The saying goes that your organization is only as strong as its weakest link. When it comes to cybersecurity, that weakest link could be an individual who inadvertently responds to a phishing email and exposes sensitive data to hackers. That’s why finding the weakest link within your organization and strengthening it is a top priority for IT leaders and CISOs.
One of the most widespread methods of testing employees’ cybersecurity awareness is through phishing tests. However, these tests have gained some notoriety in recent years and are seen by many as punitive and ultimately ineffective. In this article, we take a look at the different types of phishing test used by organizations and explore best practice in how to conduct them. We ask whether phishing tests are the most appropriate way to identify cybersecurity weaknesses and educate your workforce – and offer an alternative solution.
What are phishing tests?
Phishing tests are used by IT teams to assess the cybersecurity awareness of employees. Mock phishing emails or webpages are created by the IT team and sent out to employees. They are intended to look like genuine emails, just like phishing emails sent by hackers. The hope is that employees will identify something suspicious about the email and report it. IT teams collect information about which employees report the suspicious emails and which open the email and click on the links or attachments within them.
What is the purpose of phishing tests?
The aim of phishing tests is to help employees understand the different ways phishing attacks may be conducted, so they learn to identify suspicious features and avoid clicking on malicious links.
The results of phishing tests help IT teams to understand the level of cybersecurity resilience within their organization. They help to identify individuals that could benefit from further cybersecurity training.
IT teams can use phishing tests to measure improvements in cybersecurity resilience over time. Initial tests can provide a baseline figure for the percentage of employees that were successfully phished, against which the results from further phishing tests can be measured. This enables IT teams to track improvements in phishing email detection, following cybersecurity training or other interventions.
What are the types of phishing test?
- Phishing link tests: This type of test involves an email with a misleading link. In a real phishing attack, this link would lead to a malicious website, but in a phishing test it leads to a secure landing page, which records the action and informs the user that they have clicked on a potentially malicious link. It may direct them to further training at this stage. Similarly, emails with suspicious attachments can also be sent, to see which employees click on these potentially insecure files.
- Data entry tests: These tests may trick users into entering sensitive information into an online form or website. A phishing test email will be sent, which directs the user to a website page designed to look like a genuine data entry form or login page.
- Reply-To-Test: This test prompts users to reply to the phishing email. In a real phishingattack, replying to the email could provide an entry point for the hacker.
- Spear phishing: This is an emerging tactic used by cyber criminals, who impersonate a trusted source within an organization, such as a senior director, to target employees within the company. Employees are much more likely to trust an email that appears to come from a director within their company, making spear phishing a particularly difficult fraud to detect. Organizations can simulate spear phishing emails to help raise awareness of the issue among employees, encouraging them to be even more vigilant.
How to design and conduct effective phishing tests
Ideally, phishing tests should be conducted as part of a structured campaign, so you can gauge the success of any training interventions and measure improvements in the security culture of your organization over time.
Your phishing test campaign should progress in terms of difficulty, and mix up the various types of phishing attack mentioned above. The first phishing emails should be relatively simple for employees to identify. Subsequent phishing tests should increase in subtlety and complexity, testing the ability of employees to identify potentially malicious emails. Phishing tests should target people at all levels of the organization, so that no particular group feels unfairly targeted.
Before your phishing test campaign begins, you should notify employees that you will be carrying out these tests, without giving away any timings. You want people to feel that these tests are for the benefit of the whole business, and that each individual has a key role to play in protecting the organization from cyber-attacks. You don’t want people to feel that you’re trying to catch them out, so ensure you provide good initial training in how to spot suspicious emails and the various phishing techniques used by hackers.
Analyzing phishing test results
Your initial phishing test will provide baseline figures for the number of employees that fail to detect the potential threat. In analyzing the results, you need to collate figures on the number of employees that click on the bogus links and the number who report the phishing email.
Your aim is to increase the number of employees who report the fake attack. You can do this by running training programs for those who don’t detect the phishing emails, as well as rewarding those who do. As you provide the training required, you should see an improvement in detection rates over the course of your phishing test campaign.
What are the problems associated with phishing tests?
