There’s an (unfair!) perception in the industry that most CISOs are skeptical, or at least conservative, when it comes to adopting the latest security technology.
But the role of the CISO is evolving. It’s no longer to simply “own” risk. Today, they’re also tasked with educating and informing everybody within the company – including the C-Suite – on the risks and what can be done to mitigate them.
In this fast moving world, it’s no longer possible to be passive. Only those who are open-minded (and ideally progressive) will protect their company from the most advanced threats.
A year of firsts
The security industry is moving in a different direction. We need only look back at the last 12 months to see why:
- COVID has raised the profile for security. A greater attack profile has caught the attention of executive teams, and they are looking to CISOs to respond. But, it’s not all bad news. Just as cybercriminals see opportunity in disruption, CISOs have an opportunity to play a bigger role at the executive level.
- The digital transformation has been accelerated. The shift to remote working means an increased attack surface. Today, security teams must support whole departments of remote workers as they engage with technology in their kitchens, bedrooms, and coffee shops. CISOs need to do more than send the occasional email or facilitate annual training to raise awareness about cyber threats.
- Ransomware is an ever-growing threat. In fact, almost a third of victims pay a ransom, which means the stakes are higher than ever. Attackers have improved the implementation of their encryption schemes, making them harder to crack. And, rather than simply encrypting critical data, some criminals now steal sensitive data and threaten to release it if the ransom is not paid.
With so much changing, CISOs have to adapt fast and adopt new technology to succeed. Gartner calls this period of early adoption a “hype cycle”. And, for any new innovation, early publicity produces a number of success stories — often accompanied by scores of failures. Some companies take action; many do not.
Where do you stand?
The technology balance
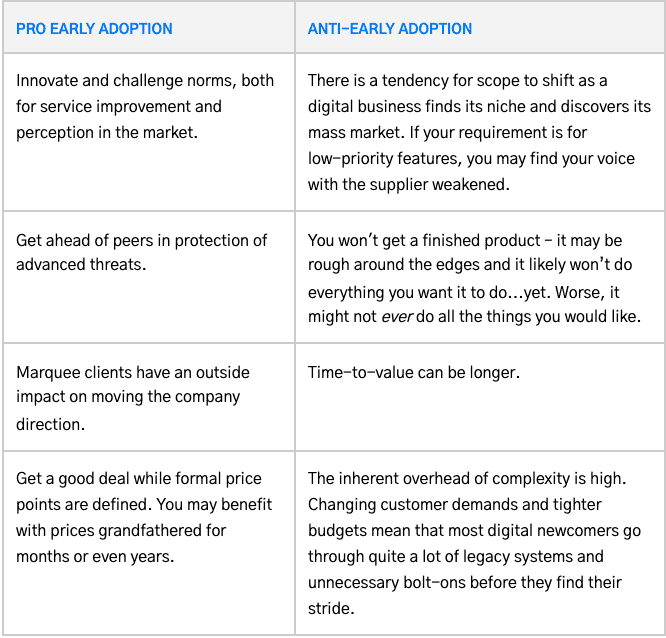
Both inside and outside of security, there are plenty of arguments both for and against new technologies:
Given the rapidly evolving threat landscape, though, CISOs should be pushed harder than most to commit fully to the leading edge of security innovation. After all, “nobody got fired for buying IBM” and “fortune favors the brave“, right?
The next generation of security
More and more CISOs are choosing to be brave. Why? It comes down to the modern way this next generation of security is being designed and built.
Today’s security benefits are focused on cutting the risk out of early participation while amplifying the benefits. At the heart of the change are two related trends:
- Next-generation security services
- The advancement of machine learning
The next generation of security services has removed the need for CISOs to be experts on negotiating IT project. Instead, they can focus on managing the risks to their business.
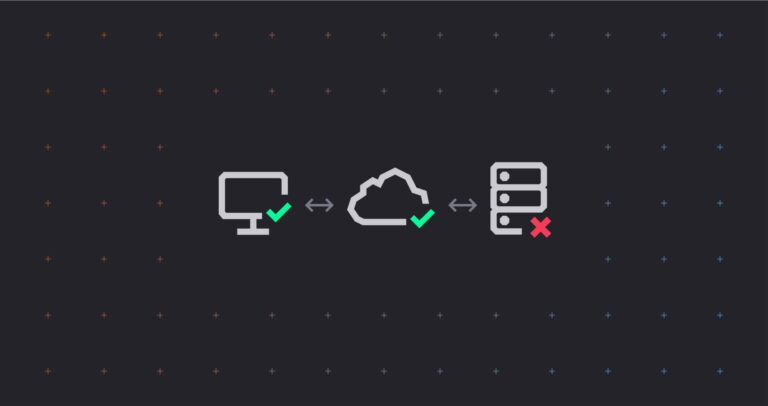
For example, with cloud services, the costs of infrastructure – and efforts of supporting it – are completely removed as the services you buy are scalable to match the business. Cloud services also require no maintenance or professional assistance beyond an internet browser. The cloud means that the hurdles and expense associated with “trying out something new” are hugely mitigated.
And, because these next-gen security services are hosted on the cloud, you’ll always have the latest version. There is only one “copy” of these software tools. That means upgrade cycles have come down from once a year to multiple times a day. Better still, these services connect to one another. This equates to a shallower learning curve for users, faster time-to-market, and the flexibility to bolt on future tools that suit the way you want to run your operation.
“The benefit for CISOs - and their security teams - is clear. Lower time commitment to identify and remediate issues and more accurate reporting on the risks to the business.”
Legacy technology vs. machine learning
Whereas legacy technology uses rule-based techniques to secure organizational risks, new providers leverage machine learning to provide accurate, automatic protection, and visibility against advanced risks, otherwise impossible to detect with legacy systems.
Machine learning’s goal is to understand the structure of the data and fit theoretical distributions to that data that is well understood. And, because machine learning often uses an iterative approach to learn from data, the learning can be easily automated. Passes are run through the data until a robust pattern is found. In an ever-evolving security world, this allows for the identification of specific risks.
By using machine learning algorithms to build models that uncover these connections, organizations can make better decisions without human intervention. For example, identifying anomalous behaviors that form part of the most advanced threats in the enterprise.
The benefit for CISOs – and their security teams – is clear. Lower time commitment to identify and remediate issues and more accurate reporting on the risks to the business.
These next generation tools also achieve something legacy systems can’t and don’t: they share de-identified data between customers to ensure everyone is protected, even from threats that haven’t (yet) been seen in their own network. The benefit? Organizations continually – and automatically – improve their protection against an ever-changing threat environment.
Low risk, high reward
Finally, like never before – and because these services are in the cloud – security leaders are in a position to switch on new services at low risk, without any upfront investment.
With no upfront CapEx, chances are that your first steps will be below any procurement ceiling too – so PoCs become simple to execute. It becomes rational to test a service or strategy with a small team before rolling out more broadly.
And, because the barrier to try (and switch!) for these early adopters is so low, “try before you buy” is a prevalent trend. With low switching costs, the software developers behind the scenes have a wholehearted commitment to making the trial period compelling enough to convince you to take the next step. They have skin in the game and understand that happy customers dictate whether or not a product is successful.
This lowering of barriers, enabling of small-scale testing, and offsetting of cost should all make it a little more tempting for CISOs to take the leap and occasionally try for first-mover status. Because adopting innovative practices has never been so low-risk and the rewards are well-worth it.
To name a few… improving your security posture, reducing admin, and protecting your employees from ever-evolving threats.
Phil O'Hagan
Head of Customer Operations