It’s a fact that C-suite executives are high-profile targets. According to Verizon’s Data Breach Investigations Report, a C-level executive is 12 times more likely to get phished than a junior employee.
Why? Because when you control the head you can control the body. Hack a CxO, and you have the power to command subordinates with requests such as wire transfers, account access resets, network access, corporate credit card details, and company financial functions.
So how can you help better protect your C-suite from attacks?
In former roles, a current Tessian employee used this training technique to test the c-suite’s resilience to an attack and improve their security awareness. Here’s how you can run this experiment on your c-suite; we’ve anonymized and edited some of the details for security and clarity.
The technique
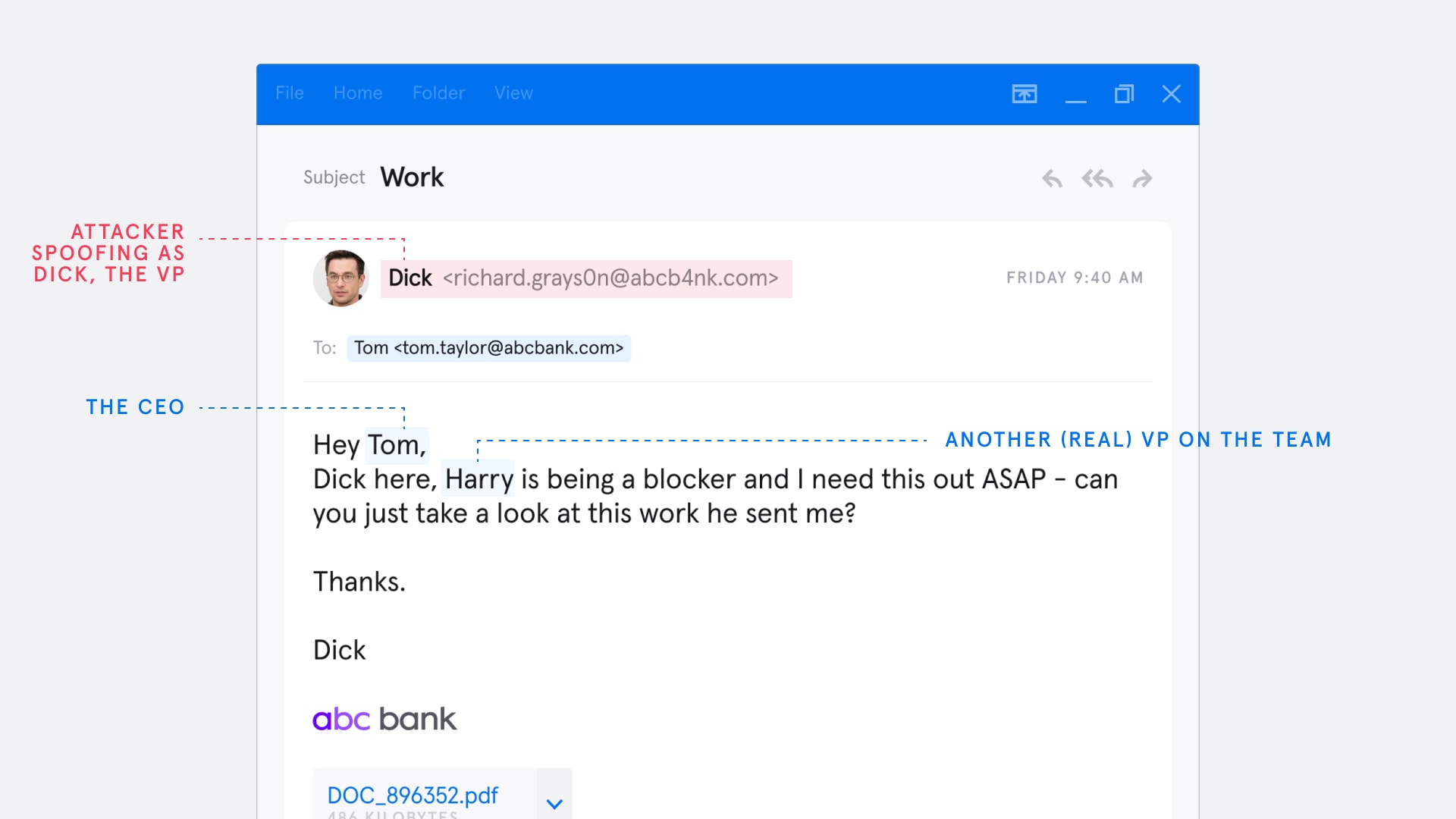
The target for the attack is a CxO or another highly senior person in your company. Your first step is to send a ‘spoof’ email from one of the senior VPs on the team to the target. For real attackers, finding the targets is easy enough as most companies list out their senior team on their websites, sometimes even complete with links to their LinkedIn profiles. And even if the information isn’t available there, it’s easy enough to find with a quick Google search or browse around social media.