Phishing tests have begun to attract some criticism, following a number of high-profile examples of bad practice. You must always bear in mind that the aim of these tests is to help educate employees and bring them onside in your efforts to combat cybercrime. All too often, phishing tests adopt a ‘gotcha’ approach, followed by what is perceived as punishment training for those caught out.
One high-profile example from website hosting company GoDaddy in 2021 saw the company send an email to 500 employees offering a $650 holiday bonus. Those who clicked on the link were rewarded not with a bonus, but with a dose of cybersecurity training. This type of phishing test seems designed simply to catch people out.
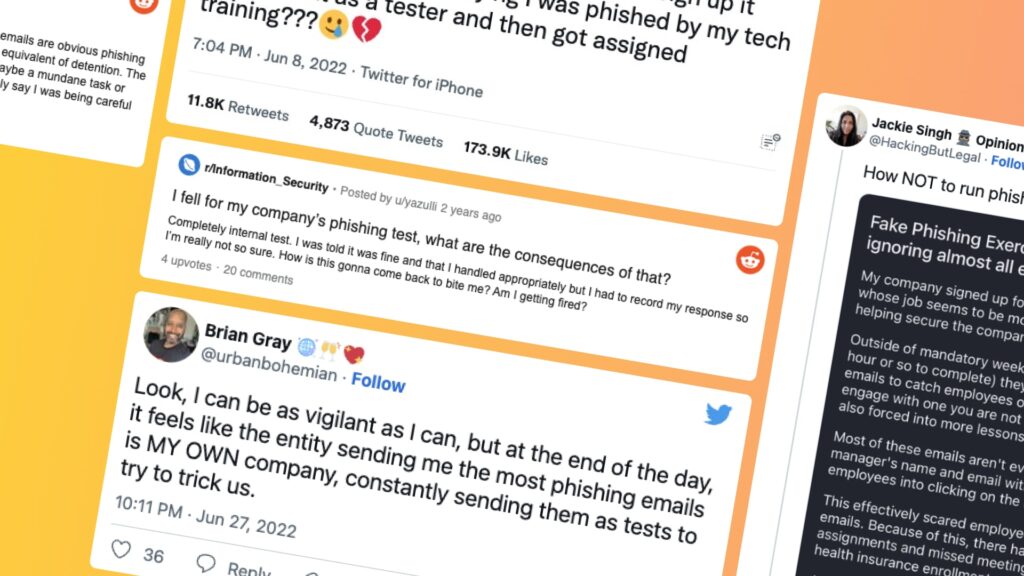
It’s easy to see how this can have a detrimental impact on employee morale, rather than helping to foster a strong security culture. Our recent Security Cultures Report found that only 33% of respondents have had a positive experience with phishing simulations, and 18-24 year olds are up to three times as likely to have had a bad experience. So when we saw this tweet, we were hardly surprised.
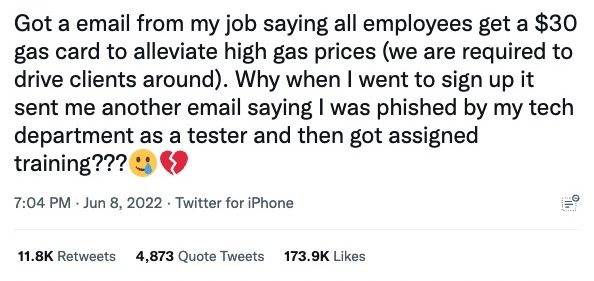
This is a classic example of a dysfunctional security culture. The result is fear and paralysis in the workforce that could affect people’s ability to do their work.
Thanks to research by Dr. Karen Renaud and Dr. Marc Dupuis we know that unleashing fear, uncertainty and doubt on a workforce doesn’t work. It cripples decision making, creative thought processes and the speed and agility businesses need to operate in today’s demanding world.
What are the most ethical and appropriate ways to use phishing tests?
As we’ve discussed before, it’s extremely difficult to stop people clicking on links in emails – because responding quickly to emails is simply part of their job. Most employees’ in-boxes are a revolving door of links to documents, webpages, forms, and databases. Weeding out the malicious emails from this avalanche of messages is no easy feat.
