Note: The Sanne Group was acquired by Apex Group in August 2022
Company: Sanne Group
Industry: Financial Services
Seats: 1,850
Solutions: Guardian, Enforcer, Defender
About Sanne Group
Sanne is an award-winning, leading global provider of alternative asset and corporate services with 22 offices across the globe that serve nearly 2,000 clients, including leading fund managers, financial institutions, and global corporates.
Today, the firm manages more than £250 billion in assets.
Sanne deployed Tessian as their complete outbound email security solution in May 2019 and, 18 months later, added Tessian Defender to prevent spear phishing attacks and other impersonation attacks.
“In these tests, employees typically click on links in phishing emails about 15%-20% of the time. During a trial with Defender enabled, this simulation number dropped to less than 5%.”
Marie Measures
CTO
Problem: Despite having deployed other email solutions and training staff, phishing emails were still getting through…and staff were still clicking on them.
Marie Measures, Sanne’s Chief Technology Officer, and her team take cybersecurity seriously. That means the firm was protected by other inbound security solutions – including native controls, Secure Email Gateways (SEGs), and antivirus software – before deploying Tessian Defender.
The problem was, those tools just weren’t stopping all inbound attacks and phishing and spear phishing emails were still landing in employees’ mailboxes. According to Marie, on average, 150 were being reported a month to the security team.
“Even with all of these controls, emails were still getting through and we were still relying on end-users to make good decisions. We even had one solution in place that triggered a pop-up if a suspicious email was detected, simply asking employees if they wanted to continue. They’d often click “yes”. So when we were evaluating new solutions, it was important to us that users would actually interact with the warnings, ” Marie explained.
After allowing Defender to flag potentially malicious emails during a phishing simulation, Marie saw how Tessian warnings did prompt employees to engage with the warnings.
“In these tests, employees typically click on links in phishing emails about 15%-20% of the time. During a trial with Defender enabled, this simulation number dropped to less than 5%,” she said.
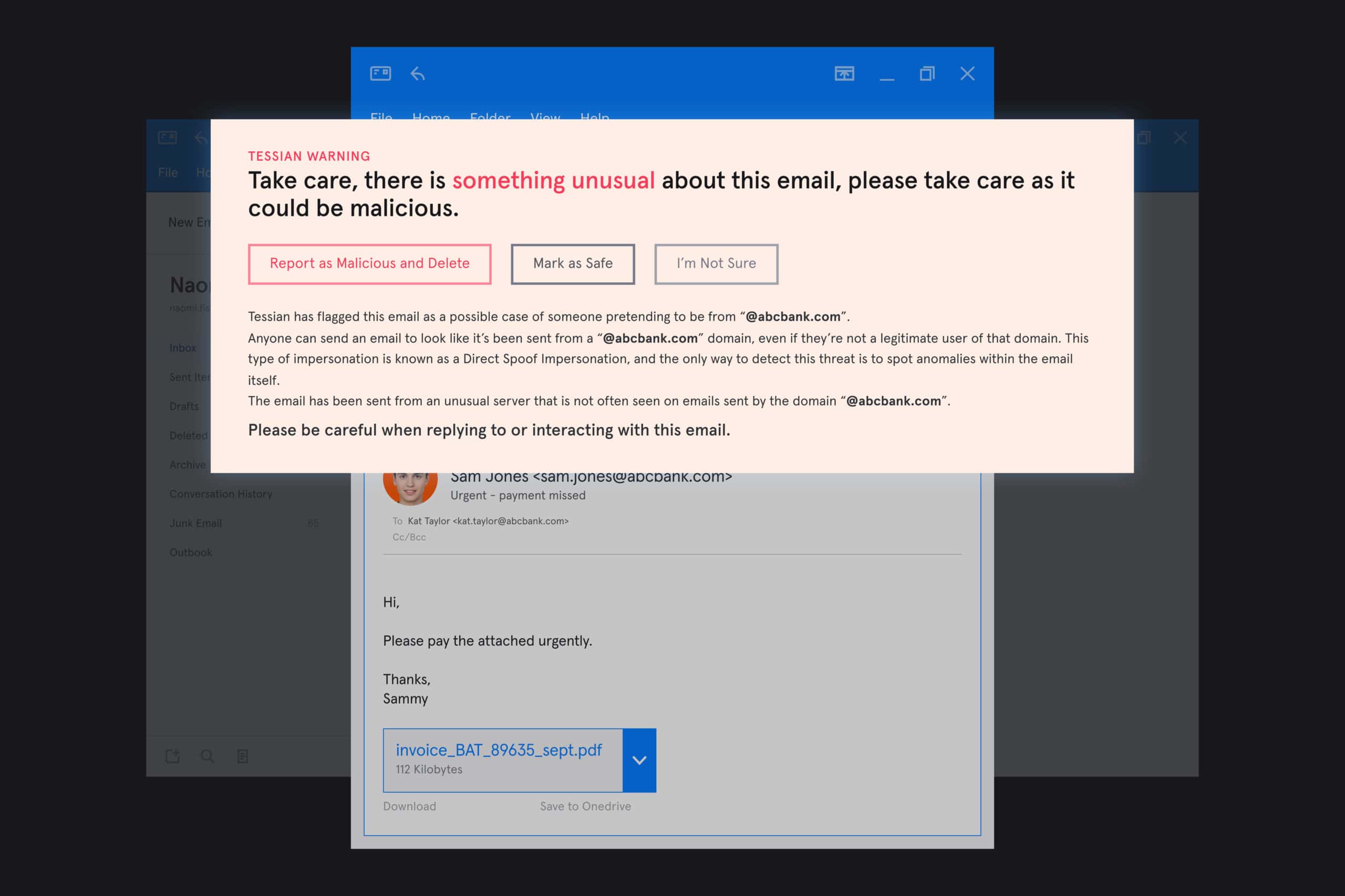
The difference between Tessian’s warnings and the other solution? Context.
“Tessian explains the “why” which is very important for awareness. It also appears within the email itself versus employees having to click through a pop-up or link to view the warning. It’s impossible to ignore and easy to understand,” Marie said.
Employees began interacting with the warnings immediately.
Marie continued, “We did not have to send out any communications to staff explaining how to interact with the tool, which is a testament to how intuitive it is. No staff training, no staff comms, nothing. We just turned it on and employees started engaging with the warnings.”
Tessian’s in-the-moment warnings explain exactly why emails are flagged in plain English. This way, training is reinforced and employee’s security reflexes improve over time.
How does Tessian Defender detect and prevent impersonation attacks?
Powered by machine learning, Tessian’s Human Layer Security technology understands human behavior and relationships to automatically prevents both known and unknown email attacks that bypass Secure Email Gateways (SEGs), while also providing in-the-moment training to educate employees and drive them towards more secure email behavior.
Here’s how:
- Tessian’s machine learning algorithms analyze your company’s email data, learn every employee’s normal communication patterns. and map their trusted email relationships — both inside and outside your organization.
- Tessian inspects inbound emails for any suspicious or unusual content both in the body of the email and the metadata. For example, payloads or anomalous domains, geophysical locations, IP addresses, email clients, or sending patterns.
- Tessian alerts employees when an email might be unsafe with easy-to-understand, contextual warnings.
Sanne Group’s Case Study