Cybersecurity attacks are increasing in volume and sophistication year-byon-year. As every CISO knows, email is the primary attack vector used by cyber criminals – being responsible for 96% of cybersecurity breaches. It means that protecting your organization against email-based attacks is a top priority for any IT leader.
Traditionally, in a world where most IT systems, including email servers, were hosted on premises, Secure Email Gateways (SEGs) were used to monitor incoming and outgoing emails and weed out fraudulent or malicious content. Today, in the work-from-anywhere era, organizations are increasingly moving to cloud-based email platforms, which need to be secured by a new generation of email protection software – known as Integrated Cloud Email Security (ICES) solutions.
To find out more about Secure Email Gateways and the emergence of Integrated Cloud Email Security (ICES), we caught up with Tessian Senior Sales Engineer, Tam Huynh. He knows more than most about the benefits and applications of these technologies, how they can be deployed in practice, and how they help organizations deal with today’s ever-changing email threat landscape.
What are the greatest email-based cybersecurity risks?
There are many ways for hackers to attack an organization’s data and systems via email. Some of these have been around for a long time, but are becoming more sophisticated every year, while others are brand-new.
-
Phishing attacks
Phishing has been around for almost as long as email itself. It involves a fraudster spamming users with emails, purporting to be from a reputable source, and encouraging the recipient to click on a link or visit a particular site. Phishing emails might offer a tempting prize or incentive, or they could threaten the recipient with account closure or financial penalties if they don’t click on the link to rectify an issue. Once the recipient clicks on the link, they are taken to a fake website and encouraged to share personal information, bank details, or reset passwords.
-
Ransomware attacks
A ransomware attack involves a hacker breaching your company’s security and restricting access to data or systems. The hacker then demands a ransom to be paid in order to lift the restriction. Ransomware attacks are often made through email, duping users into clicking on malicious links or opening an attachment that releases malware into the company’s computer network.
-
Zero-day attacks
This is a rapidly growing threat that targets previously unidentified vulnerabilities in a company’s software. Again, email is the attack vector, with zero-day malware entering a network via a breach in email security and stealing or damaging data from within an organization’s network. Because these attacks enter via a previously unknown vulnerability or gap in cyber defenses, the organization targeted has ‘zero days’ to patch the vulnerability and fix the problem. The only way to identify zero-day malware is to examine suspicious email and software activity.
What is a Secure Email Gateway?
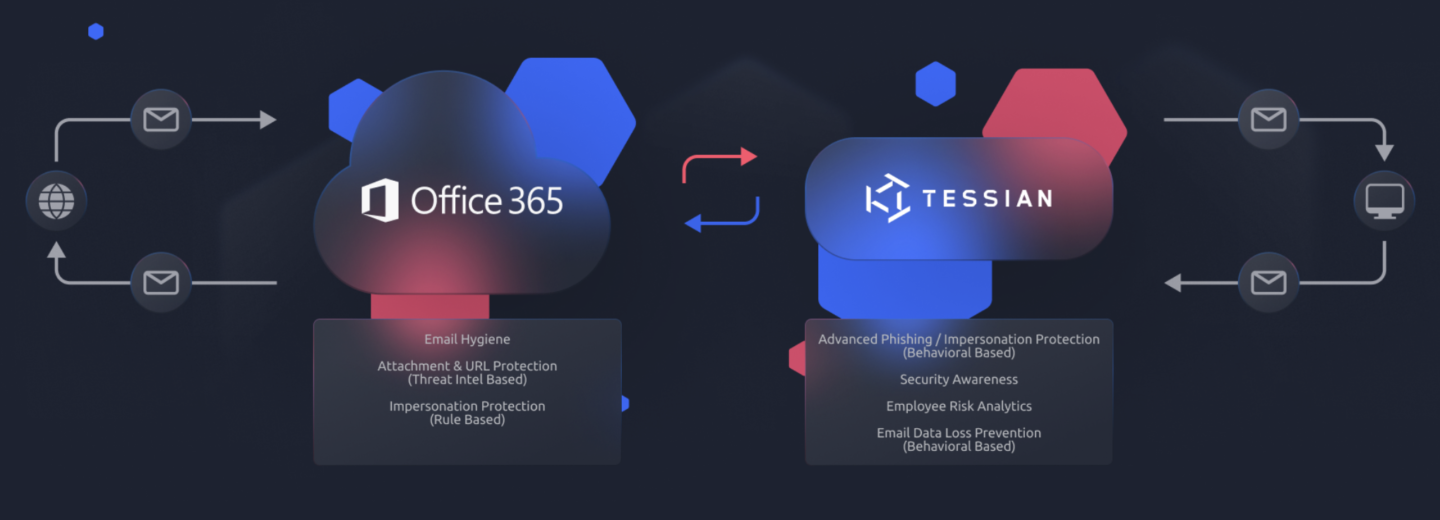
A Secure Email Gateway (SEG) is a technology solution designed to protect organizations from email-based threats and ensure a secure flow of email communications. Secure Email Gateways act as a filter between an organization’s internal email infrastructure and external email systems, such as the internet.
