Tessian Blog
Subscribe to our blog
Industry insights, straight to your inbox every week
- All Categories
- ...
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email Security451 Research: Tessian Uses Machine Learning for Better DLP
-
Life at Tessian
Our Journey To Revamp The Tessian Values
-
Advanced Email Threats
Phishing in Retail: Cybercriminals Follow The Money
-
Advanced Email Threats
How to Avoid the PPP Scams Targeting Small Businesses
-
 Cyber Skills Gap
Cyber Skills Gap3 Reasons Hackers Could Help Bridge the Cybersecurity Skills Gap
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityEd Bishop Joins SecureWorld “Emerging Threats” Panel
-
 Email DLP
Email DLPThe Drawbacks of Traditional DLP on Email
-
Email DLP, Compliance
5 Things Every CISO Should Know About CCPA’s Impact on Their InfoSec Programs
-
 Customer Stories
Customer StoriesKeeping Sensitive Client Data Safe
-
 Email DLP
Email DLPHow to Communicate Cybersecurity ROI to Your CEO
-
 Advanced Email Threats
Advanced Email ThreatsSpotting the Stimulus Check Scams
-
 Remote Working
Remote WorkingRemote Worker’s Guide To: BYOD Policies
-
Remote Working
Advice from Security Leaders for Security Leaders: How to Navigate New Remote-Working Challenges
-
 Remote Working
Remote WorkingRemote Worker’s Guide To: Preventing Data Loss
-
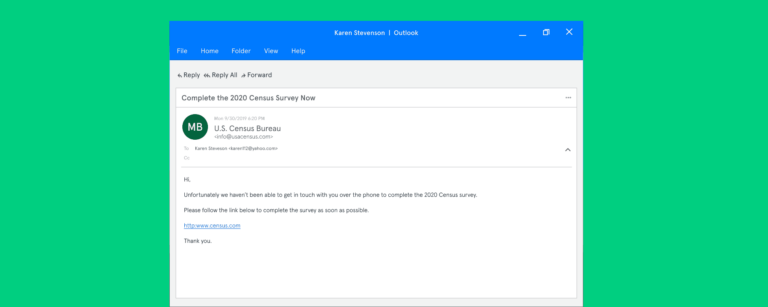 Advanced Email Threats
Advanced Email ThreatsHow to Spot and Avoid 2020 Census Scams
-
Cyber Skills Gap
Key Takeaways from Tessian’s Cybersecurity Skills Gap Webinar
-
 Remote Working
Remote WorkingUltimate Guide to Staying Secure While Working Remotely
-
 Integrated Cloud Email Security
Integrated Cloud Email Security5 Key Takeaways Tessian’s VentureBeat Webinar
-
Integrated Cloud Email Security, Email DLP, Insider Risks
How Can Organizations Empower People to Prevent Data Exfiltration?
-
 Remote Working
Remote Working11 Tools to Help You Stay Secure and Productive While Working Remotely







