Tessian Blog
Subscribe to our blog
Industry insights, straight to your inbox every week
- All Categories
- ...
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsTim Sadler on Hacking Humans Podcast: Ep 117 “It’s Human Nature”
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityHuman Layer Security Summit On-Demand: 5 Sessions to Watch Now
-
 Email DLP, Advanced Email Threats, Insider Risks, Compliance
Email DLP, Advanced Email Threats, Insider Risks, ComplianceCompliance in the Legal Sector: Laws & How to Comply
-
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks, Compliance, Customer Stories
18 Actionable Insights From Tessian Human Layer Security Summit
-
Advanced Email Threats
Why We Click: The Psychology Behind Phishing Scams and How to Avoid Being Hacked
-
 Email DLP, Compliance
Email DLP, ComplianceUltimate Guide to The POPIA – South Africa’s Privacy Law
-
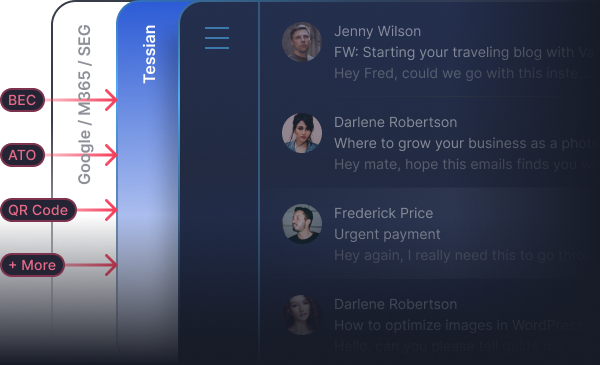 Compliance
ComplianceSecurity vs. Compliance: What’s The Difference?
-
Advanced Email Threats
How to Avoid Falling Victim to Voting Scams in the 2020 U.S. Election
-
Email DLP, Advanced Email Threats, Insider Risks, Compliance
August Cybersecurity News Roundup
-
Life at Tessian, Integrated Cloud Email Security
Why Customer Centricity is So Important At Tessian
-
Integrated Cloud Email Security, Email DLP, Customer Stories
9 Questions That Will Help You Choose The Right Email Security Solution
-
Integrated Cloud Email Security
8 Reasons To Register Now For Tessian Human Layer Security Summit
-
Advanced Email Threats
What is Social Engineering? 4 Types of Attacks
-
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Research Shows Employee Burnout Could Cause Your Next Data Breach
-
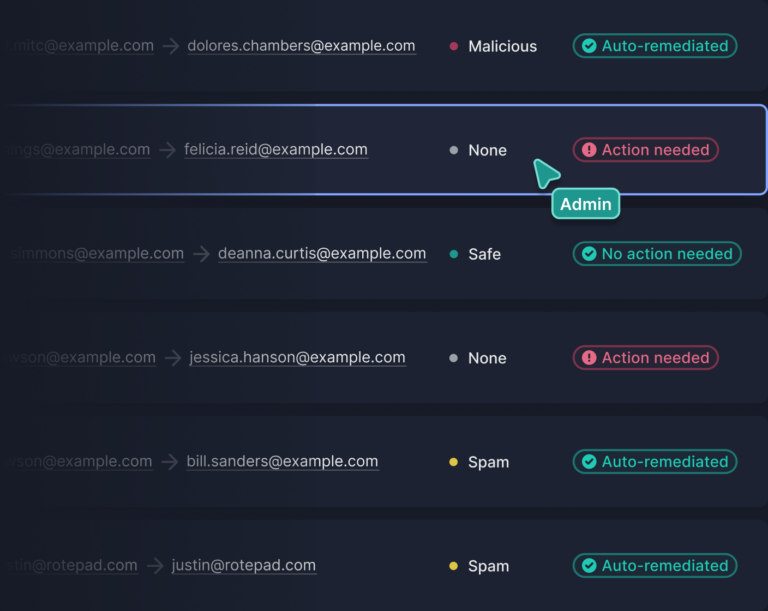 Integrated Cloud Email Security, Email DLP, Customer Stories
Integrated Cloud Email Security, Email DLP, Customer StoriesData Leakage and Exfiltration: 7 Problems Tessian Helps Solve
-
Compliance
Ultimate Guide to Data Protection and Compliance in Financial Services
-
Email DLP, Advanced Email Threats, Compliance
July Cybersecurity News Roundup
-
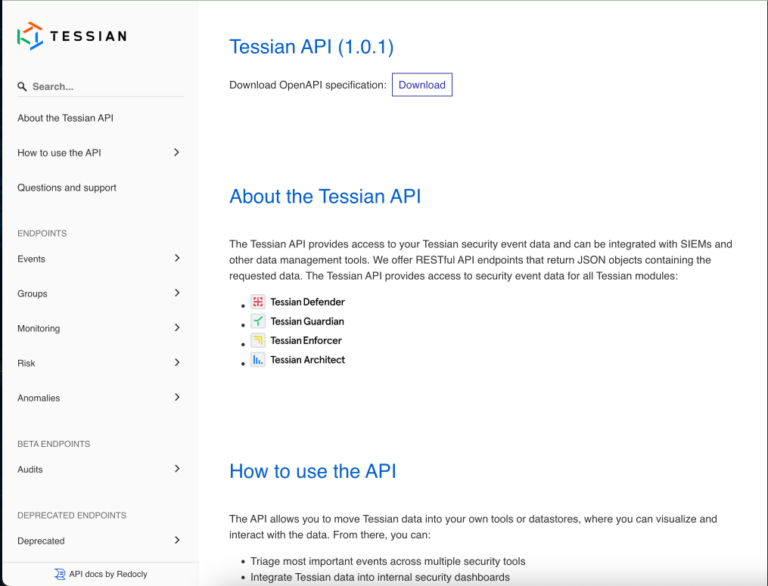 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider RisksResearch Shows How To Prevent Mistakes Before They Become Breaches
-
 Life at Tessian
Life at TessianOur First Growth Framework – How Did We Get Here?
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsWhy Political Campaigns Need Chief Information Security Officers







