The cost of a data breach is up 13% from 2020 totalling $4.35 million, according to IBM’s Cost of a Data Breach Report for 2022. IBM’s annual report also revealed that compromised credentials, phishing and cloud misconfiguration are the top three attack vectors. Phishing related breaches is the costliest form of attack, costing businesses $4.91 million in damages per breach.
IBM recommends investing in security tools that leverage artificial intelligence (AI) and machine learning. These next generation security tools represent the biggest breach cost mitigation measure organizations can take, reducing the overall cost of a breach by an average of $3.05 million.
Keep reading for key findings from the report.
Key findings
- The cost of a breach continues to creep up year-over-year. The cost of a breach has increased to $4.35m in 2022 – representing a nearly 13% increase from 2020.
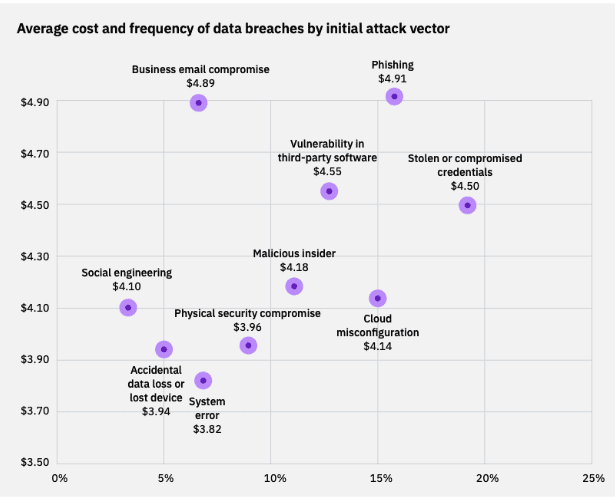
- Top 3 attack vectors were identified as: compromised credentials (19%), phishing (16%) and cloud misconfiguration (15%).
- Phishing is the costliest form of a breach. Although compromised credentials is the leading cause of a breach, phishing is the costliest with the fallout averaging $4.91m per breach.
- Business Email Compromise (BEC) is expensive. BEC attacks are the second costliest, totalling on average $4.89m per breach.
“Phishing is the costliest form of attack in the modern enterprise, costing businesses $4.91 million in damages per breach. ”
IBM Cost of a Data Breach Report 2022
- Healthcare remains the most adversely impacted vertical. Costs of healthcare breaches have reached a record high of $10.1m. According to HIPAA, there were over 680,000 healthcare breaches in 2021, resulting in close to 45 million healthcare records being compromised.
- Million dollar savings. Investing in security AI and machine learning tools is the greatest breach cost mitigation organizations can take, reducing the overall cost of a breach by an average of $3.05m compared to organizations that do not have these tools in place.
- The increasing frequency and costs associated with breaches is adding to inflationary pressure for goods and services. Companies that have suffered a breach are typically raising their prices for goods and services.
- Breaches are still taking an inordinate amount of time to contain. On average breaches are resolved within 277 days from discovery.
- Paying ransoms does not lead to significant cost savings for victims of a breach. Those that chose to pay ransoms saw on average $610, 000 less in breach costs than those that chose not to pay.
- Critical infrastructure remains vulnerable and lags in zero trust adoption. 80% of critical infrastructure organizations have not adopted zero trust strategies. The result is +$1m more costly breaches, totalling an average of $5.4m per breach.
The importance of cloud adoption maturity and cloud security
- Hybrid cloud represents a hedge against cyber risk. The study found hybrid cloud adopters discovered breaches 15 days sooner than companies that relied solely on a single public or private cloud operating model.
- Hybrid cloud reduces breach cost. Companies that rely on a hybrid cloud operating model also experienced the lowest costs associated with a breach. On average breach costs for hybrid cloud adopters were $3.8 million.
- Cloud security adoption is lagging breaches. Almost half (45%) of all breaches originated in cloud environments, with 43% of organizations stating that they are only in the early stages of implementing security across their cloud environments.
- A lack of cloud security adoption increases time to resolve a breach. On average organizations that failed to adopt adequate or any cloud security for their cloud environments required +108 days to resolve a breach.
Phishing and Business Email Compromise (BEC) are the costliest attack vectors
- BEC and credential compromise breaches are insidious and difficult to discover. Email breaches have the second highest mean time to discovery at 308 days (+16% on the overall mean time), with compromised credentials topping the list with a mean time for discovery 327 days (+19%).
- Phishing is a lucrative scam. Phishing is the second leading attack vector for breaches (16%), and is also the costliest at $4.91m. BEC attacks come a close second, costing businesses $4.89m.
Source: IBM Cost of a Data Breach 2022
Recommendations
Some of the key IBM recommendations include:
- Adopt a zero trust security strategy and security model. Zero trust is particularly well-suited to hybrid cloud environments and hybrid and remote work operating models, protecting data by limiting accessibility and requiring context to grant access.
- Adopt security tools that can share and centralize data between disparate systems. Implement security tools that can centralize data security operations across multiple environments to enable security teams to detect incidents across complex hybrid multi-cloud environments.
- Invest in cloud native security automation tools. This includes security orchestration, automation and response (SOAR), security information and event management (SIEM), managed detection and response (MDR) tools and XDR to accelerate incident response through automation.
- Use best-of-breed security tools that help protect and monitor endpoints and remote employees. Remote work related breaches cost an average of $1 million more than non-remote work breaches. Leveraging endpoint and end-user focussed security solutions including endpoint protection platforms (EPP), identity and access management (IAM) and email security solutions are essential.
- Create and test incident response plans and playbooks. This includes creating incident response teams that are well rehearsed on testing the IR plan. Additional measures include red teaming and finding solutions that manage attack surface risk.
To see how Tessian prevents ransomware attacks, and protects against DLP, watch a product overview video or book a demo.
For the latest cybersecurity news and articles, sign up for our newsletter, and follow us on Twitter and LinkedIn.