The Black Friday sales weekend is fast approaching, with many consumers set to splash their cash and bag themselves a bargain before the holidays. According to Adobe Analytics, online spending surged by 22% during Black Friday 2020, with consumers spending $9 billion on retailers’ websites the day after Thanksgiving.
And Black Friday 2021 is set to be no different.
In a recent Tessian survey, 62% of U.S. consumers told us they will take part in Black Friday shopping this year. It’s important, then, to be wary of the phishing and smishing scams that you could receive.
Why Cybercriminals Leverage Black Friday for Phishing Attacks
When our researchers analyzed malicious emails between July 2020 and July 2021, they saw a significant spike during Q3 2020, immediately before and after Black Friday.
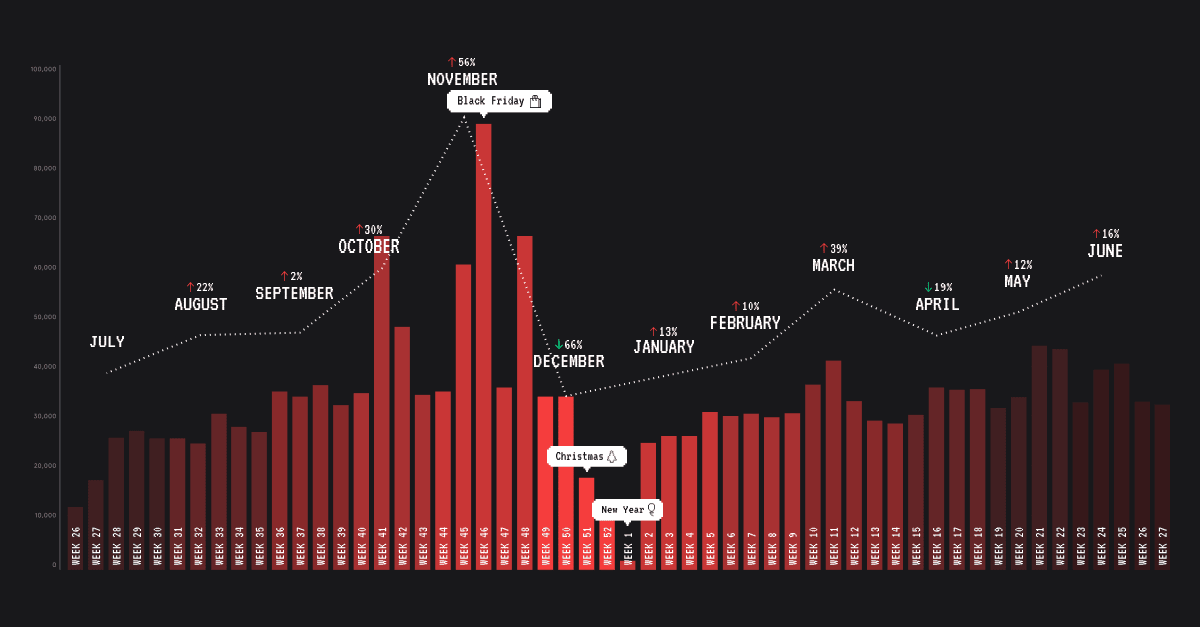
What’s more, nearly a third of U.S. consumers (30%) said they received a phishing email around Black Friday last year, either by email or SMS to their personal email or cell.
The thing is that consumers expect to receive more marketing and advertising emails from retailers during this time, touting their deals, along with updates about their orders and notifications about deliveries. Inboxes are noisier-than-usual and this makes it easier for cybercriminals to ‘hide’ their malicious messages.
What’s more, attackers can leverage the ‘too-good-to-be-true’ deals people are expecting to receive, using them as lures to successfully deceive their victims. When the email looks like it has come from a legitimate brand and email address, people are more likely to click on malicious links that lead to fake websites or download harmful attachments.
“Nearly a third of U.S. consumers received a phishing email around Black Friday last year, either by email or SMS.”
Tessian Research
And it’s not just consumers that need to be wary. Employees in the retail industry will be busier and more distracted than ever during this time, faced with hundreds of orders, thousands of customer queries to respond to, and overwhelming sales targets to hit. Cybercriminals will use this to their advantage, crafting sophisticated phishing emails and cleverly worded social engineering messages in the hope that a stressed worker will miss the cues and comply with their requests.
