Tessian Blog
Subscribe to our blog
Industry insights, straight to your inbox every week
- All Categories
- ...
-
 Life at Tessian
Life at TessianLessons Learned From Raising Our Series C Via Zoom
-
 Remote Working
Remote Working5 Reasons to Download Our Back to Work Security Behaviors Report
-
 Threat Stories
Threat StoriesUS Legal Education Provider Spam Campaign Detected
-
 Customer Stories
Customer StoriesAdvanced Inbound and Outbound Threat Protection for an International Law Firm
-
 Life at Tessian
Life at TessianThe Rise Of The New-School CISO
-
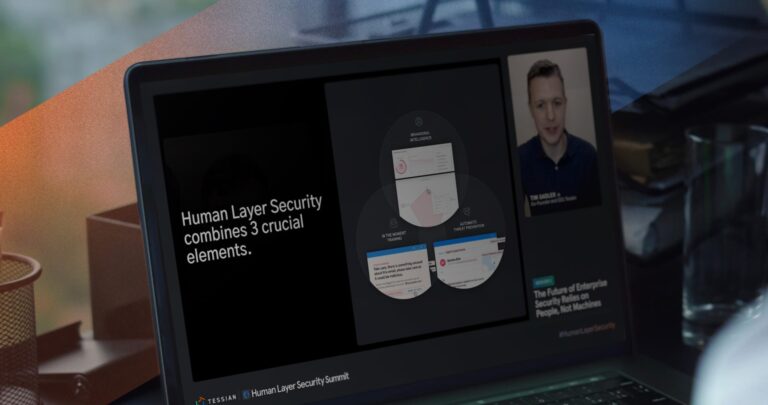 Integrated Cloud Email Security
Integrated Cloud Email Security6 Insights From Tessian Human Layer Security Summit
-
 Engineering Blog
Engineering BlogAfter 18 Months of Engineering OKRs, What Have We Learned?
-
 Life at Tessian
Life at TessianBuilding a Customer Success Team: 5 Pillars of Success
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsIs Your Office 365 Email Secure?
-
 Integrated Cloud Email Security, Email DLP, Compliance
Integrated Cloud Email Security, Email DLP, ComplianceAt a Glance: Data Loss Prevention in Healthcare
-
 Integrated Cloud Email Security, Life at Tessian
Integrated Cloud Email Security, Life at TessianAnnouncing our $65M Series C led by March Capital
-
 Threat Stories
Threat StoriesAnalysis of Executive Impersonation Burst Attack
-
 Engineering Blog
Engineering BlogTessian’s Client Side Integrations QA Journey – Part I
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityJune Human Layer Security Summit: Meet the Speakers
-
 Engineering Blog
Engineering BlogHow Do You Encrypt PySpark Exceptions?
-
 Integrated Cloud Email Security, Advanced Email Threats, Customer Stories
Integrated Cloud Email Security, Advanced Email Threats, Customer StoriesHow Tessian Reduced Click-Through Rates on Phishing Emails From 20% to Less Than 5%
-
 Life at Tessian
Life at TessianWhy We’re Logging Off at Lunchtime This Summer
-
 Compliance
ComplianceWhy Information Security Must Be a Priority For GCs in 2021
-
Email DLP, Integrated Cloud Email Security, Insider Risks, Compliance
The State of Data Loss Prevention in the Financial Services Sector
-
 Advanced Email Threats, Threat Stories
Advanced Email Threats, Threat StoriesHow Cybercriminals Exploited The Covid-19 Vaccine Roll-Out







