Tessian Blog
Subscribe to our blog
Industry insights, straight to your inbox every week
- All Categories
- ...
-
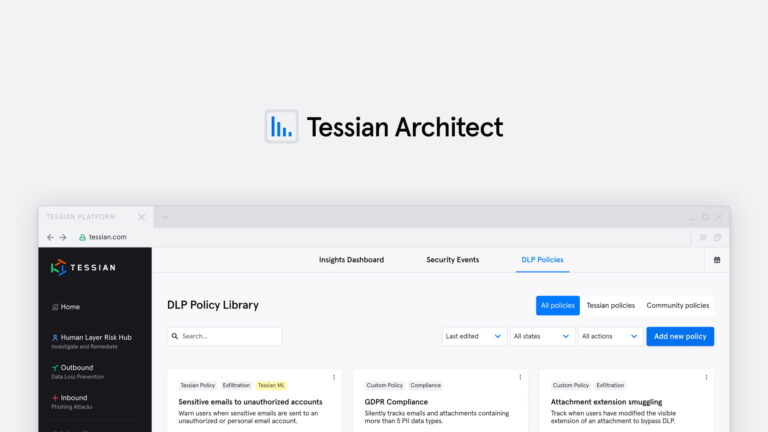 Email DLP
Email DLPIntroducing Tessian Architect: The Industry’s Only Intelligent Data Loss Prevention Policy Engine
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityNew Technology Integration: Sumo Logic Tessian App
-
 Email DLP, Integrated Cloud Email Security, Insider Risks, Compliance
Email DLP, Integrated Cloud Email Security, Insider Risks, ComplianceYou Sent an Email to the Wrong Person. Now What?
-
 Engineering Blog
Engineering BlogA Solution to HTTP 502 Errors with AWS ALB
-
 Life at Tessian
Life at TessianTessian Officially Named a 2021 UK’s Best Workplace™ in Tech
-
 Email DLP, Customer Stories
Email DLP, Customer StoriesCustomer Story: How Tessian Helped a Private Equity Firm Achieve Threat Visibility Through A Platform Approach
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsNew ESG Report Highlights Gaps in M365 Native Security Tools
-
 Advanced Email Threats
Advanced Email ThreatsWe Analyzed 2 Million Malicious Emails. Here’s What We Learned.
-
 Life at Tessian
Life at Tessian200 Reasons to Love Tessian
-
 Email DLP, Customer Stories
Email DLP, Customer StoriesCustomer Story: How Tessian Combines Data Loss Prevention With Education in Financial Services
-
 Advanced Email Threats
Advanced Email ThreatsWhat is a Software Supply Chain Attack?
-
 Advanced Email Threats
Advanced Email ThreatsWhat Does a Spear Phishing Email Look Like?
-
 Email DLP
Email DLPHow to Close Critical Data Loss Prevention (DLP) Gaps in Microsoft 365
-
 Integrated Cloud Email Security, Email DLP
Integrated Cloud Email Security, Email DLPLegacy Data Loss Prevention vs. Human Layer Security
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsLegacy Phishing Prevention Solutions vs. Human Layer Security
-
 Email DLP, Advanced Email Threats, Compliance
Email DLP, Advanced Email Threats, Compliance5 Cyber Risks In Manufacturing Supply Chains
-
 Compliance
ComplianceNIST Cybersecurity Framework and Email Security
-
 Integrated Cloud Email Security
Integrated Cloud Email SecurityTessian Partners with Optiv Security and Moves to a 100% Channel Model
-
 Advanced Email Threats
Advanced Email ThreatsPhishing vs Spear Phishing: Phishing and Spear Phishing Examples
-
 Email DLP, Integrated Cloud Email Security
Email DLP, Integrated Cloud Email SecurityWhat is Email DLP? Overview of DLP on Email







