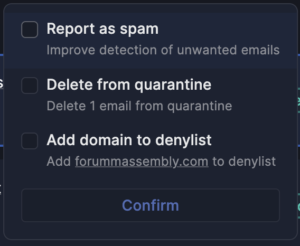
Stay ahead of emerging threats with proactive hunting. Combat evolving or zero-day threats by swiftly searching across your email archives and remediating in just two clicks. I&R supports broad and intricate searches, offering comprehensive flexibility.
Unified Investigation and Remediation
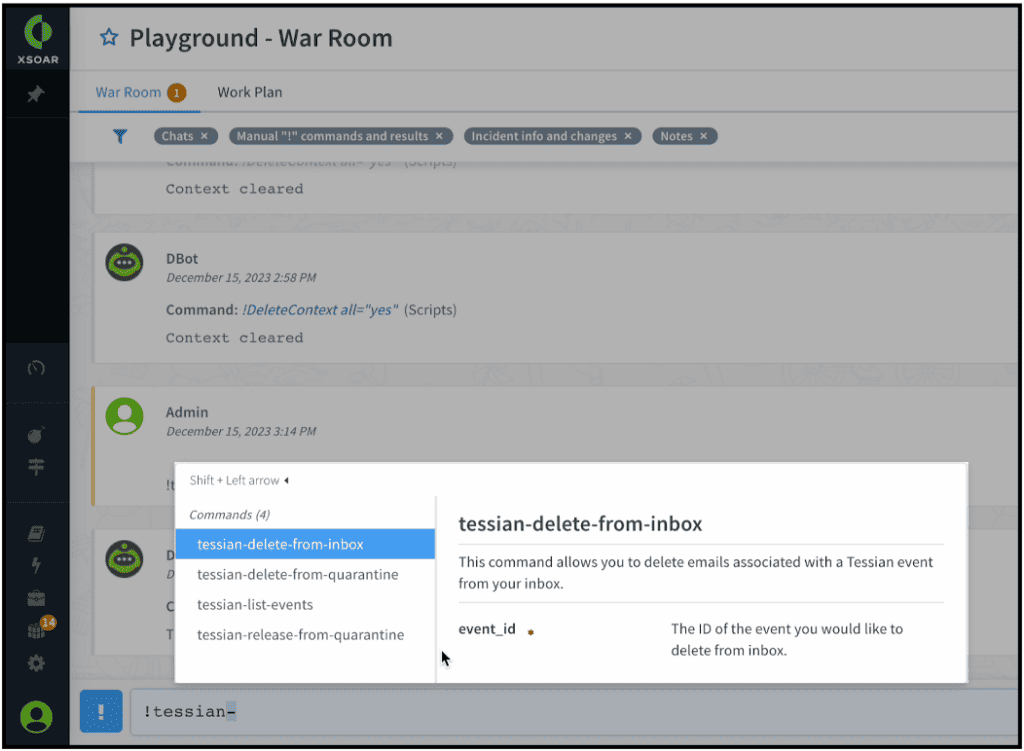
Bid farewell to juggling multiple tools. I&R consolidates email investigations, saving you time and eliminating analyst frustration. What’s more, remediation is seamless within the platform—no need to switch to your email compliance tool.