When done properly, phishing tests can be a powerful tool in building your security culture. They can offer valuable research insights and data to help your organization improve its suite of security measures. We believe phishing tests should be used as an opportunity to better tune your organization’s cybersecurity filters and defenses, not to single out individuals for further training.
That’s because, in reality, a user failure is really a technical failure in your organization’s security defenses. With the proper IT security systems in place, those phishing emails should never get through to employees in the first place. Blaming busy employees for clicking on malicious links is really just passing the buck.
What are the alternatives to phishing tests?
How did you learn to swim? You probably didn’t sit through an hour-long presentation about it, watch a video, then do a ‘fun’ quiz. You got in the water and worked things out ‘in the moment’. Your senses and instincts flagged potential dangers like getting out of your depth or diving too deep. Good security training is the same.
Training people away from their day-to-day working environment removes the connection between the danger, and where that danger is experienced. When Tessian detects a threat, like a spear-phishing email, it generates a security warning message that the recipient has to respond to. It’s written in plain English and explains why the email was flagged.
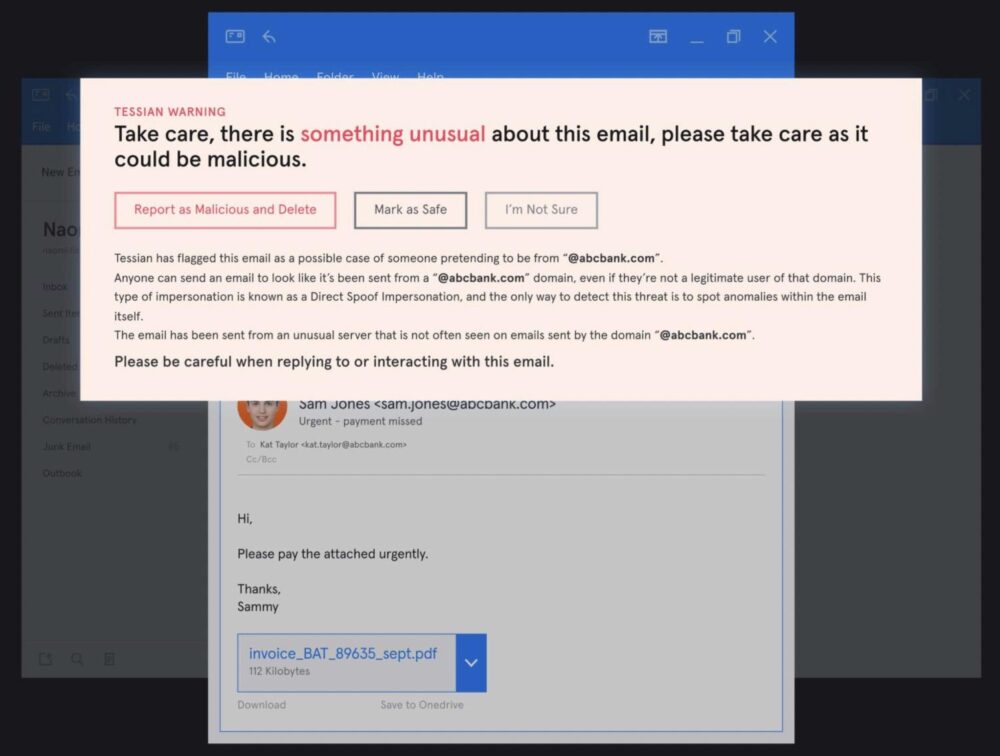
This type of in-the-moment training offers a far more user-friendly way to improve cybersecurity resilience than trying to catch employees out with phishing tests. It enables employees to learn as they work and raises awareness of the risks that may be lurking in their inbox.
Building a robust cybersecurity culture
It takes time and effort to develop a robust security culture that everyone subscribes to. It’s hard work for IT teams who are fighting many other issues and problems. But, according to our research, security leaders underestimate just how much they should be a part of the employee experience.
IT leaders need all the help they can get when it comes to getting employees on board in their efforts to combat cyber-crime. That’s why in-the-moment cybersecurity training can play such an important role in progressively enhancing your organization’s cyber defenses from within.
Our 2022 Security Culture Report is a good place to start your journey to a stronger security culture. Download it here.