In August Tessian’s Threat Intel team saw a new Business Email Compromise malware campaign in the wild called Logokit. Logokit is an impersonation attack phishing kit used to propagate Business Email Compromise campaigns to harvest credentials.
How Logokit exploit kits work
Threat actors will impersonate domains of trusted brands, commonly seen impersonating healthcare, financial or legal services providers. The phishing email usually contains a malicious URL or attachment.
The unsuspecting victim will click on the malicious URL which in this case redirects to an impersonated website of Microsoft. There, the threat actors attempt to harvest login credentials.
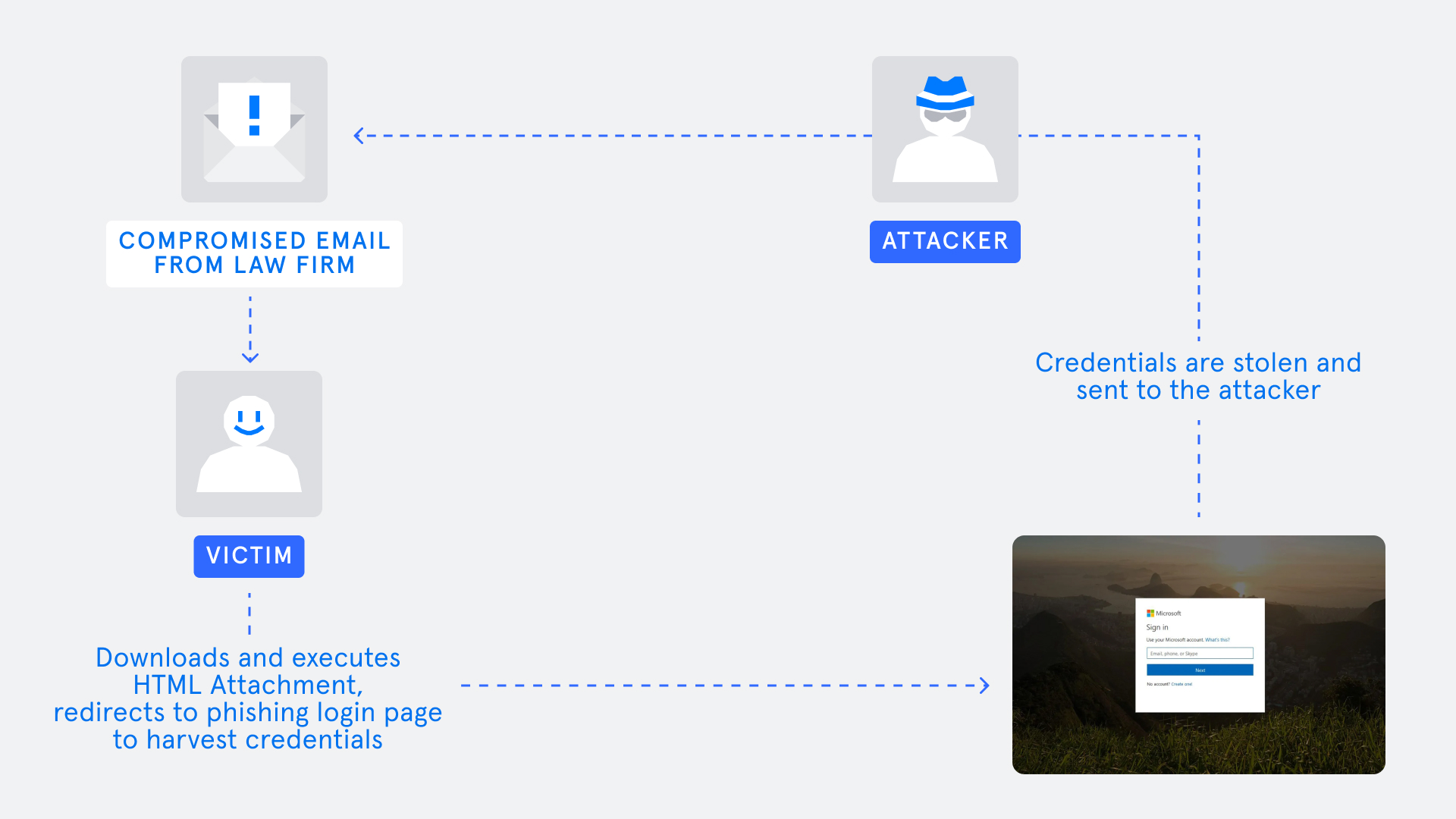
The attack chain
1: The law firm is impersonated and a spoofed account is used to send a malicious email to the victim.
