First things first: let’s answer the question at hand.
That’s the short and sweet definition. But, there’s more you need to know. Phishing is a common type of social engineering attack that cybercriminals have been conducting for decades. In this article, we’ll take a look at some different types of phishing, how these differ from “traditional” phishing, and how phishing attacks work. Wondering what social engineering is? Check out this article, which includes plenty of real-world examples.
Definitions of phishing
If you look at the definition above, you’ll notice we made an important distinction in the last sentence. “Phishing is typically bulk in nature and not personalized for an individual target.” But, oftentimes, you’ll hear the word “phishing” used as an umbrella term to cover many types of online social engineering attacks, including:
- Spear phishing: A phishing attack targeting a specific individual
- Whaling: A phishing attack targeting a company executive
- Smishing: Phishing via SMS
- Vishing: Voice-phishing, via phone or VoIP software
What links all these types of attacks? They all involve some form of “impersonation” — the attacker pretends to be a person or institution that the target is likely to trust. But, in this article, we’ll focus on traditional “spray and pray” phishing attacks. It’s one of the most straightforward types of online social engineering attacks.
Importantly, this “old-school” form of cybercrime is distinct from all the examples above because:
- Unlike smishing or vishing, phishing attacks occur via email.
- Unlike spear phishing and whaling, traditional phishing isn’t targeted. Attackers send phishing emails indiscriminately, rather than emailing a specific individual.
If you’re scratching your head trying to figure out how phishing is different from spam, we’ve answered all your questions in this article: Spam vs. Phishing: The Difference Between Spam and Phishing.
How phishing works
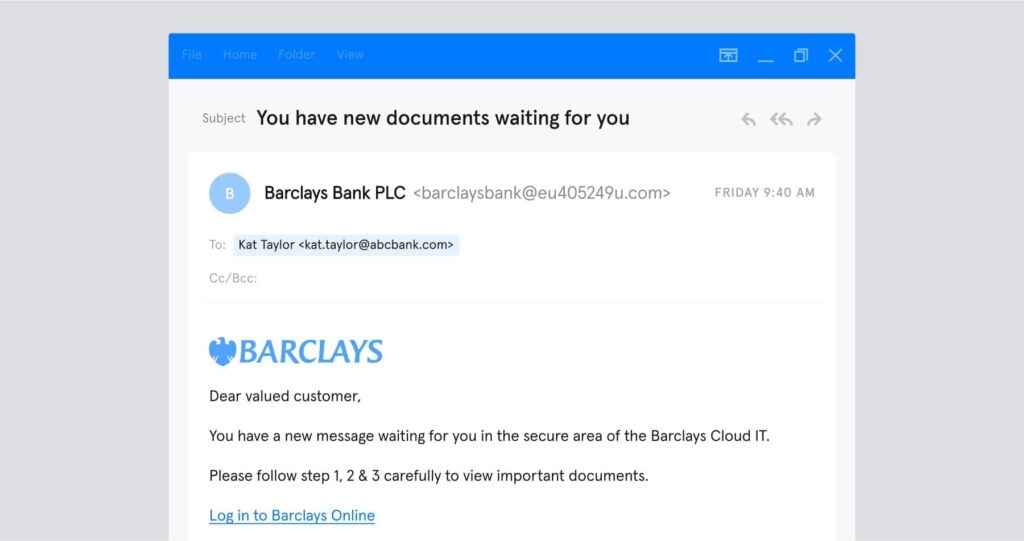
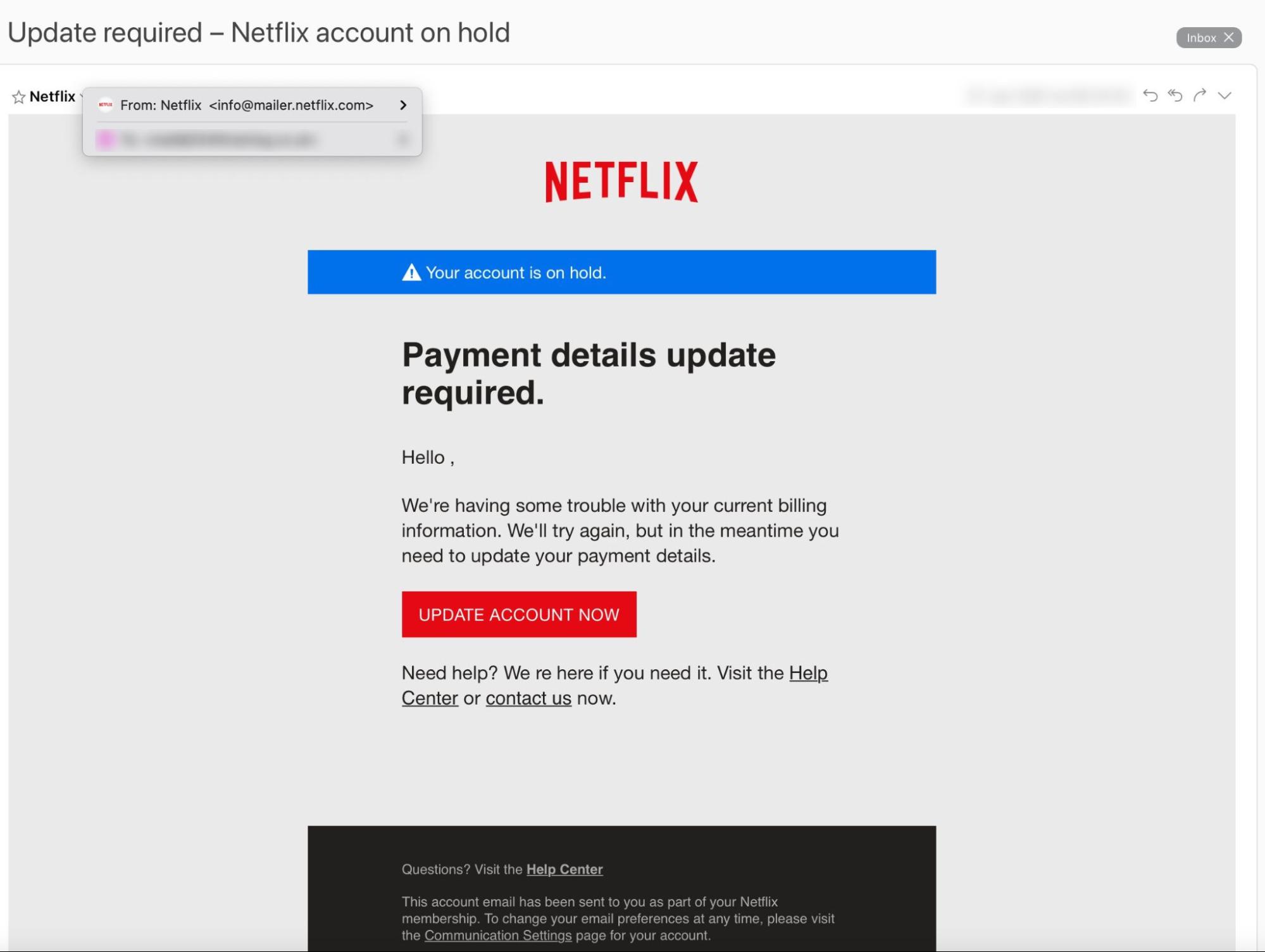
Let’s take a real-life example of a phishing attack to see how this type of cybercrime works. It appears to comes from a brand most of us know and trust: Netflix.
So, what makes it a phishing email? The “UPDATE ACCOUNT NOW” button leads to a malicious website (not Netflix’s genuine website) designed to steal payment information. But, the average person wouldn’t know that.
- The email arrived from “info@mailer.netflix.com” — a person could reasonably believe this was a genuine Netflix email address
- The “Help Center” and “Communications Settings” links lead to Netflix’s actual website
- The Netflix logo and branding look authentic
But look a little closer, and you’ll notice a few giveaways.
- The greeting is generic (“Hello ,”). This suggests that this is a bulk email sent to many recipients.
- The email asks for payment details. Netflix will never request payment information via email.