Internal Risk Resolution
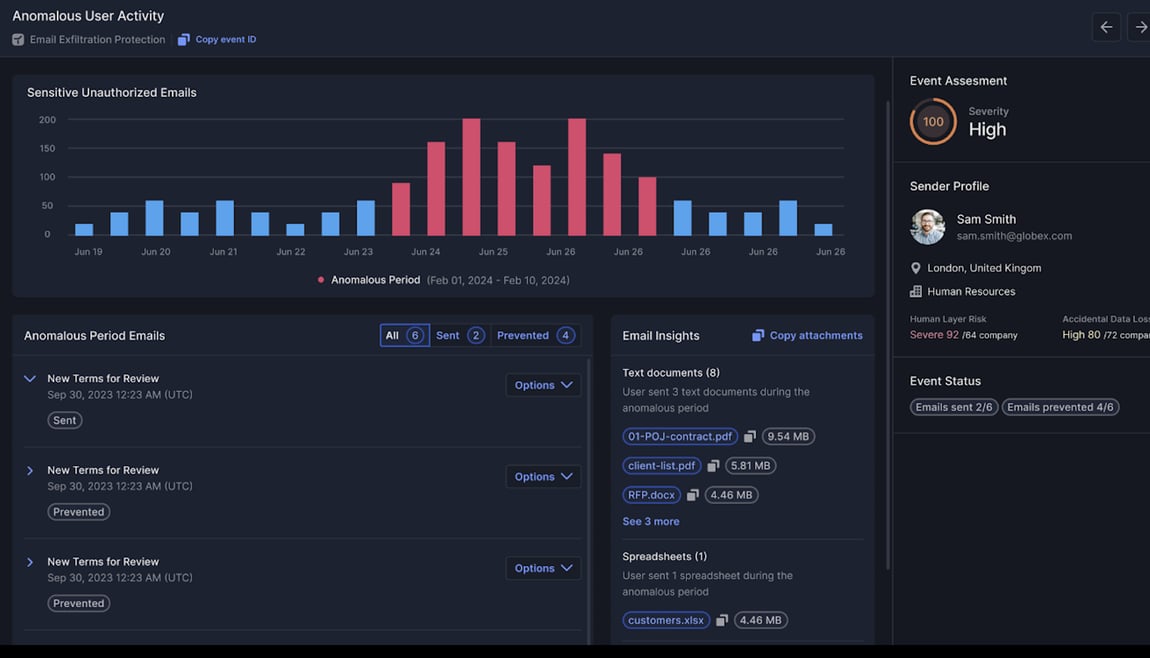
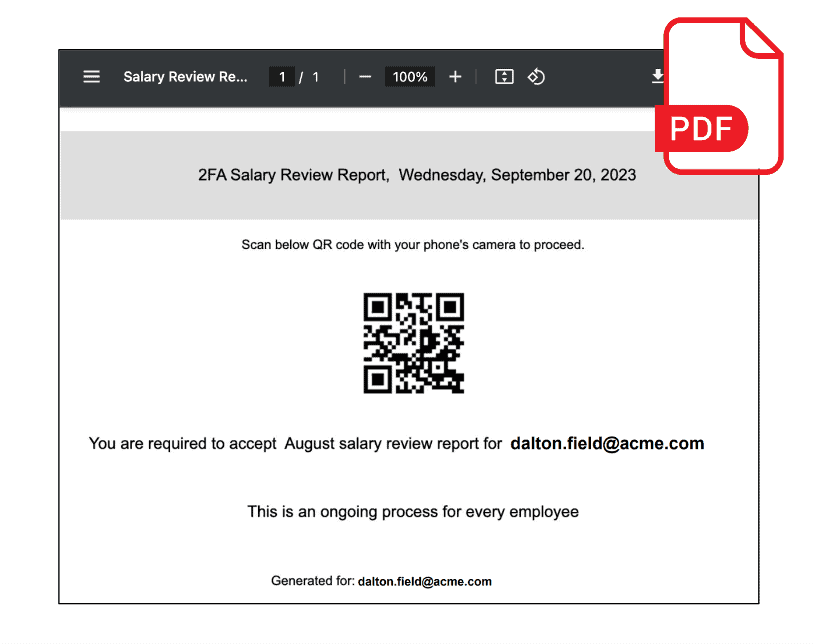
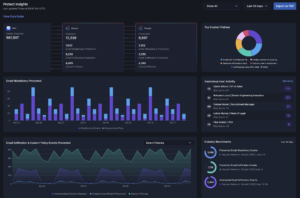
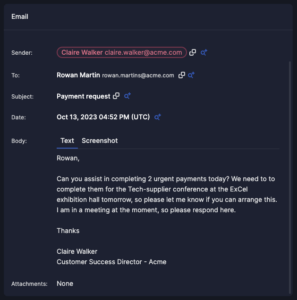
I&R isn’t confined to external threats. Gain visibility into internal email traffic, empowering you to address internal incidents promptly. Prevent unauthorized exposure of sensitive data to internal recipients. Elevate your threat management with I&R—where search, investigation, and remediation unite for enhanced efficiency and security.