2: The victim receives the malicious email and downloads the malicious HTML attachment.
3: Upon execution of the HTML page, the final landing page is Microsoft impersonation page, requesting the victim to enter Microsoft login credentials.
4: The compromised credentials that were inserted by the victim are then harvested by the threat actor.
Threat analysis
In the case that Tessian Threat Intel analyzed, a victim of this campaign was targeted by threat actors impersonating a law firm. The impersonated email from the law firm contained the company logo, as well as an obfuscated HTML attachment titled: Letter To Buyer’s Solicitor Enclosing Contract Bundle.htm
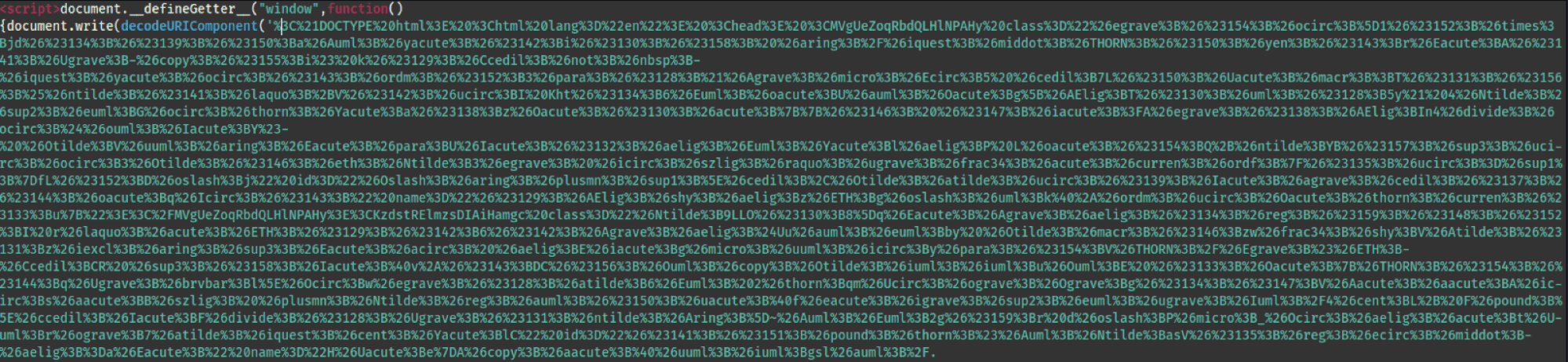
Code snippet in the HTML page
Tessian Threat Intel started the investigation in a virtual environment, analyzing the attached HTML file. At first inspection the HTML file appeared benign. We, then, analyzed the HTML file in a non-virtual environment. This initial HTML file then redirects to an impersonated Microsoft login webpage.
Conclusion and recommendations for staying safe
At the initial time of analysis, the Logokit redirect campaign stopped at the Microsoft phishing landing page. There is a high probability that this campaign could be altered in the coming days and weeks, landing on a different page.
In order to not fall victim to similar types of phishing emails we recommend:
- Being careful of unsolicited emails, especially those containing attachments or URLs.
- Before interacting with any suspicious email received, check the source and email header to confirm the organization it originated from is legitimate.
- If anything seems unusual, do not follow or click on links, or download attachments.
- If the suspicious email appears to come from someone you know and trust, like a colleague, reach out to the individual directly by phone, Slack, or a separate email thread. Rest assured, it’s better to confirm and proceed confidently than the alternative.
- Adopt intelligent cloud email security solutions like Tessian that use behavioral intelligence to detect and prevent advanced email attacks, including increasingly sophisticated impersonation emails.
Catalin Giana
Threat Intelligence Engineer