- There’s a typo (“We re here if you need it”). Typos are increasingly rare in phishing emails, but they should always raise a red flag.
This is not your typical “Nigerian prince” scam and it’s easy to see why so many people – both consumers and employees – fall for these scams. If you’re looking for statistics to back this up, check out this article: Must-Know Phishing Statistics (Updated 2021).
Note that this scam appears to use “email impersonation”: the sender address (mailer.netflix.com) looks like it could be an authentic Netflix domain, but Netflix doesn’t own that domain at all. Hackers can also use account takeover and email spoofing for more advanced phishing attacks.
What is phishing for?
We’ve looked at how criminals use different methods to conduct phishing scams and target different types of people. But why do they do it? Attackers use phishing scams to target different types of resources. For example:
- Credentials. Cybercriminals steal usernames and passwords to sell them on the dark web, access company data, or conduct account take-over attacks.
- Personal information. Addresses, social security numbers — even lists of names associated with a particular platform can be valuable to cybercriminals, who can use them to target spear phishing attacks.
- Money. Phishing attacks aiming to trick the target into transferring money to the attacker are common, but they’re normally reserved for more sophisticated types of phishing such as Business Email Compromise (BEC), which the FBI calls “the $26 billion scam.”
Want to know which of these resources hackers target the most frequently? Download this infographic.
How common is phishing?
Phishing has become a huge criminal industry, and there’s no sign of it getting smaller. Here are some of the latest statistics:
- The FBI’s Internet Crime Complaint Centre (IC3) 2020 Internet Crime Report cites phishing as the leading cause of cybercrime complaints. Phishing complaints more than doubled between 2019 and 2020.
- According to Verizon’s 2020 data breach report, 96% of phishing attacks arrive by email (smishing and vishing account for 3% and 1% of attacks, respectively).
- Phishing is on the rise. Microsoft’s 2021 Future of Work report shows that 80% of organizations experienced an increase in security threats in 2020 — and of these, 62% said phishing showed the most significant increase.
- As a major cause of data breaches, phishing is a considerable business expense. According to IBM, the average cost of a data breach in 2020 was $3.86 million.
Want more of the most up-to-date figures on phishing? Subscribe to our newsletter for monthly updates, straight to your inbox. Now you know what “phishing” means, how common it is, and how much damage it can cause. If you want to learn how to protect yourself from phishing, check out our guidance on how to avoid falling for phishing attacks.