With an average cost to businesses of $5.01 million per breach, it’s no surprise that the FBI has named Business Email Compromise (BEC) a “$26 billion scam”, and the threat is only increasing. Business Email Compromise (BEC) attacks use real or impersonated business email accounts to defraud employees. In 2020, BEC scammers made over $1.8 billion – far more than via any other type of cybercrime.
You can find more information on what exactly BEC is and how it works in this article: What is Business Email Compromise and How Does it Work? , and understand how Tessian prevents BEC, across industries here.
But what does a BEC attack look like in real-life? This article details 16 examples of BEC attacks that have cost victims money, time, and reputation, to help you avoid making the same mistakes.
1. Facebook and Google: $121m BEC scam
First, let’s look at the biggest known BEC scam of all time: a VEC attack against tech giants Facebook and Google that resulted in around $121 million in collective losses.
The scam took place between 2013 and 2015 — and the man at the center of this BEC attack, Evaldas Rimasauskas, was sentenced to five years in prison in 2019.
So how did some of the world’s most tech-savvy employees fall for this elaborate hoax?
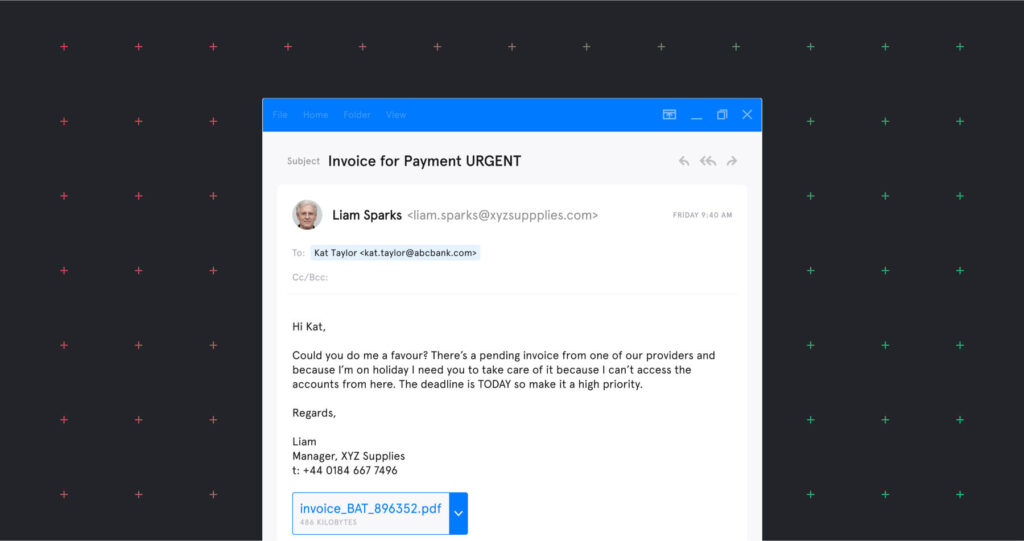
Rimasauskas and associates set up a fake company named “Quanta Computer” — the same name as a real hardware supplier. The group then presented Facebook and Google with convincing-looking invoices, which they duly paid to bank accounts controlled by Rimasauskas.
As well as fake invoices, the scammers prepared counterfeit lawyers’ letters and contracts to ensure their banks accepted the transfers.
The Rimasauskas scam stands as a lesson to all organizations. If two of the world’s biggest tech companies lost millions to BEC over a two-year period — it could happen to any business.
2. Ubiquiti: $46.7m vendor fraud
In August 2015, IT company Ubiquiti filed a report to the U.S. Securities and Exchange Commission revealing it was the victim of a $46.7 million “business fraud.”
This attack was an example of a type of BEC, sometimes called Vendor Email Compromise (VEC). The scammers impersonated employees at a third-party company and targeted Ubiquiti’s finance department.
We still don’t know precisely how the cybercriminals pulled off this massive scam. VEC attacks previously relied on domain impersonation and email spoofing techniques, but these days, scammers are increasingly turning to the more sophisticated account takeover method.
3. Toyota 2019: $37 million BEC attack
Kicking things off with a name you may recognize – in 2019 Japan’s Toyota Boshoku Corporation was hit with a $37 million BEC attack. The huge size of the company meant that though $37 million may appear alarming to you or I, hackers were able to implore an employee to transfer the sum out of the European subsidiary before being detected.
