The threat caused by malicious, embedded URLs will grow as Business Email Compromise (BEC) attacks increase. Only a behavioral-based approach that involves a thorough examination of the URL content contained within the email body and its attachment allows you to reduce the risk of a URL-based email compromise.
Differentiating from the SEG
While URL link rewriting, also known as time-of-click protection, is offered by legacy email security providers, such as Secure Email Gateways (SEGs), it has major restrictions on the level of security it can provide. The problem is that your protection is only as effective as the rules and policies you create and how up-to-date the threat detection engine of known threats is.
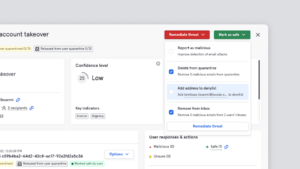
Tessian enhances the protection against known and unknown malicious URLs by ensuring they are detected and retrieved from both the email’s body as well as any attachments that may include them. From here the URLs are analyzed against known and unknown indicators of compromise (IOC).
Cyber Criminals break the rules
The static, rule-based approach to malicious URL detection offered by legacy email security presents an open opportunity for threat actors to circumvent them using a range of obfuscation methods. For example, in a well-documented case of APT 39’s malicious URL campaign, the cyber criminals were able to hide malicious links within attached files and bypassed the rule-based SEGs of numerous victims.
Five Shortcomings of URL Link Rewriting Protection
Here are five additional reasons why URL Link Rewriting falls short in protecting your organization from malicious URLs:
-
URL link rewriting is an overly manual security control prone to human error
It requires a significant degree of manual security rule and policy orchestration. The static nature of URL policy and rule orchestration also opens up the probability of human error introducing security risk, by either failing to set the appropriate degree of URL scanning intensity, or failing to include appropriate user groups.
-
URL link rewriting is ineffective at protecting against zero-day attacks
It only offers protection against known threats and limited protection against zero-day attacks. For example, registering new domains or hijacking existing “trusted” domains are popular methods of evasion by threat actors.
-
URL link rewriting lacks the intelligence to detect advanced attacks on email
Threat actors are continuously becoming more sophisticated. Hiding malicious URls in an attachment or having a redirected link tricks the victim into thinking they are clicking on a perfectly safe link when in fact they are actually clicking on a malicious link.
-
Protection starts and stops at the gateway
When utilizing a perimeter solution, such as a SEG, you can only see what is coming into and out of the organization. Lateral phishing attacks are missed as the email doesn’t pass the gateway.
-
If all you have is a hammer, everything looks like a nail
URL link rewriting offers no protection against cross-site scripting (XSS) attacks. In this type of attack, threat actors will send a benign-looking URL link to a victim, usually from a legitimate but recently compromised website. Here the threat actor is able to capture credentials from the victim, for example on a log-in page of the compromised website. Legacy email security solutions would have determined that the link is “safe” even if the email was received from an unknown or suspicious party.
The need for Intelligent Cloud Email Security
Email-based attacks are still by far the most popular attack vector. The efficiency of legacy email security controls has come into sharp focus as a result of the constantly shifting and developing attack landscape.
Threat actors are continuously becoming more sophisticated and circumventing the rules-based approaches of legacy email security tools. Today URL link rewriting is no longer capable of defending organizations from advanced attacks on email. Only by leveraging intelligent email security solutions that understand behavior and have contextually aware scanning capabilities – detecting the most obfuscated of URLs – can you significantly improve your email security posture against URL-based attacks.
To see how the Tessians Intelligent Cloud Email Security platform prevents ransomware attacks, and protects against data loss, watch a product overview video or book a demo.
For the latest cybersecurity news and articles, sign up for our newsletter, and follow us on Twitter and LinkedIn
James Alliband
Director of Product Marketing