Today, a comprehensive email security strategy needs to do more more than just secure an organization’s own email platform and users. Why? Because more and more often, bad actors are gaining access to the email accounts of trusted senders (suppliers, customers, and other third-parties) to breach a target company.
This is called account takeover (ATO) and one in seven organizations have experienced this kind of attack.
And, since legitimate business email accounts are used to carry out these attacks, it is one of the most difficult impersonation attacks to detect, making most organizations vulnerable to ATO.
But, not Tessian customers. Tessian Defender can now detect and prevent ATO.
How does Tessian Defender detect ATO?
Unlike Secure Email Gateways (SEGs) – which rely almost exclusively on domain authentication and payload inspection – Tessian Defender uses machine learning (ML), anomaly detection, behavioral analysis, and natural language processing (NLP) to detect a variety of ATO signals:
- Unusual sender characteristics: This includes anomalous geophysical locations, IP addresses, email clients, and reply-to addresses
- Anomalous email sending patterns: Based on historical email analysis, Tessian can identity unusual recipients, unusual send times, and emails sent to an unusual number of recipients
- Malicious payloads: Tessian uses URL match patterns to spot suspicious URLs and ML to identify red flags indicative of suspicious attachments
- Deep content inspection: Looking at the email content – for example, language that conveys suspicious intent – Tessian can detect zero-payload attacks, too
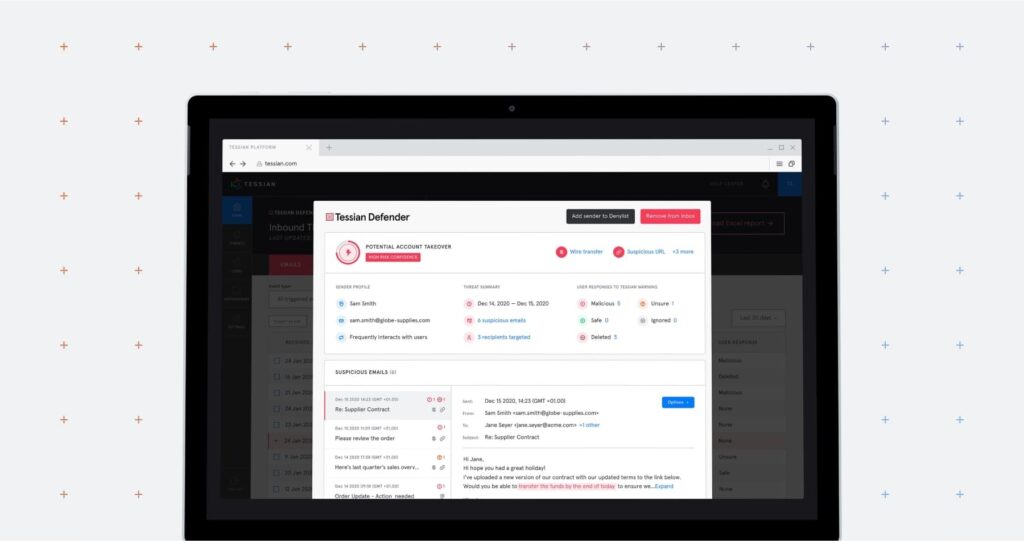
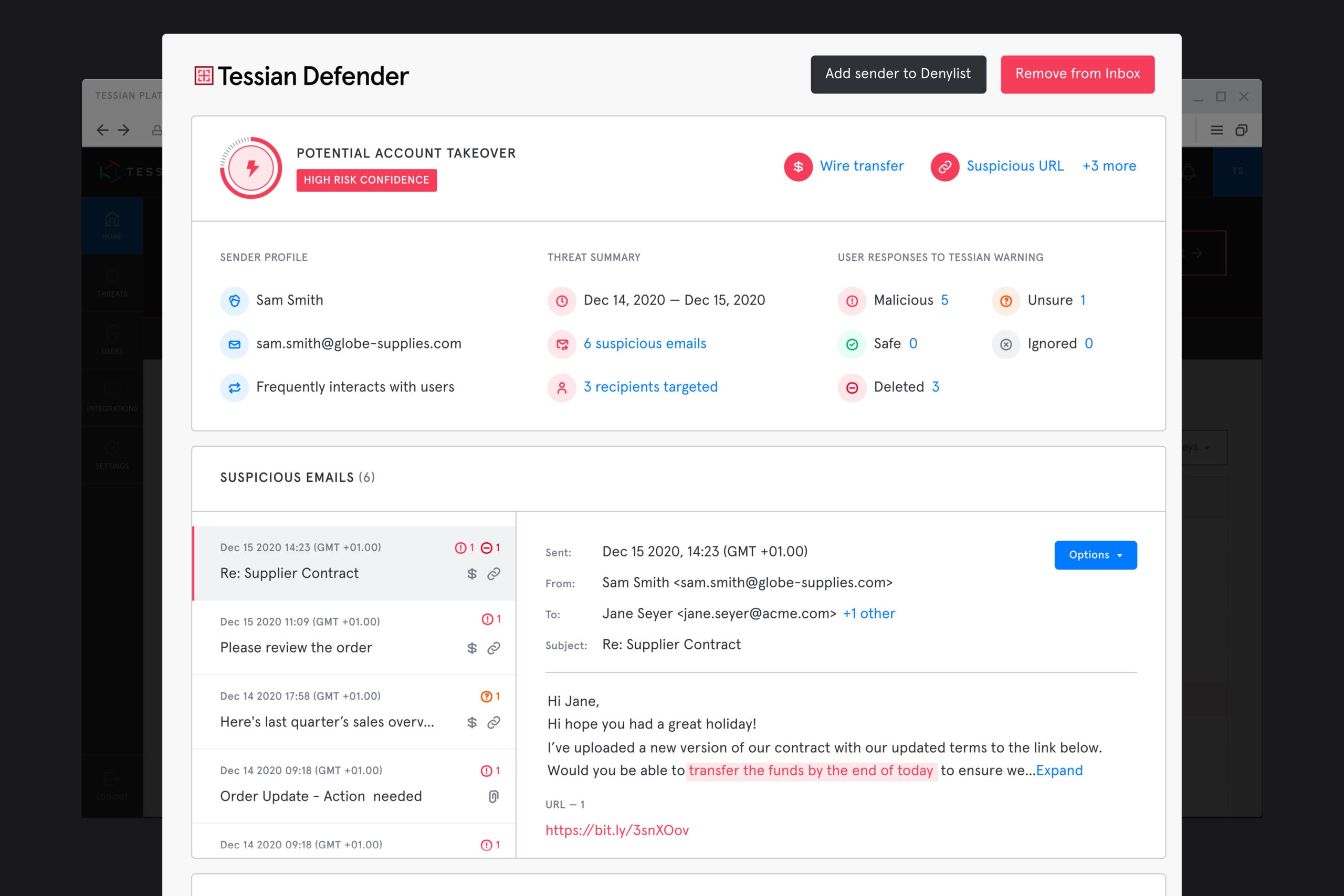
This image shows how Tessian Defender analyzes the content and metadata of an email to detect ATO.
Importantly, Tessian’s ML algorithm gets smarter as it continuously analyzes email communications across its global network. This way, it can build profiles of organizations (and their employees) to understand what “normal” email communications look like at a granular level.
This allows Tessian Defender to catch even the most subtle ATO attacks.
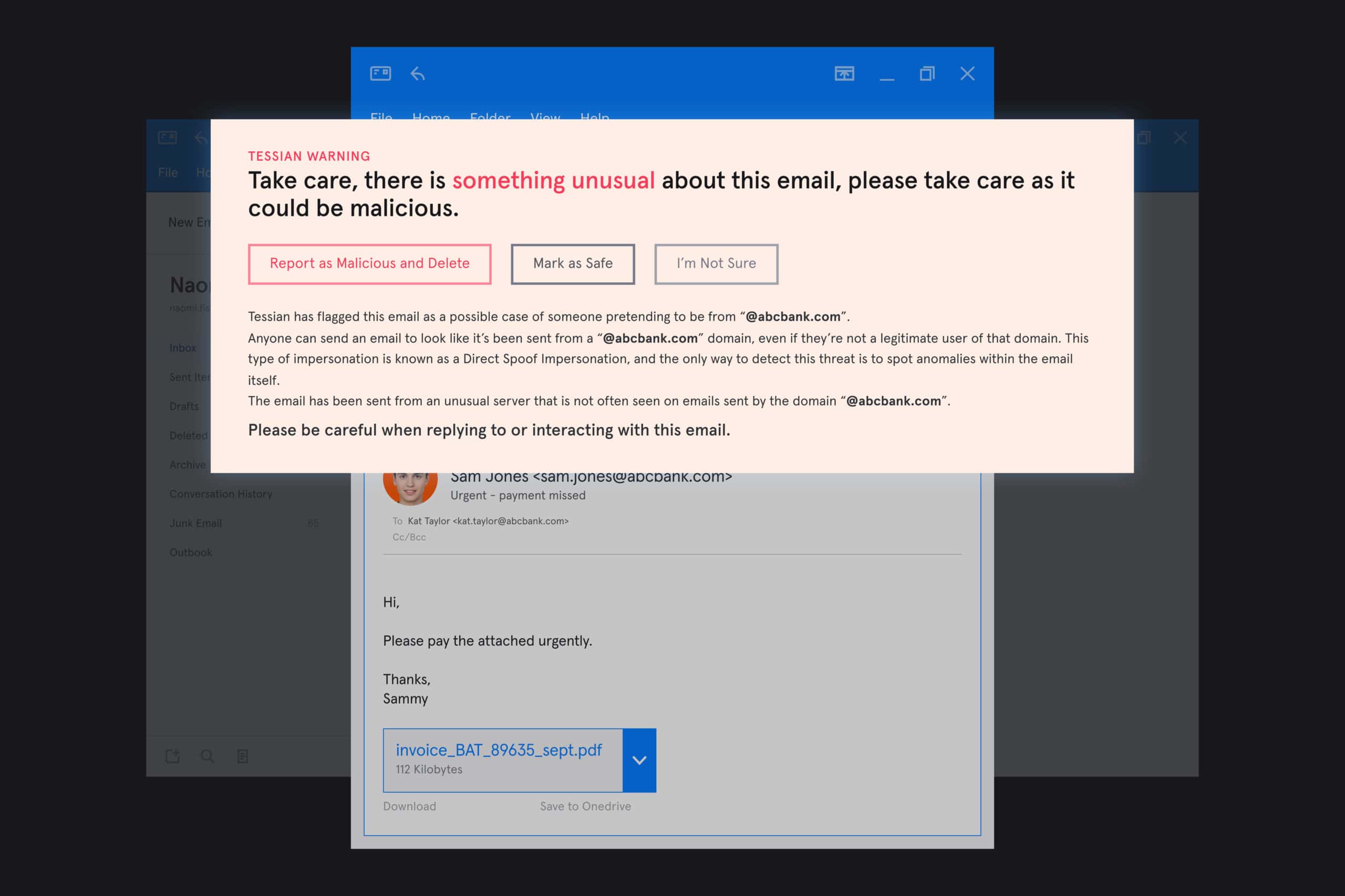
Once it detects a threat, Tessian alerts employees and admins that an email might be unsafe. The warnings are written in easy-to-understand language and explain why an email has been flagged, which prevents the users from responding to the email or clicking on malicious links or attachments. These warnings also act as in-the-moment training and help improve email behavior over time.
Administrators get real-time alerts of ATO and can track events in the Human Layer Security Intelligence portal.
You can learn more about how Tessian detects and prevents ATO here.
Keep reading to see an admin’s view of the portal and what a warning looks like for employees.
What are the benefits of Tessian ATO threat protection?
The consequences of ATO are far-reaching.
Attackers could gain access to credentials, employee data, and computer data. They could initiate fraudulent wire transfers, conduct bank fraud, and sell data. That means organizations could suffer significant financial loss, reputational damage, and lose customers (and their trust). And this doesn’t even account for lost productivity, data loss, or regulatory fines.
Between 2013 and 2015, Facebook and Google were scammed out of $121 million after a hacker impersonated a trusted vendor. And that’s just one example.
Tessian’s ATO threat protection minimizes these risks by preventing successful attacks.
But, detecting and preventing threats is just one of the benefits of Tessian.
For security teams
In the portal, admins can see exactly why an email has been flagged as suspicious, view the content of the email, and access remediation tools.