With BEC on the rise, and this attack being the third that Toyota had experienced that year so far, critics say that Toyota should have been on the lookout for the scam.
As Toyota learnt the hard way, BEC attacks often exist in multiples – with one attack opening the door to many more as money, IP, data or identities are stolen.
4. Obinwanne Okeke: $11 million in losses
In February 2021, celebrated entrepreneur Obinwanne Okeke was sentenced to 10 years in prison for his involvement in a BEC scheme that resulted in at least $11 million in losses to his victims. Using phishing emails to secure the login credentials of business executives (including the CFO of British company Unatrac Holding), these initial phishing scams then acted as a platform for BEC.
As is often the case, BEC was just one part of a tapestry of fraud and cybercrime, with Okeke also creating fraudulent webpages to further manipulate his victims. The money transfers also went directly into overseas accounts, meaning that local law enforcement couldn’t aid in recovering them.
5. Scouler Co.: $17.2m acquisition scam
This example demonstrates how fraudsters can play on a target’s trust and exploit interpersonal relationships. In June 2014, Keith McMurtry, an employee at Scouler Co, a company in Omaha, Nebraska, received an email supposedly from his boss, CEO Chuck Elsea. The email informed McMurty that Scoular was set to acquire a Chinese company.
Elsea instructed McMurty to contact a lawyer at accounting firm KPMG. The lawyer would help facilitate a transfer of funds and close the deal. McMurty obeyed, and he soon found himself transferring $17.2 million to a Shanghai bank account in the name of “Dadi Co.”
The CEO’s email, as you might have guessed, was fraudulent. The scammers had used email impersonation to create accounts imitating both Elsea and the KPMG lawyer.
Aside from the gargantuan $17.2m loss, what’s special about the Scoular scam? Take a look at this excerpt from the email, provided by FT.com, from “Elsea” to McMurty:
“We need the company to be funded properly and to show sufficient strength toward the Chinese. Keith, I will not forget your professionalism in this deal, and I will show you my appreciation very shortly.”Given the emotive language, the praise, and the promise of future rewards — it’s easy to see why an employee would go along with a scam like this.
6. Homeless Charity, Treasure Island: $625,000 BEC loss
BEC rates have been rising for several years, as demonstrated by 2021 data from the FBI’s Internet Crime Complaint Center (IC3). So perhaps it’s unsurprising—if somewhat disheartening—that law enforcement agencies are struggling to cope with all the BEC incidents that companies are reporting to them.
In June 2021, we learned that San Fransisco-based homelessness charity Treasure Island fell victim to a devastating, month-long $625,000 BEC attack after hackers infiltrated the organization’s bookkeeper’s email system.
The hackers found and manipulated a legitimate invoice used by one of Treasure Island’s partner organizations. Staff at Treasure Island transferred a loan intended for the partner organization straight into the cybercriminals’ bank account.
The nonprofit sadly lacked cybercrime insurance. But even worse—the U.S. Attorney’s Office in San Fransisco, which would have been responsible for leading an investigation into the BEC attack, reportedly declined to investigate the incident.
This case serves as a reminder that, when it comes to cybercrime, prevention is always better than cure. Building security into your systems is the only viable way to avoid the losses associated with BEC attacks.
7. Government of Puerto Rico: $2.6 million transfer
In early 2020, while dealing with the aftermath of a 6.4-magnitude earthquake, the Puerto Rican government discovered they had fallen victim to a BEC scam. The direct victim of the scam was Rubén Rivera, finance director of Puerto Rico’s Industrial Development Company who mistakenly transferred over $2.6 million to a fraudulent bank account.
Rivera had received an email explaining that there had been a change to the bank account tied to remittance payments. The email had come from a hacked email account of an employee of the Puerto Rico Employment Retirement System.
Three employees were suspended after the attack and fortunately, the money, which included public pension funds, was frozen by the FBI. Manuel Labor, executive director of the Industrial Development Company insisted that the incident “did not affect and will not affect pension payments to retirees”.
8. St. Ambrose Catholic Parish: $1.75 million
While enjoying the recent restoration and repair of the church roof, St. Ambrose Catholic Parish in Ohio was given a nasty surprise when it fell victim to a BEC attack.
