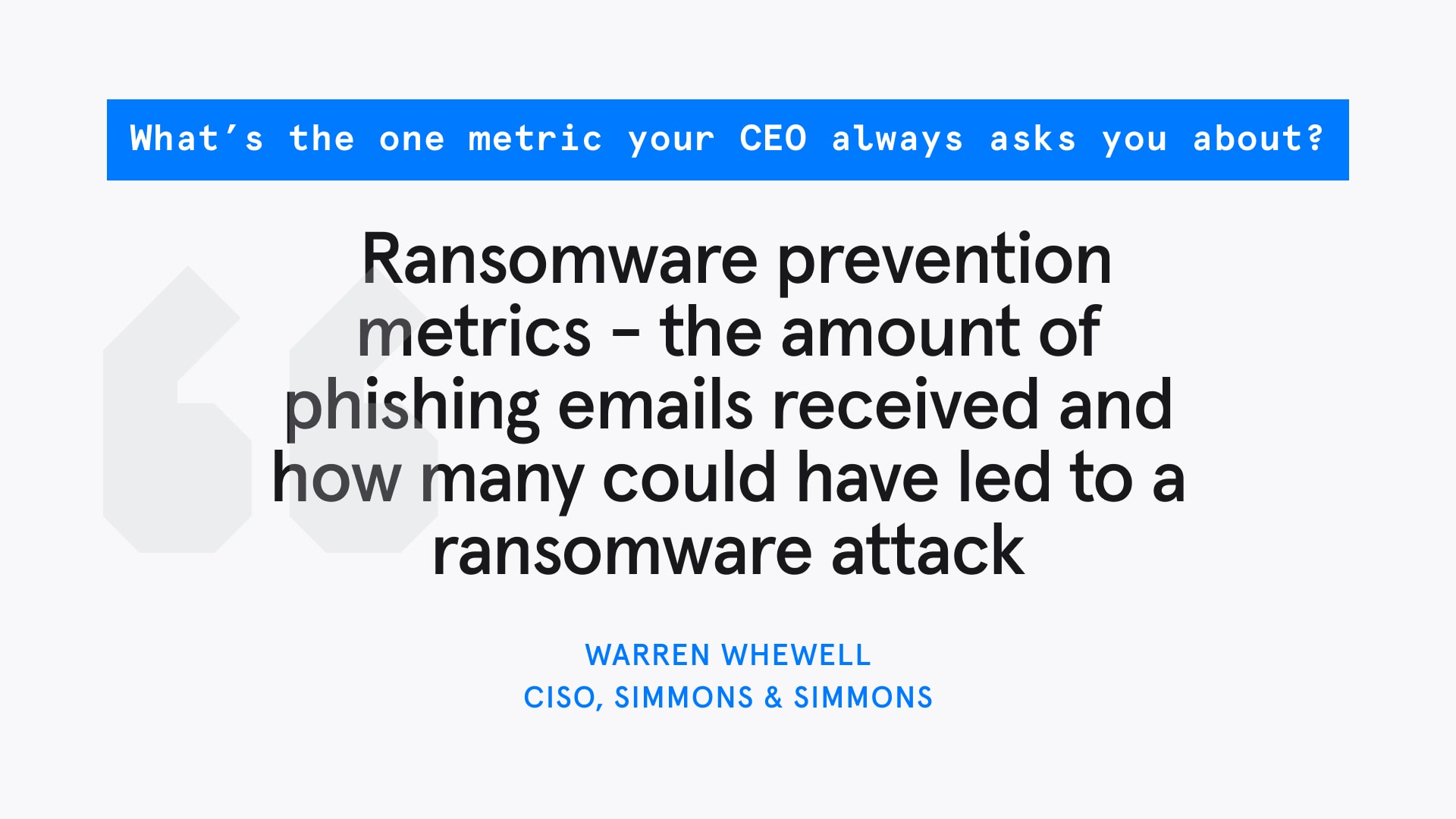
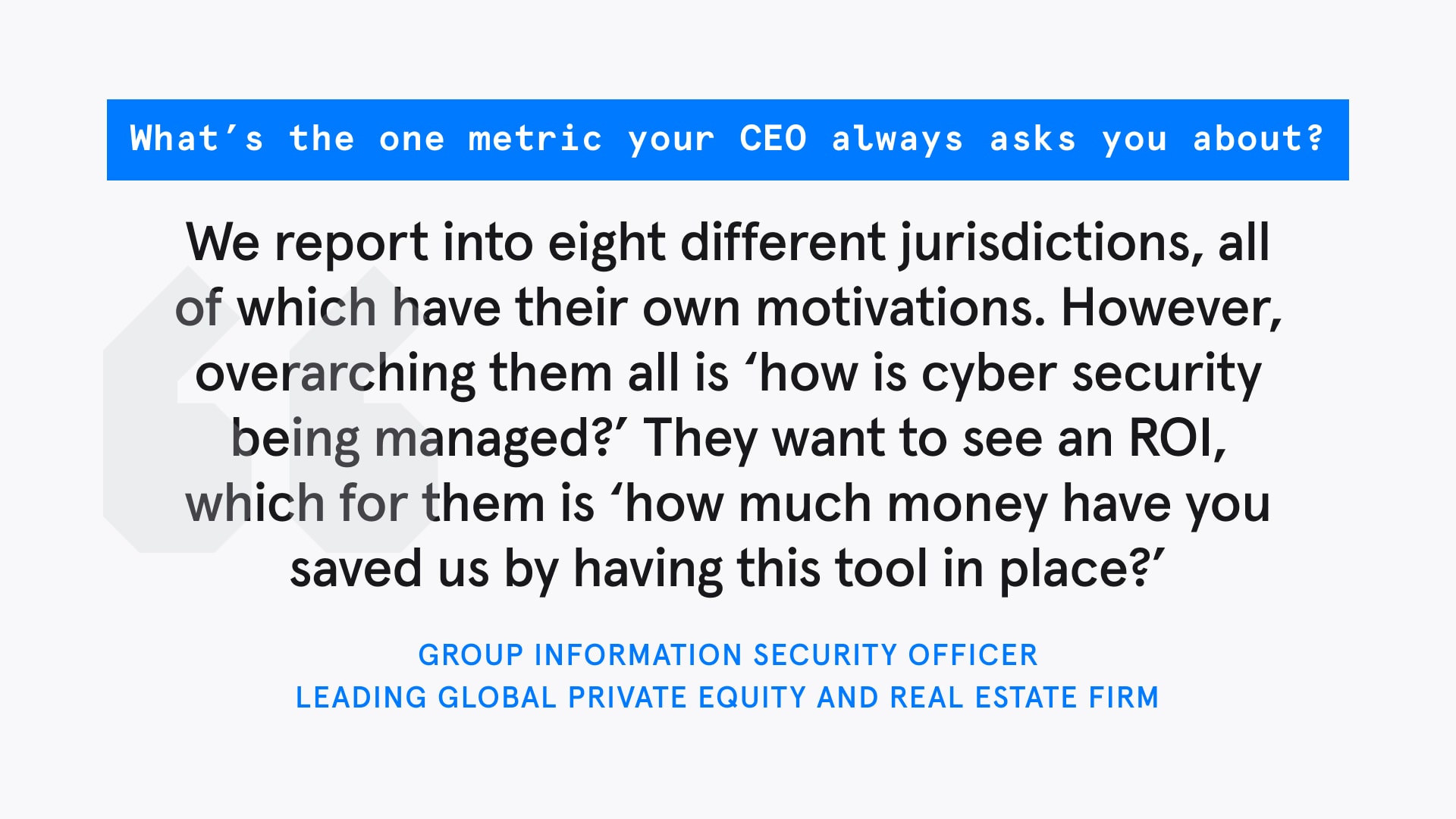
We asked leading CISOs who trust Tessian to protect their business, what was the one metric their CEOs always asked about. Here’s what they told us, so that you can help your CEO (and the rest of the C-suite) see the value in cybersecurity, in ways they’ll understand
Cybersecurity attacks can be highly damaging not only for businesses, but also CEOs themselves, often (very sadly) resulting in their resignation. Examples include Target CEO, Gregg Steinhafel, Equifax’s CEO Richard Smith, LandMark White’s Keith Perrett, and Chris Hylen of Imperva.
A decade ago, a breach might have been seen as an IT issue, and often it was the CIO or other technology-focussed C-suite executive who would take the blame. More recently, though, with the fallout from an attack having financial, operational, reputation and increasingly regulatory ramifications, the buck now stops at the CEO. Indeed by 2024, CEOs will be held personally accountable for breaches according to Gartner. Have we piqued your interest?
Do CEOs understand cybersecurity?
According to the 2021 PwC Annual Global CEO Survey, chief executives cited cyber threats as the number-two risk to business prospects — topped only by pandemics and other health crises. In North America and Western Europe, cyber was number one.
Yet the same report goes on to note that while the top 10% that are “most advanced” in cyber practices or “most improved” on cyber outcomes are in a good position… the majority overall — 63% of organizations — don’t get the kind of support they need from their CEO. The fact is, both the CEO and CISO need to work together to benefit the company.
Here are some more startling facts:
- 64% of CISOs fear their companies are at risk of a major cybersecurity attack in the upcoming year
- 66% feel their organization is unprepared to handle it
- Just 7% of security leaders report directly to the CEO, according to a recent study from Ponemon Institute.
So if your CEO doesn’t get it (or even if they do), here’s our advice on how to update them and the wider C-suite, with answers to metrics that are meaningful, productive, and easily understood.
