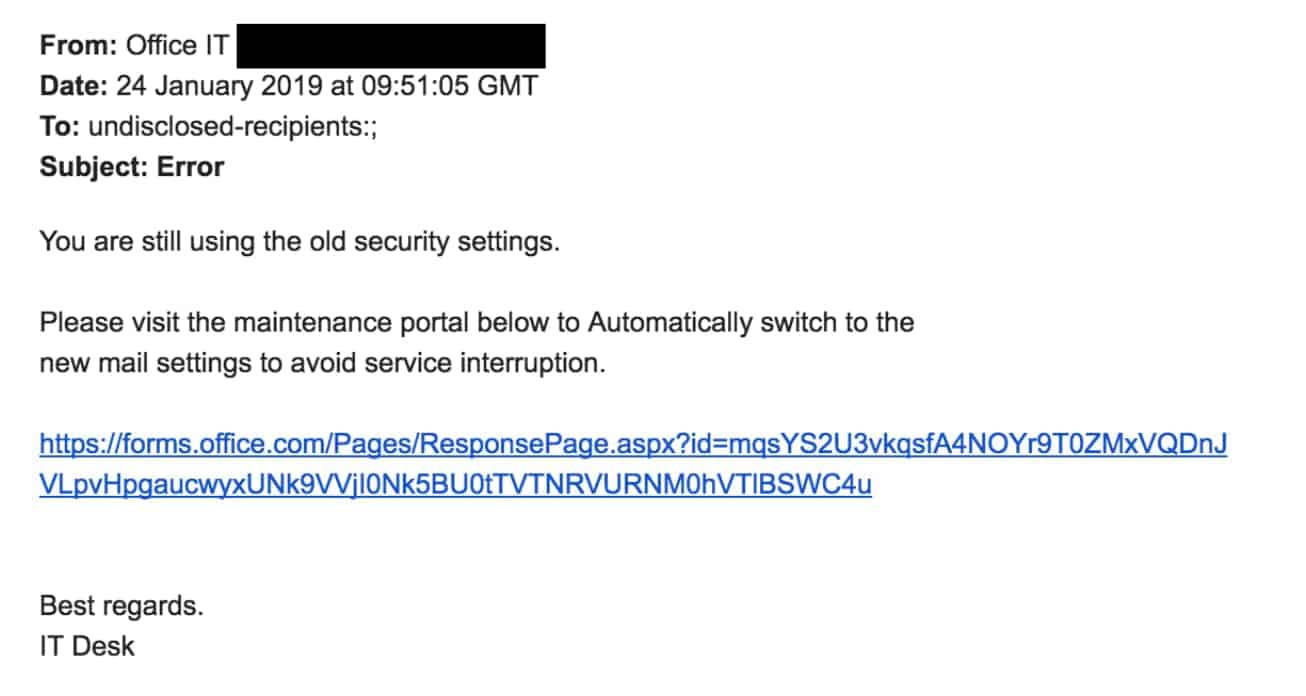
Attackers are using Microsoft Forms links to get past email URL protection and steal sensitive information. We were alerted to this new tactic by one of our clients in the financial services sector. They recently received a spear phishing email containing a Forms link.
In an attempt to protect firms from credential pharming and malware, several email security providers including Proofpoint, Mimecast and O365 Advanced Threat Protection re-write and scan URLs within emails to verify that the URL is safe to visit. The effectiveness of this approach has been questioned before, and now a new vulnerability involving the use of Microsoft Forms is being exploited by attackers.
How are they exploiting Microsoft Forms?
Microsoft Forms is an online tool for creating quizzes and surveys and automatically collecting the results. Forms were fully released to enterprise users of Office 365 in 2018.
Here’s how they work
You create a survey or quiz via Microsoft Forms and distribute it to your audience by embedding a link in an email. To fill out the form, a recipient will click the link within the email and be directed to a Microsoft Form containing fields that capture whatever data the form is designed to collect.
Crucially, because the links direct users to a genuine Microsoft site, Forms links are trusted by the URL protection from Secure Email Gateways and ATP. Attackers have become aware of this and are now using authentic Microsoft Forms to collect sensitive information from unwitting targets. Any data input into the form is automatically sent to attackers, bypassing security defenses.