Hackers pretended to be the construction firm that had repaired the roof, and emailed parish officials claiming that they had not been paid in two months. The parish swiftly wired $1.75 million into a fraudulent account, and the perpetrators swept it out before anyone knew what had happened.
On top of hiring a third-party cybersecurity firm to assess their system and policies, the parish resolved to start sending manual checks again instead of wire transfers to stop any future fraudsters in their tracks.
9. Guillermo Perez: $2.2 million
From (at least) October 2018 to October 2019, Guillermo Perez and his co-conspirators led a BEC scam that made them $2.2 million richer (allegedly – he’s awaiting trial). As part of the scheme, Perez and co-conspirators provided banks with false and misleading information regarding their affiliations.
Lured into a false sense of security, the banks then opened business accounts for them that were fraudulent. Perez and his fellow attackers then used BEC to manipulate victims into transferring over $2.2 million into the fraudulent accounts – money that was moved swiftly into the attackers’ pockets.
10. Save the Children: $1 million
There is seemingly no limit to who BEC attackers will target – as demonstrated in 2018 with an attack on Save the Children that cost the charity $1 million. The attacker gained access to an employee’s email account and from there sent fake invoices and other documents pretending that the money was needed to pay for health centre solar panels in Pakistan.
The charity has had a base there for decades, so the attack was well-researched and effective, and before the scam was exposed the money had already been deposited in a Japanese bank account.
11. Noel Chimezuru Agoha, Sessieu Ange Oulai and Kelechi Arthur Ntibunka: $1.1 million
In March 2021, Noel Chimezuru Agoha, Sessieu Ange Oulai, and Kelechi Arthur Ntibunka were charged with conspiracy to commit wire fraud, conspiracy to commit money laundering, and aggravated identity theft. This was all as (allegedly) part of a series of BEC scams that saw the attackers pose as clients of victims to intercept payments totaling over $1.1 million dollars.
The BEC scam was accompanied by a dating scam, which involved manipulating victims on dating websites into believing they were in a romantic relationship with the scammers, and coaxing them into sending money. These scams exemplify the sophisticated social engineering techniques that are often found in BEC and other forms of cyberattacks.
12. Atlanta BEC scammer: Sentenced after making $250,000+
In June 2021, an Atlanta court sentenced Anthony Dwayne King to two and a half years in prison for his role in a BEC scam—but only after he’d earned nearly $250,000 ripping off businesses and individuals across four U.S. states.
Between October 2018 and February 2019, King and his accomplices conducted BEC and vishing (phone phishing) operations, setting up fake companies and opening fraudulent bank accounts to redirect wire transfers.
The cybercriminals targeted law firms and home movers but were thwarted by Georgia’s Cyber Fraud Task Force. As well as serving federal prison time, King will have to repay the money he stole from his victims.
13. Gift card scams
Gift card BEC scams have always been popular amongst the cybercrime community – and according to the FBI, the prevalence of this type of scam is only increasing. Victims receive an email from attackers masquerading as an authority figure asking victims to purchase gift cards for personal or business reasons. Sometimes the attacker will also request a wire transfer payment, much like the classic BEC scam.
An example of this type of attack was seen in 2019 when attackers impersonated Rabbis in Virginia and convinced their synagogue congregants to purchase gift cards for a fundraiser and told them to send back pictures of the serial numbers.
As you might imagine, this type of attack is particularly common during the holiday season and Black Friday. According to a report from the Anti-Phishing Working Group, 66% of BEC attacks included a request for gift card payment in the second quarter of 2020.
14. Snapchat payroll information breach
Many high-profile BEC attacks target a company’s finance department and request payment of an invoice to a new account. But not all BEC scams involve wire transfer fraud. Here’s an example of how BEC scams can target data, as well as money.
In February 2016, cybercriminals launched a BEC attack against social media firm Snapchat. Impersonating Snapchat’s CEO, the attackers obtained “payroll information about some current and former employees.”
The scam resulted in a breach of some highly sensitive data, including employees’ Social Security Numbers, tax information, salaries, and healthcare plans. Snapchat offered each affected employee two years of free credit monitoring and up to $1 million in reimbursement.