Overview
- Industry: Legal
- Size: 5,000 employees
- Platform: O365
In May 2021 Tessian Defender flagged a series of emails sent to a global law firm. The emails were attempting to impersonate a senior partner at the firm and targeted a list of other partners.
Reconnaissance
The firm being targeted by the attacker operates globally, but the senior partner they were impersonating was based in Australia. All employees targeted in the attack – including their contact details – are featured on the firm’s website.
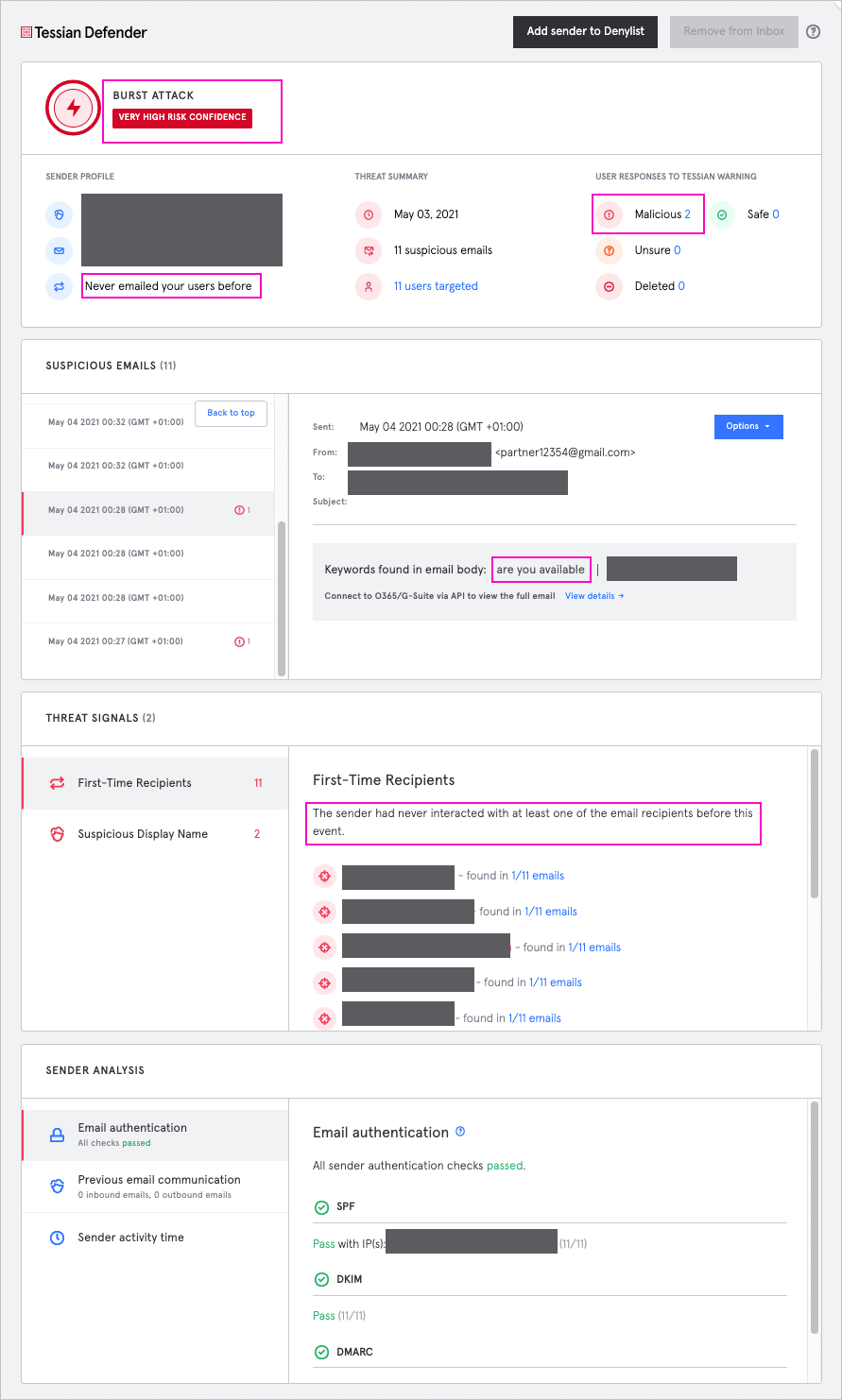
Eleven partners were targeted by the attacker. All of them were also based in Australia, indicating the attacker spent time considering who to target based on what they were able to learn from reconnaissance activities against the individual they wanted to impersonate. It is likely they chose targets they assumed would be in regular contact with the senior partner at the firm.
