CEO fraud is a type of cybercrime in which the attacker impersonates a CEO or other company executive. The fraudster will most often use the CEO’s email account — or an email address that looks very similar to the CEO’s — to trick an employee into revealing sensitive data or transferring money. A report by UK Finance suggests that CEO fraud is among the main eight types of fraud attacks targeting consumers and businesses.
Like all types of phishing, CEO fraud attacks are very difficult for employees to spot. Some legal technical solutions, such as Secure Email Gateways (SEGs) can also struggle to detect this increasingly sophisticated type of cybercrime. But, there are still ways to prevent successful CEO fraud attacks. The key? Take a more holistic approach by combining training, policies, and technology. We’ve outlined three techniques that are crucial to help your organization defend against CEO fraud and other related types of cybercrime.
1. Raise employee awareness
Security is everyone’s responsibility. That means everyone – regardless of department or role – must understand what CEO fraud looks like. Staff training is getting tougher as CEO fraud gets more sophisticated. The FBI’s Internet Crime Complaint Centre (IC3) warns that along with CEOs, cybercriminals increasingly impersonate a broad range of actors, including vendors, lawyers, and payroll departments. So where do you start when training employees to detect CEO fraud attacks? Using real-world examples to point out common red flags can help.
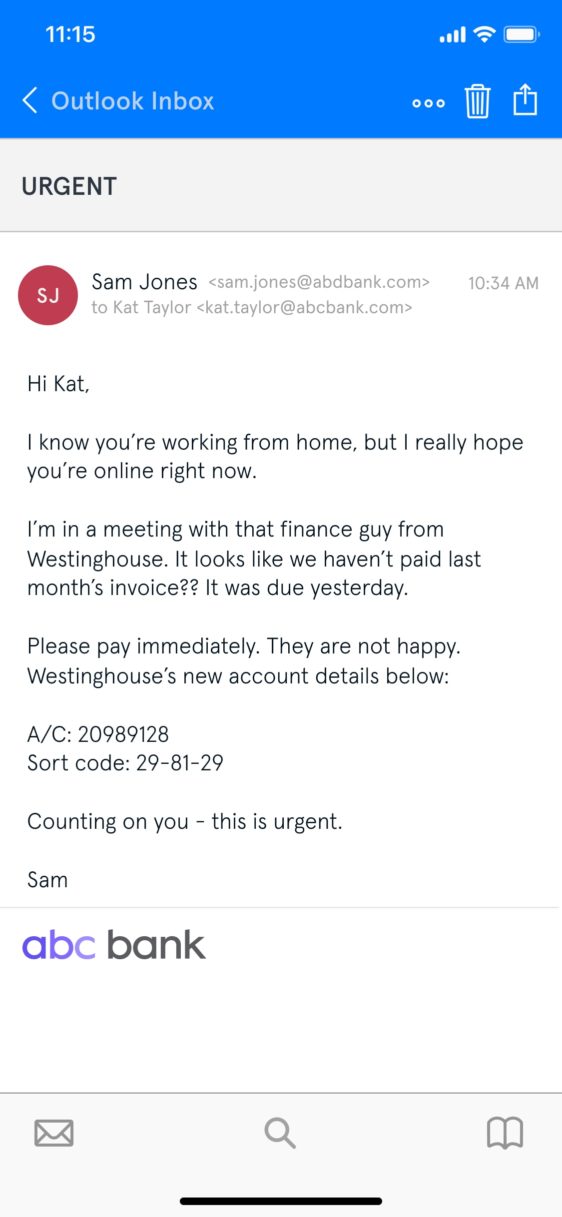
An example of CEO fraud that uses seniority and urgency to motivate the target to make a wire transfer.
What are the signs that this email is part of a CEO fraud attack? First off, note the lack of spelling errors. Poor spelling and grammar can be a phishing indicator, but this is increasingly unlikely in today’s more sophisticated cybercrime environment.
Also, notice the personal touches — Sam’s familiar tone, his references to Kat working from home, and his casual email sign-off. Fraudsters go to great efforts to research their subjects and their targets, whether via hacking or simply using publicly available information.
These persuasive elements aside, can you spot the red flags? Let’s break them down:
- The sender’s email address: The domain name is “abdbank.com” (which looks strikingly similar to abcbank.com, especially on mobile). Domain impersonation is a common tactic for CEO fraudsters.