The message you design from the spoof account has to say something along the lines of “Hey Tom (CxO), Dick here, Harry (another real VP on the team) is being a blocker and I need this out ASAP, can you just take a look at this work he sent me.”
The ‘work’ is of course a document containing the malware. Phrased in this way there is an extremely high probability that Tom, the CxO, will open that attachment. As our anonymous employee explains, “you don’t even need to hack a VP account, you can simply spoof it. I’ve had clicks on this with email metadata that clearly does not match.”
The psychology of why this is so effective
Why this works so well, despite not being a particularly technologically sophisticated technique, is all to do with human nature and the power dynamics found in the top tier of organizations. The message is ‘validated’ because it is supported in the target’s mind by using a bond of trust the CxO has in Harry, the innocent VP. But the attacker is borrowing that trust bond to psychologically ‘authenticate’ the email with the target.
“The beauty of this technique is that it’s a method of phishing where the higher you go up the corporate ladder, the more this works. ”
Tessian Employee
This is textbook social engineering, which is the technique of manipulating the victim’s natural emotional responses and reactions. Which is why we see other classic ingredients common in phishing attacks like a sense of urgency (I need this ASAP) and a cry for help or a perceived problem that only the target can rectify. After all, there’s some evidence that humans are born with an urge to help.
Why do senior leaders fall for this?
This exercise manipulates the tendency for senior leaders to overvalue trust bonds from people closest to them and undervalue potentially conflicting information coming from those far below in the org chart. The fact that the message appears to have come from two people that the CXO talks to all the time means they will tend to overvalue communication with them.
Furthermore, the message is contextualized around potential turbulence in the relationship dynamic within that inner circle, rather than an external generic ‘your accounts been suspended’ phishing attempt. This only adds to its legitimacy.
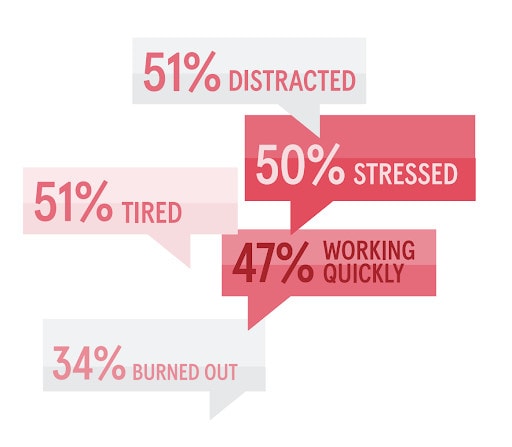
As for that relationship turbulence, our recent psychology of Human Error 2022 report found that people make mistakes when they are in highly emotional states. Catch the CxO when they’re distracted, stressed or working quickly and the odds of them clicking only increase.
Finally, traditional SAT training for the C-suite often means they’re aware of it’s deployment across the organization, making it even harder for them to experience a genuine attack moment.
Advice for running this experiment in your organization
If you’re looking to run this phishing test on your team, there are two important principles to consider. The first: don’t cause chaos on your own network. The second: this is about building relationships with the security team, not about adversarial content. “The most important thing is consent,” advises our employee. All too often companies run phishing programs that don’t involve other people and teams before they start their campaigns.
To do this successfully, you’ll need to define parameters such as:
-
Who is this test targeted at?
-
What will the message describe?
-
What am I allowed to include in the payload?
-
Between what dates will I run the test and at what time?
-
What happens after the click?
That last one is perhaps the most important. What program will you have in place for those who fall for the phish? Remember, these are high-profile people with limited time, so your response has to be concise yet impactful.
Consider scheduling a face-to-face 15-minute discussion where you can explain how the attack worked and what the employee should do in the future. Be sure to back this up by evidence and statistics on what happens when a C-suite member gets hacked, and what the impact is on the organization. The aim is to connect their click event, with specific actionable risks being brought into the business.
Technology can help, too. Tessian Defender would have detected this social engineering attack as the metadata in the email address wouldn’t have matched the legitimate address. Defender could have quarantined it for SOC analysis or alerted Tom, the CxO, in real-time with an ‘in the moment’ notification.
Learn more about how Tessian detects and prevents BEC attacks, ATO attacks, CEO Fraud, and other advanced email threats by watching our product tour, or book a demo to learn more.
KC O'Carroll
Head of Security Engineering & Operations