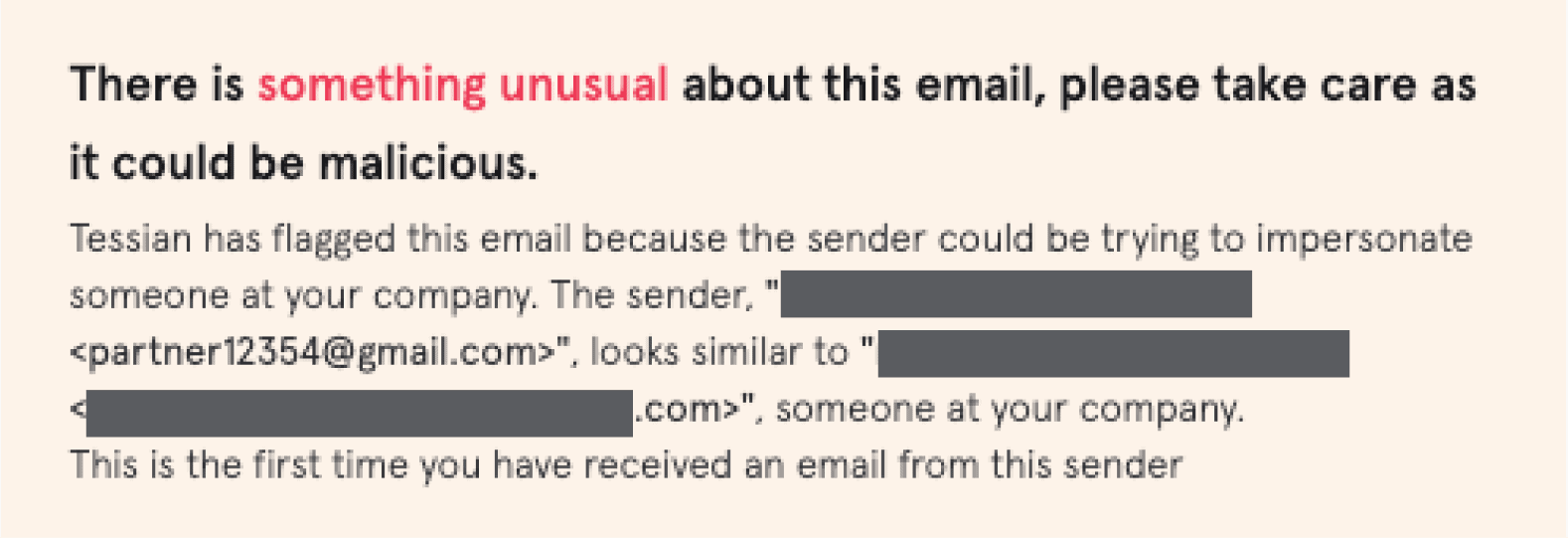
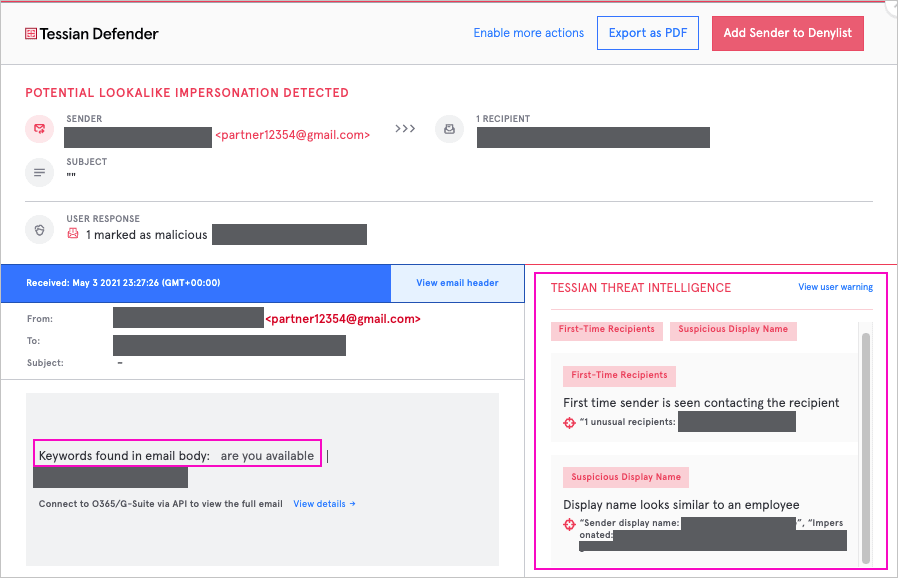
The attacker had registered an email address with Gmail containing the word “partner” at the beginning followed by a series of numbers. They also changed the display name associated with the address to match the name of a senior partner at the firm they were targeting.
Attack Deployed
In the email sent, the attacker asked questions about the targeted recipient’s availability, implying that part of the intention was to establish a dialog for social engineering. From the email headers, it also appears that the email was sent from a mobile device.
There were no links or attachments included in any of the emails. It is likely the attacker was hoping to receive a response from any of the 11 targeted partners, with the intention of building a rapport and then socially engineering them into carrying out actions on the attacker’s behalf; for example, giving up sensitive information or unwittingly compromising the firm’s network infrastructure by further directing them to a malicious link or attachment.
Threat Detected and Prevented
At the time the emails were sent, Tessian Defender was being trialed at the firm across a subset of users. Two of the users who received the email had Defender installed. For both users, Defender flagged the email as a possible impersonation of someone else at the firm based on the display name, and warned them there was something suspicious about it.