- The sense of urgency: The subject line, the ongoing meeting, the late invoice—creating a sense of urgency is near-universal in social engineering attacks. Panicked people make poor decisions.
- The authoritative tone: “Please pay immediately”: there’s a reason cybercriminals impersonate CEOs — they’re powerful, and people tend to do what they say.
- Playing on the target’s trust: “I’m counting on you”. Everyone wants to be chosen to do the boss a favor.
- Westinghouse’s “new account details”: CEO fraud normally involves “wire transfer phishing”—this new account is controlled by the cybercriminals.
Your cybersecurity staff training program should educate employees on how to recognize CEO fraud, and what to do if they detect it.
- Check the sender’s email address for discrepancies. This is a dead giveaway of email impersonation. But remember that corporate email addresses can also be hacked or spoofed.
- Feeling pressured? Take a moment. Is this really something the CEO is likely to request so urgently?
- New account details? Always verify the payment. Don’t pay an invoice unless you know the money’s going to the right place.
Looking for a resource that you can share with your employees? We put together an infographic outlining how to spot a spear phishing email. While these are important lessons for your employees, there’s only so much you can achieve via staff training.
Take it from the U.K.’s National Cyber Security Centre (NCSC):“Spotting phishing emails is hard, and spear phishing is even harder to detect. Even experts from the NCSC struggle.The advice given in many training packages, based on standard warnings and signs, will help your users spot some phishing emails, but they cannot teach everyone to spot all phishing emails.”
Humans are often led by emotion, and they’re not good at spotting the small giveaways that might reveal a fraudulent email. Sometimes, even security experts can’t!
2. Implement best cybersecurity practice
Beyond staff training, every thriving company takes an all-around approach to cybersecurity that minimizes the risk of serious fallout from an attack. Many companies choose to implement a cybersecurity framework, such as the CIS Critical Security Controls or the NIST Cybersecurity Framework, to help them adopt security controls and protections in a systematic and comprehensive way.
Here are some important security measures that will help protect your company’s assets and data from CEO fraud:
- Put a system in place so employees can verify large and non-routine wire transfers, ideally via phone
- Protect corporate email accounts and devices using multi-factor authentication (MFA)
- Ensure employees maintain strong passwords and change them regularly
- Buy domains that are similar to your company’s brand name to prevent domain impersonation
- Regularly patch all software
- Closely monitor financial accounts for irregularities such as missing deposits
- Deploy an email security solution
All the above points are crucial cybersecurity controls. But let’s take a closer look at that final point — email security solutions.
3. Deploy intelligent inbound email security
CEO fraud attacks overwhelmingly take place via email (along with 96% of all phishing attacks). That’s why deploying an email security solution is one of the most effective steps you can take to prevent this type of cybercrime. But not just any email security solution.
Legacy solutions like Secure Email Gateways (SEGs), spam filters, and Microsoft and Google’s native tools generally can’t spot sophisticated attacks like CEO fraud. Why? Because they rely almost entirely on domain authentication and payload inspection. This means they tend to check publicly available records to verify the authenticity of an email address, and examine any attachments to see if they contain malware.
Social engineering attacks like CEO fraud easily evade these mechanisms. Tessian is different. Tessian Defender uses machine learning (ML), anomaly detection, behavioral analysis, and natural language processing (NLP) to detect a variety of signals indicative of CEO fraud.
- Tessian’s machine learning algorithms analyze your company’s email data. The software learns every employee’s normal communication patterns and maps their trusted email relationships — both inside and outside your organization.
- Tessian inspects both the content and metadata of inbound emails for any signals suggestive of CEO fraud. For example, suspicious payloads, anomalous geophysical locations, out-of-the-ordinary IP addresses and email clients, keywords that suggests urgency, or unusual sending patterns.
- Once it detects a threat, Tessian alerts employees that an email might be unsafe, explaining the threat in easy-to-understand language.
“Tessian's unique approach to solving complex problems sets it apart from any other solutions I've worked with. ”
Chris Turek
CIO, Evercore
Click here to learn more about how Tessian Defender protects your team from CEO fraud and other email-based cybersecurity attacks. You can also explore our customer stories to see how they’re using Tessian Defender to protect their people on email and prevent social engineering attacks like CEO Fraud.