Secure Email Gateways are designed to prevent unwanted email entering a company’s IT environment, while ensuring good emails get through to the right recipients. SEGs help to detect spam, phishing attacks, malware, and fraudulent content, while outgoing messages can be analyzed to prevent sensitive data leaving the organization.
How do Secure Email Gateways work?
Originally developed in 2004 for on-premise email servers, SEGs use a rule-based approach to threat detection. They have ‘deny’ lists, ‘allow’ lists and signatures for message authentication to prevent attacks. That means they protect email systems against threats that are already known, using a reactive approach. However, this means that Secure Email Gateways can’t offer protection against zero-day attacks and are increasingly easy for attackers to evade using advanced social engineering campaigns.
Secure Email Gateways use an established dataset and static analysis to identify the threat signals in emails. However, SEGs have been found wanting when it comes to detecting business email compromise (BEC), account takeover (ATO) and advanced spear phishing attacks – because often there is no malicious payload associated with these emails.
Furthermore, the shift away from on-premise email platforms to cloud-based platforms presents new challenges in securing these cloud services against email-based attacks. Gartner estimates that 70% of organizations now use cloud productivity solutions like Microsoft 365 and Google Workspace. In this environment, IT leaders are increasingly turning away from SEGs and opting for new Integrated Cloud Email Security (ICES) solutions.
What is an Integrated Cloud Email Security (ICES) solution?
Integrated Cloud Email Security (ICES) solutions have been developed to provide the best defense against advanced email-based threats that evade traditional email security controls. ICES solutions are cloud-based and use application programming interfaces (APIs) to detect anomalies in emails, using advanced techniques such as natural language understanding (NLU), natural language processing (NLP) and image recognition. Using API access to the cloud email provider, these solutions have much faster deployment and time-to-value, and can analyze email content without the need to change the Mail Exchange (MX) record.
How long does it take to deploy an Integrated Cloud Email Security solution?
APIs enable advanced and intricate ICES solutions to be deployed to Microsoft 365 in around 20 minutes, depending on how quickly the administrator can get the author credentials. With the Tessian solution, users enter their credentials inside of our portal and grant permissions to the Tessian console, tell us which groups to sync, and they’re done.
If we look back a decade at how Secure Email Gateways were deployed, it could take well over a month or more of multiple-phase approaches, changing control windows, testing within a lab or a sandbox first, and then rolling the system out to production. ICES deployment is much faster.
How do ICES solutions work with existing tech stacks?
Our experience shows that many businesses are essentially replacing their Secure Email Gateways with ICES solutions. To enable this transition, we typically create a full feature map of the organization’s SEG, and then recommend a Microsoft 365 E5 license that enables them to use features such as sandboxing and behavioral analysis, as well as other features found in a SEG. Of course, organizations can choose to retain their Secure Email Gateway alongside Microsoft 365 E5.
For organizations not looking to move to Microsoft 365, who might have an on-premise exchange server, or are using G Suite, Tessian can leverage a gateway testing deployment, which means an installation time of around an hour. And that’s from start to finish. Either way, deploying via the APIs or gateway means no worrying about modifying MX records.
How should companies communicate ICES to the rest of the business?
As we’ve seen, ICES solutions can be deployed in under an hour, but that might come as quite a shock to other teams around the organization. So it’s vital to have a clear communication strategy for the business, alongside your technical deployment strategy.
You need to ensure that all relevant teams are aware of the change, well ahead of time, especially non-technical teams. Users will want to know if the change is going to affect any imminent sales. Does the Customer Success team need to inform customers? And don’t forget to let the leadership team know. Use the skills of your communications team to help get the information out to the wider organization, and have them on standby in the unlikely event that there is an issue with the deployment.
When is the best time to deploy an ICES?
Not at 5pm on the penultimate Thursday or Friday in the quarter when sales might be trying to hit target! The ideal time we’ve found with our customers is after business hours on a Monday. The email volume is low, so it won’t be noticed by most end users.
To find out more about Integrated Cloud Email Security and how it can protect your business from the latest email-based cybersecurity threats, please read our Buyers Guide to ICES or request a demo.
Andrew Webb
Senior Content Manager
