In fact, security leaders in the retail industry told us that they aren’t 100% confident that their staff will be able to identify the scams that land in their inbox during these busier periods.
Being made aware of the scams and being provided with sound advice – in-the-moment – on what to do if they do receive a phishing email will make the difference between whether an employee clicks on the link or shares their credentials versus if they don’t.
Impersonating Couriers to Advance Phishing Scams
As the number of online purchases grew throughout the pandemic, so did the number of emails and SMS messages in which scammers impersonated delivery companies and logistics firms.
In fact, our survey revealed that one in five (20%) U.S. consumers and 33% of U.K. consumers received a phishing scam from a hacker posing as a delivery service this year already.
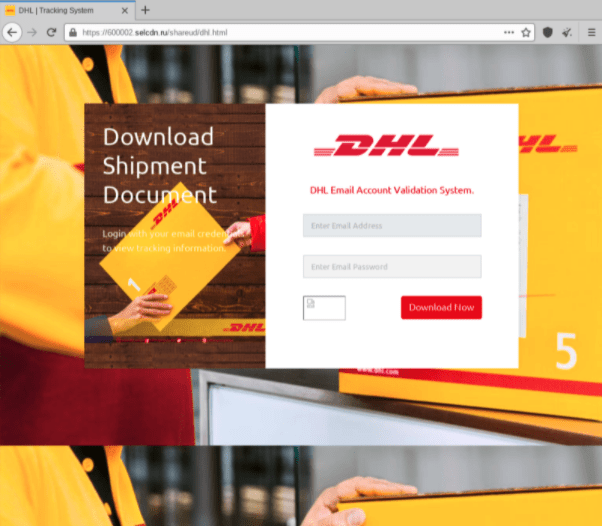
With consumers spending billions online during the upcoming Black Friday and Cyber Monday, it’s highly likely that delivery-related phishing scams will surge – especially against the backdrop of the supply chain issues retailers are currently facing, which are causing delays and product shortages.
For example, these supply chain issues mean delivery services are expected to experience higher-than-normal demand. This is creating an opportunity for bad actors to scam people through SMS and email, posing as legitimate couriers or logistics companies and claiming to have important information regarding a package.
It’s particularly concerning, then, that two-thirds (64%) of the top couriers are at risk of having their domains impersonated by phishers and scammers as a result of not having Domain-based Message Authentication, Reporting & Conformance (DMARC) records set to the strictest settings.
In fact, just 20% of the top couriers have configured DMARC policies to the strictest settings to prevent abuse of the domain by scammers and phishers.
Without the proper DMARC records in place, an attacker could impersonate one of these couriers’ domains in phishing campaigns, tricking people into thinking they’re opening an email from a trusted and legitimate source about an order or delivery update.
From that phishing email, hackers could lure their targets to a fake website that has been set up to steal account credentials or personal and financial information.
For the consumer, it really wouldn’t seem out of the ordinary to receive a message that asks them to ‘learn more’ about a delivery update or reschedule a missed delivery.
How to Avoid Falling For Black Friday Phishing and Smishing Attacks
Here are some simple tips for you, your employees, friends and family to follow this Black Friday:
- Inspect emails and text messages to look out for spelling errors; these are a sure sign that it is not from a legitimate source.
- Take a few seconds to verify that the sender’s name and email address match up, especially if you are reading your emails on your mobile. Cybercriminals typically spoof a brand’s name in the hope that you’ll fail to inspect the email domain.
- Be wary of business messages from unknown numbers or numbers starting with a local area code such as +44, as these are regularly associated with scam texts.
- If you’re led to a website, look for the padlock in the URL bar to verify the website is secure or not.
- And, if in doubt, just don’t click. You can follow up with the delivery company or retailer directly if you have a question that needs to be answered.
And for security teams at retailers and delivery companies:
- Educate your staff – everyone from senior executives to temporary/seasonal employees – on the scams they could be exposed to during this busy period and train them on what to do should they receive a malicious message.
- Remind employees to expect emails that come from suppliers or third parties; posing as a trusted connection is another way in which cybercriminals will try to hack into the organization.
- Configure email authentication records like DMARC and set strict policies – this is a necessary first step in preventing attackers from directly impersonating your business’s email domain.
Charles Brook
Threat Intelligence Specialist