- Detection is automated, which means it’s not just effective, but also effortless for security teams
- Real-time alerts of ATO events and robust tools (like single-click quarantine) allow for rapid investigation and remediation directly in the portal
- Tessian’s API can be integrated with SIEMs like Splunk and Rapid7, allowing security analysts and SOC teams to analyze Tessian data alongside insights from other solutions
- In-the-moment warnings reinforce security awareness training and help nudge employees towards safer email behavior
For the C-suite
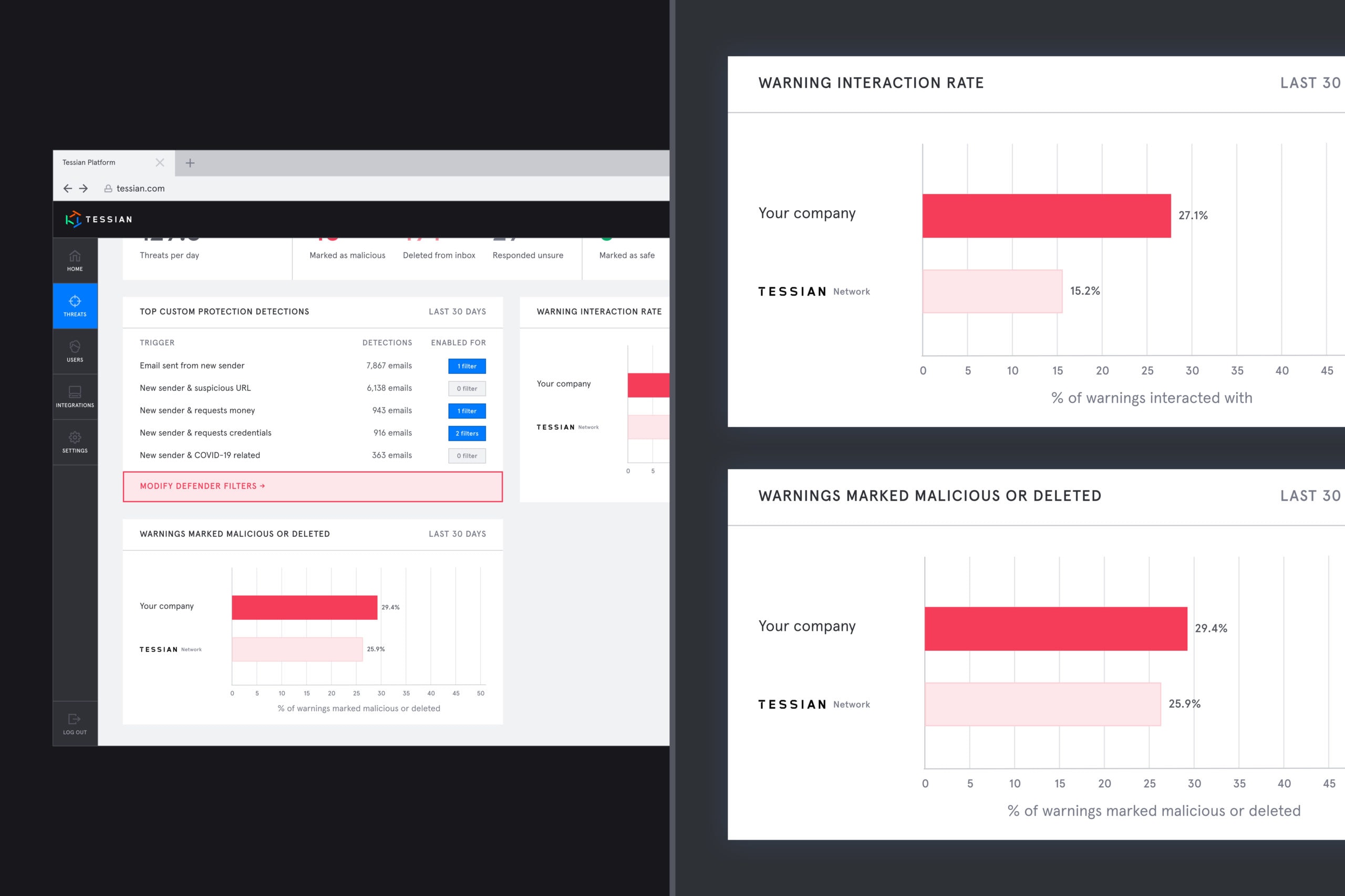
Tessian dashboards show - at a glance - how many threats have been detected, how users are interacting with warnings, and how your organization's security posture compares to industry benchmarks.
- ATO protection doesn’t just keep your organization safe and compliant (and help you avoid reputational damage or financial loss). It’s a competitive differentiator and can help build trust with existing customers, clients, and your supply chain.
- Multi-layer threat insights, visualized data, and industry benchmarks help CISOs understand their organization’s security posture compared to their industry peers
- Automated reports make it easy to communicate success to the board and other key stakeholders
For employees
Tessian's warnings are written in clear, easy-to-understand language to help emplyoee's understand why an email has been flagged. In this case, it's because the email has been sent from an unusual server.
- Contextual warnings are helpful – not annoying – and act as in-the-moment training. This helps employees improve their security reflexes over time for safer email behavior.
- Flag rates are low (and false positives are rare) which means employees can do the job they were hired to do, without security getting in the way
Learn more about Tessian
Interested in learning more about Tessian Defender and ATO Protection? Current Tessian customers can get in touch with their Customer Success Manager.
Not yet a Tessian customer? Learn more about our technology, explore our customer stories, or book a demo now.
Harry Wetherald
Group Product Manager