Phishing and spear phishing are both “social engineering” cyberattacks. In both types of attacks, a cybercriminal impersonates a trustworthy person and tricks their target into revealing login credentials, installing malware, or making a wire transfer.
This is a summary of the similarities and differences between phishing and spear phishing.
Think of it this way:
- Phishing is like catching fish using a line — you cast your rod into the water and see what bites.
- With spear phishing, you choose the fish you want and aim the spear right at it.
This distinction is a crucial one, affecting how you detect, mitigate, and prevent both types of attacks.
What is phishing?
As we explained in our article “What Is Phishing?,” the term “phishing” can mean two things:
- An umbrella term covering many types of cyberattacks
- A specific type of cyberattack: an untargeted social engineering attack, conducted via email
In the first instance, “phishing” can refer to cyberattacks including:
- Business Email Compromise: A phishing attack utilizing an impersonated, spoofed, or hacked business email address
- Wire transfer phishing: A phishing attack that attempts to trick the target into making a fraudulent transfer to the attacker
- Smishing: Phishing via SMS
- Vishing: Phishing via voice, e.g., phone or VoIP software
In the second, specific sense, phishing means a social engineering attack (conducted via email) with no specific target. We sometimes call this “spray-and-pray” phishing. The cybercriminal sends as many emails as they can in the hope that someone falls for their scam. But don’t be fooled: phishing attacks aren’t necessarily amateurish operations.
What is spear phishing?
Spear phishing is a targeted phishing attack. The target receives an email that addresses them directly — by name.
Any type of targeted phishing attack is a “spear phishing” attack, including:
- Whaling: A spear phishing attack targeting company executive
- CEO fraud: A spear phishing attack where the fraudster impersonates a company’s CEO and targets another of the company’s employees.
But spear phishing is broader than this: if a Business Email Compromise attack, wire transfer phishing attack — or any other type of phishing attack — targets a specific individual, it’s a spear phishing attack.
Looking for more information about spear phishing? Check out this article: What is Spear Phishing? Targeted Phishing Attacks Explained.
Phishing vs. spear phishing examples
Now we’re going to look at some phishing attacks and spear phishing attacks side-by-side so you can understand the differences.
The two emails below demonstrate the essential difference between phishing and spear phishing:
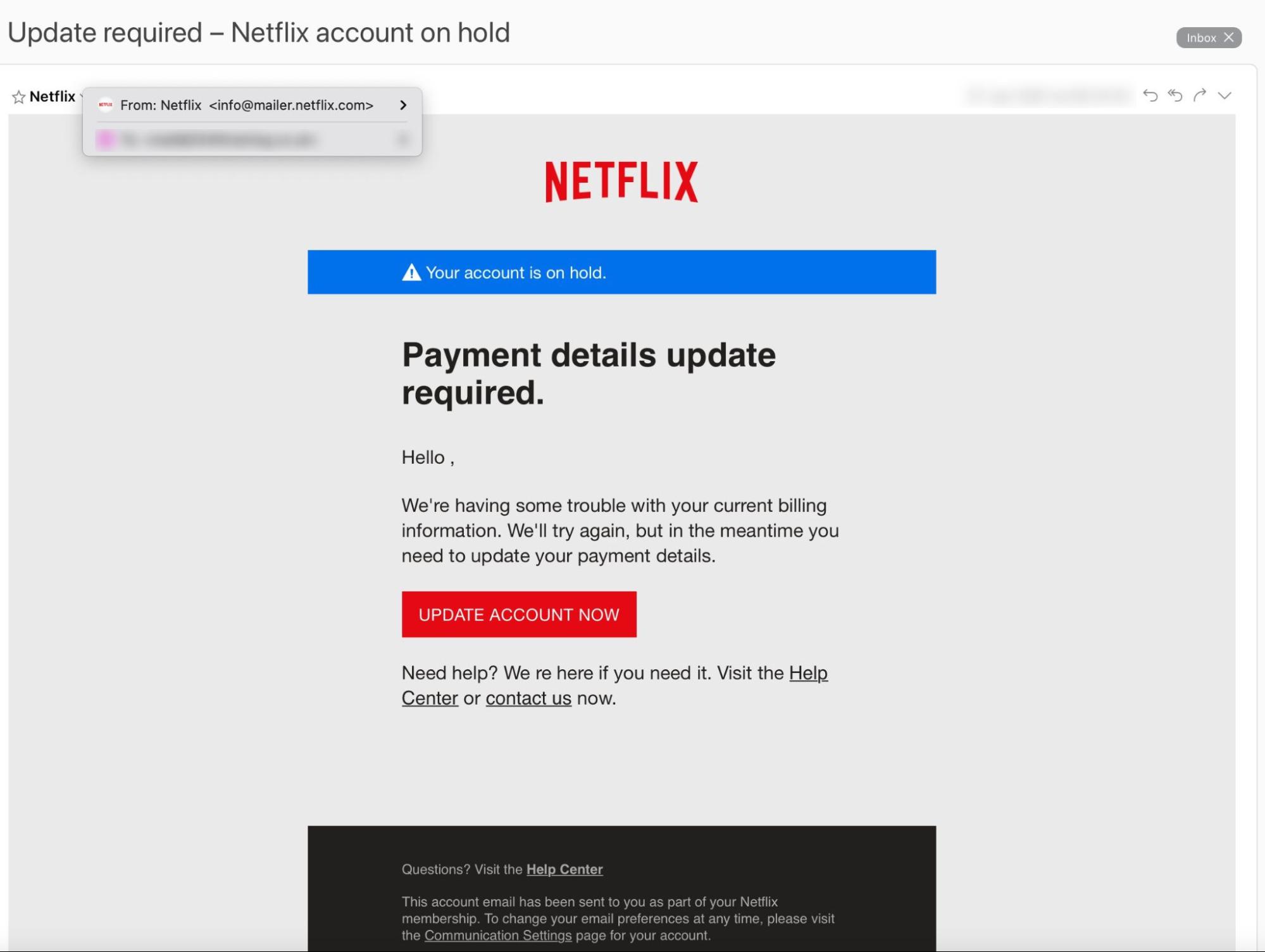
This is an example of a bulk phishing email. In this case, the attacker is impersonating Netflix.
This is an example of a “bulk” phishing email. It doesn’t address the target by name and doesn’t contain any personal information. But, because it appears to come from a trusted brand (Netflix) someone is likely to click the link.
This is an example of a targeted spear phishing attack. In this case, the attacker is impersonating the target's colleague.
This is an example of a spear phishing email: CEO fraud, to be precise. The attacker has exploited a professional relationship to elicit feelings of urgency and trust — the CEO urgently needs a favor and requests an employee to pay an invoice to an unknown account. But the “CEO” is a cybercriminal who controls the “new account.”
These examples should help you better understand the difference between phishing and spear phishing:
- Phishing succeeds by sheer volume: send a fraudulent email out to enough people and someone will fall for it eventually.
- Spear phishing succeeds through more sophisticated methods: send one fraudulent email containing personal information to a specific individual.
Looking for more resources?
We explore phishing, spear phishing, and other social engineering attacks in greater detail in the following articles:
- Phishing 101: What is Phishing?
- What is Spear Phishing? Targeted Phishing Attacks Explained
- Spear Phishing Examples: Real Examples of Email Attacks
- How to Hack a Human: How Attackers Use Social Media to Craft Targeted Spear Phishing Campaigns