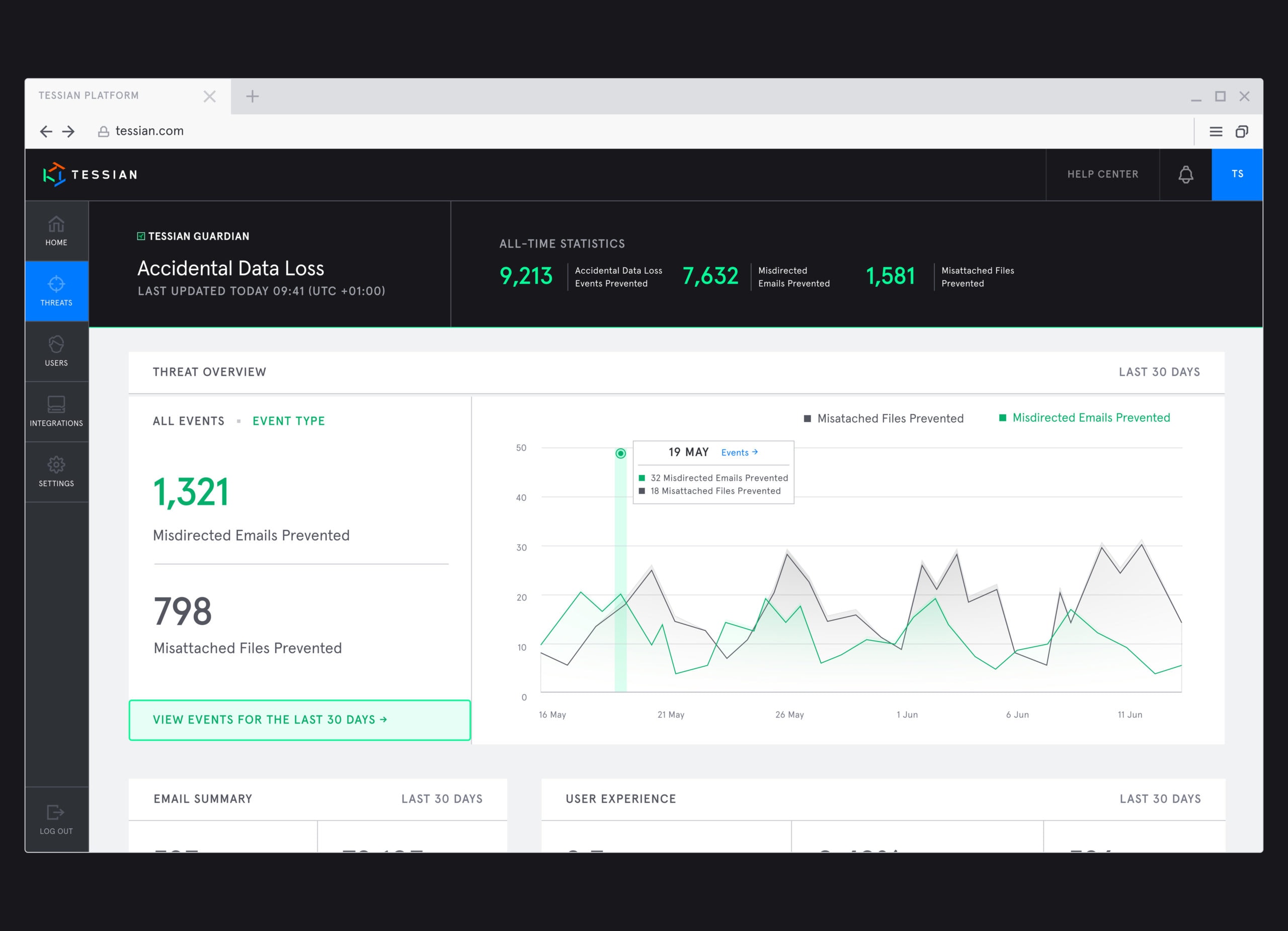
Misdirected emails – emails sent to the wrong person – are the number one security incident reported to the Information Commissioner’s Office. And, according to Tessian platform data, an average of 800 misdirected emails are sent every year in organizations with over 1,000 employees.
