Advanced Email Threats
Get up to speed on the latest tips, guides, industry news and technology developments around phishing, spear phishing, Business Email Compromise, and Account Takeover
- All Categories
- ...
-
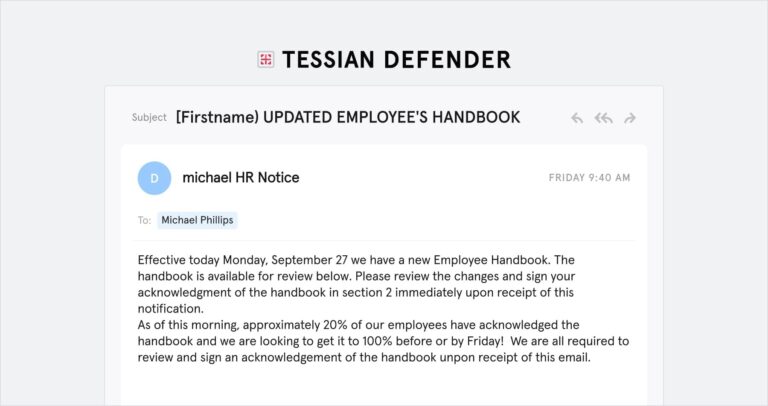 Advanced Email Threats
Advanced Email ThreatsReal Spear Phishing Examples and Why They Worked
-
 Advanced Email Threats
Advanced Email ThreatsAttackers are Using Microsoft Forms to Exfiltrate Data
-
 Advanced Email Threats
Advanced Email ThreatsWhat is Spear Phishing? Targeted Phishing Attacks Explained
-
 Advanced Email Threats
Advanced Email ThreatsHow to Avoid Falling For a Phishing Attack
-
 Advanced Email Threats
Advanced Email ThreatsHow Hackers Are Exploiting The COVID-19 Vaccine Rollout
-
 Advanced Email Threats
Advanced Email ThreatsCOVID-19: Screenshots of Phishing Emails
-
 Integrated Cloud Email Security, Advanced Email Threats
Integrated Cloud Email Security, Advanced Email ThreatsRomance Fraud Scams Are On The Rise
-
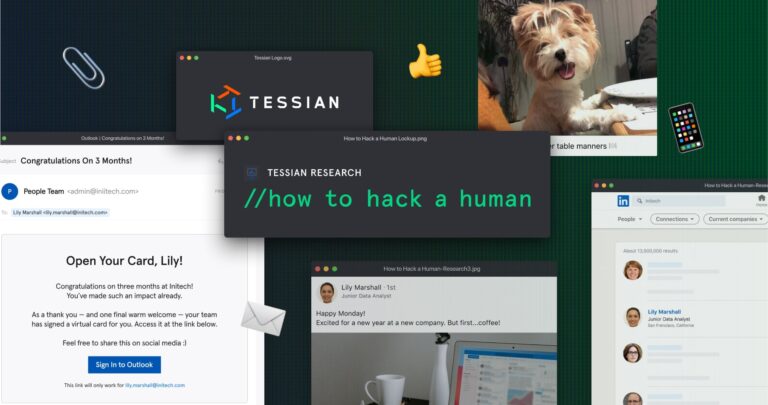 Advanced Email Threats
Advanced Email Threats6 Reasons to Download “How to Hack a Human” Now
-
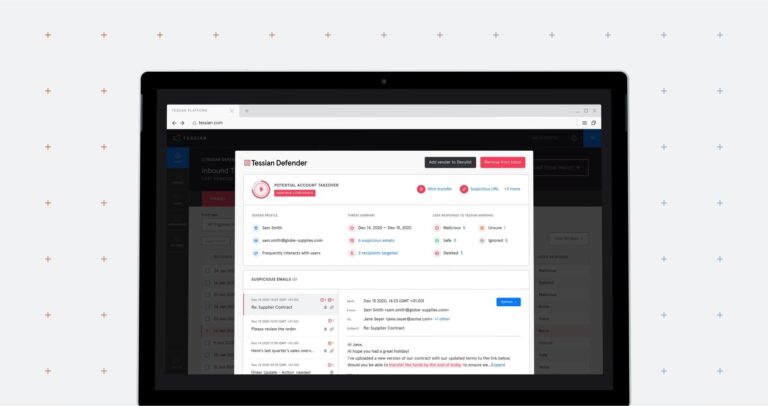 Advanced Email Threats
Advanced Email ThreatsTessian Launches Account Takeover (ATO) Protection
-
 Advanced Email Threats, Remote Working
Advanced Email Threats, Remote WorkingCISA Warns of New Attacks Targeting Remote Workers
-
 Advanced Email Threats
Advanced Email ThreatsWhat is a Malicious Payload and How is it Delivered?
-
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Worst Email Mistakes at Work and How to Fix Them
-
 Email DLP, Advanced Email Threats
Email DLP, Advanced Email ThreatsDecember Cybersecurity News Roundup
-
 Advanced Email Threats
Advanced Email ThreatsWhat Is Account Takeover (ATO)?
-
 Advanced Email Threats
Advanced Email ThreatsSpam vs. Phishing: The Difference Between Spam and Phishing
-
 Advanced Email Threats
Advanced Email ThreatsWhat is a Zero-Day Vulnerability? 3 Real-World Examples
-
 Advanced Email Threats
Advanced Email ThreatsHow to Spot Retail Scams
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider RisksOctober Cybersecurity News Roundup
-
 Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider Risks
Integrated Cloud Email Security, Email DLP, Advanced Email Threats, Insider RisksTessian Included as a Cloud Email Security Supplement Solution in Gartner’s 2020 Market Guide for Email Security
-
 Advanced Email Threats
Advanced Email ThreatsEverything You Need to Know About Wire Transfer Phishing







