Attack Types
- All Categories
- ...
-
Advanced Email Threats
Phishing Awareness Training: How Effective is Security Training?
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsFive Ways Tessian Cloud Email Security Improves Enterprise Cybersecurity
-
 Advanced Email Threats
Advanced Email ThreatsWhy You Should Stop Phishing Your Own Employees
-
 Advanced Email Threats
Advanced Email ThreatsWhy Cybercrime is Thriving, And What You Can Do About It
-
 Advanced Email Threats, Threat Stories
Advanced Email Threats, Threat StoriesPhishing Campaigns Pick-Up in the Wake of the Ukraine Invasion
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsNew Research: One in Four Employees Who Made Cybersecurity Mistakes Lost Their Jobs Last Year
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats
Integrated Cloud Email Security, Email DLP, Advanced Email ThreatsBuyer’s Guide to Integrated Cloud Email Security
-
 Advanced Email Threats
Advanced Email ThreatsTessian Defender API Deployment and Enhanced Quarantine Capability
-
 Advanced Email Threats
Advanced Email ThreatsEverything You Need to Know About Tax Day Scams 2022
-
Email DLP, Insider Risks
Examples of Real Insider Threats And How to Manage Them
-
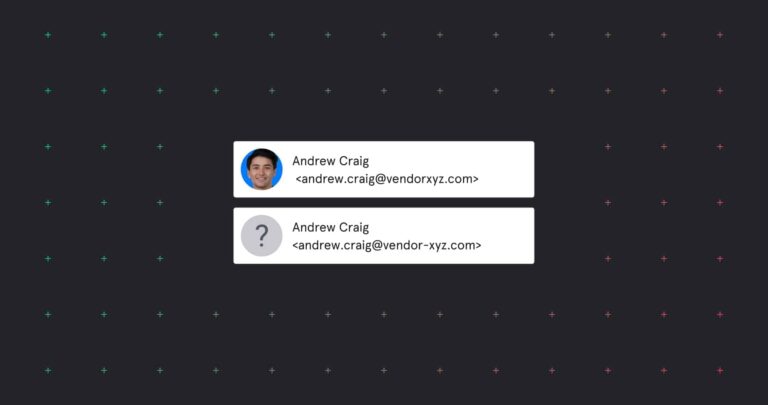 Advanced Email Threats
Advanced Email ThreatsWhat is Email Impersonation? Everything You Need to Know
-
 Advanced Email Threats
Advanced Email ThreatsWhy Enterprises Are Replacing Their SEGs With Microsoft and Tessian
-
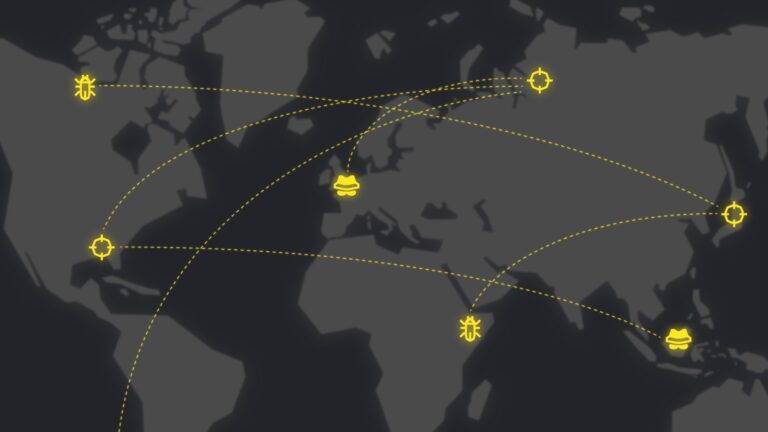 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsNation-States – License to Hack?
-
 Advanced Email Threats
Advanced Email Threats18 Examples of Ransomware Attacks
-
 Advanced Email Threats, Threat Stories
Advanced Email Threats, Threat StoriesAnalysis of a Microsoft Credential Phishing Attack
-
 Email DLP, Insider Risks
Email DLP, Insider RisksWhat is Data Exfiltration? Tips for Preventing Data Exfiltration
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsPlaying Russian Roulette with Email Security: Why URL Link Rewriting Isn’t Effective
-
 Advanced Email Threats
Advanced Email ThreatsPhishing 101: What is Phishing?
-
 Email DLP, Insider Risks
Email DLP, Insider RisksWhy Taking Your Work With You When You Leave a Company Isn’t a Smart Idea
-
 Advanced Email Threats, Threat Stories
Advanced Email Threats, Threat StoriesSpear Phishing Attack Impersonating C-Suite Targets Junior Employees at Law Firm