An unsolved problem
We solved this years ago with Tessian Guardian, our solution for accidental data loss.
But sending an email to the wrong person is just one part of the problem. What about sending the wrong attachment? After all, our data shows that 1 in 5 external emails contain an attachment and new Tessian research reveals that nearly half (48%) of employees have attached the wrong file to an email.
We call these “misattached files” and we’re happy to announce a new, industry-first feature that prevents them from being sent.
The consequences of attaching the wrong file
The consequences of a misattached file depend on what information is contained in the attachments.
According to Tessian’s survey results, 42% of documents sent in error contained company research and data. More worryingly, nearly two-fifths (39%) contained security information like passwords and passcodes, and another 38% contained financial information and client information.
36% of mistakenly attached documents contained employee data.
Any one of the above mistakes could result in lost customer data and IP, reputational damage, fines for non-compliance, and customer churn. In fact, one-third of respondents said their company lost a customer or client following this case of human error, and a further 31% said their company faced legal action.
Until now, there weren’t any email security tools that could consistently identify when wrong files were being shared. This meant attachment mistakes went undetected…until there were serious consequences.
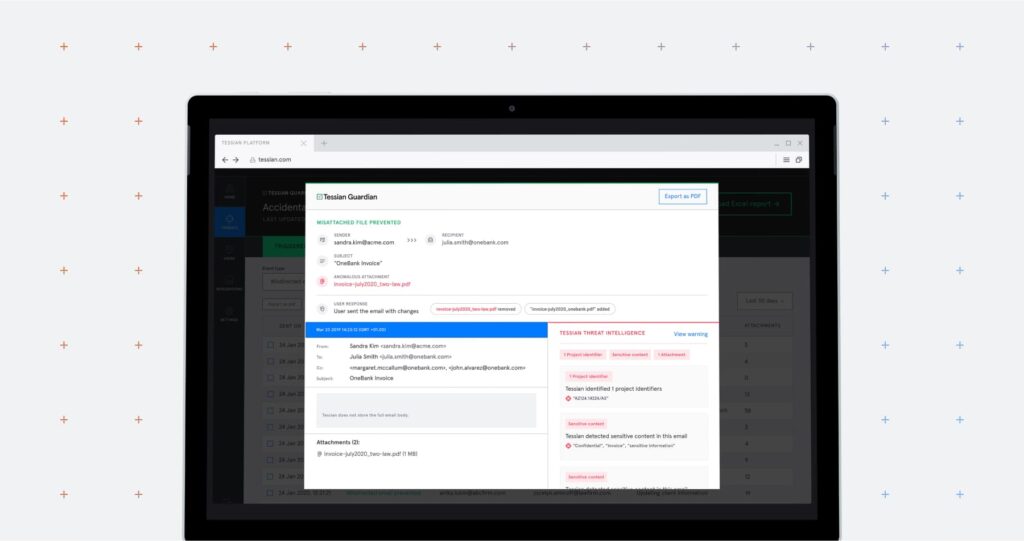
How does Tessian detect misattached files?
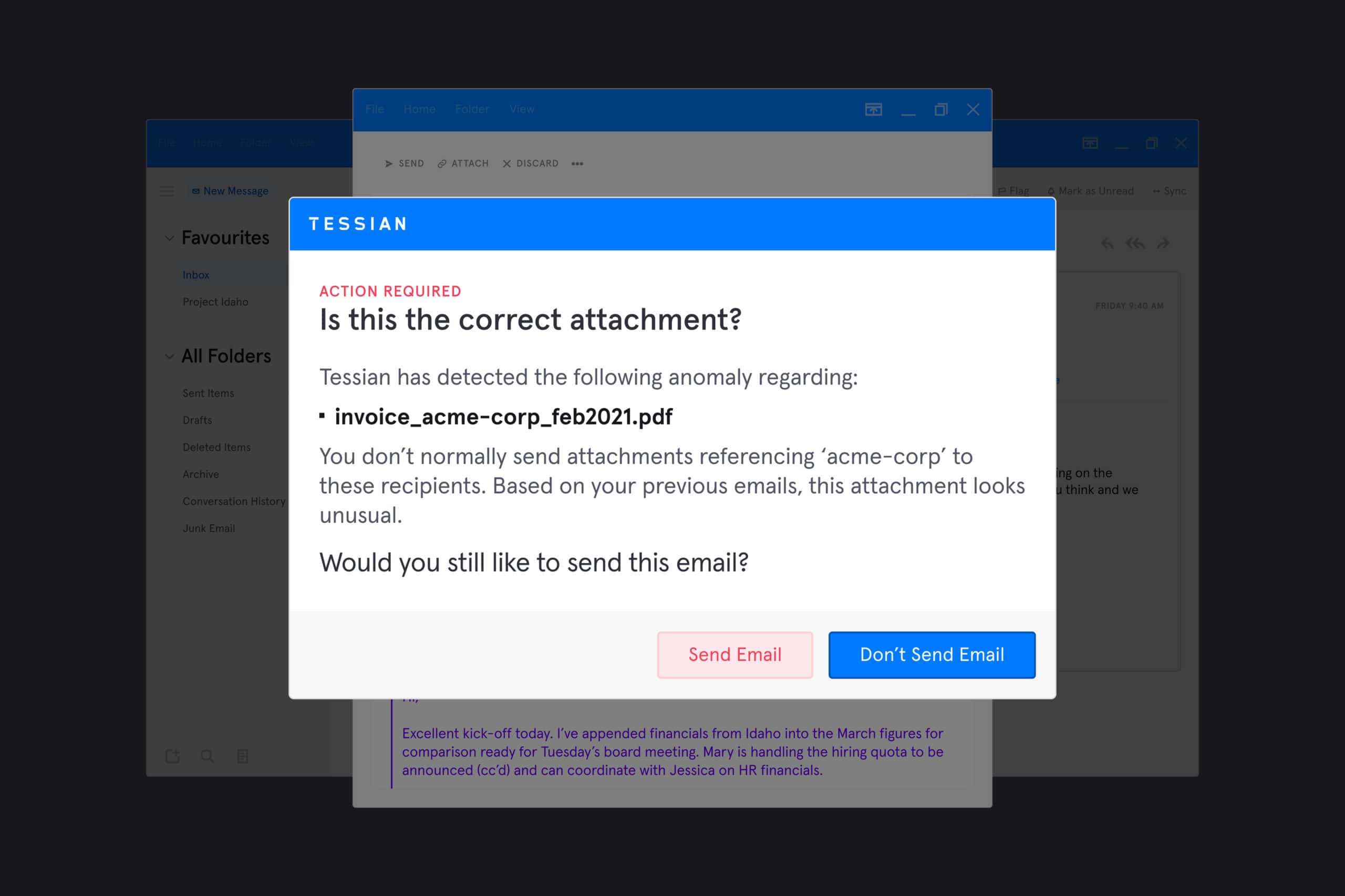
The latest upgrade to Tessian Guardian leverages historical learning to understand whether an employee is attaching the correct file or not.
When an email is being sent, Guardian’s machine learning (ML) algorithm uses deep content inspection, natural language processing (NLP), and heuristics to detect attachment anomalies such as:
- Counterparty anomalies: The attachment is related to a company that isn’t typically discussed with the recipients. For example, attaching the wrong invoice.
- Name anomalies: The attachment is related to an individual who isn’t typically discussed with the recipients. For example, attaching the wrong individual’s legal case files.
- Context anomalies: The attachment looks unusual based on the email context. For example, attaching financial-model.xlsx to an email about a “dinner reservation.”
- File type anomalies: The attachment file type hasn’t previously been shared with the receiving organization. For example, sending an .xlsx file to a press agency.