Metric 1: The Threat Question
One of the first metrics a CEO might want to know can broadly be defined as ‘the threat question’.
Here they’ll ask questions like ‘how big is our attack surface?’ or ‘how well do we understand the threat?’ or ‘where is our biggest source of threats?”. You’ll need up-to-the-minute data on this, but also deeper context of the potential harm these threats could have done to the business.
Metric 2: The Money Question
All CEOs (and CFOs) want to know exactly where the money goes.
Risk calculators can quickly ballpark the cost of a breach depending on your company’s size, sector, and location. This can help give you a Return on Investment (ROI) for your tech stack.. Using Hiscox Group’s Risk Calculator for example, gives $4.7m as the estimated cost of breach for a US healthcare company with revenue of up to $5m, with most of that cost in fines for loss of PII.
The ‘money question’ actually comes in several parts, there’s the immediate loss of revenue while systems are down; fixing this also consumes the company’s time and resources, which also have a cost. But these are relatively small compared to the later costs of regulatory fines and legal action, as well as long-term reputation damage.
Metric 3: The Time Question
Finally, there’s the ‘time’ question. If you’re in InfoSec, you’re realistic enough to know that, at some point, an attack is going to come.
When it does, your ‘identify, deal with, and recover’ times are the metrics you need to communicate to the team, because ‘how quickly can we recover from an attack?’ is the sort of time question your CEO will ask you.
For South African businesses like the Rand Merchant Bank, the Protection of Personal Information Act (POPI Act) came into effect on July 1, 2020, giving organizations one year to be fully compliant. With that time now elapsed, any breach has to be reported to the regulator which is a huge time sink (and can incur several fines).
Get everyone focused on the same metrics
Cybersecurity is a mirror in which the wider C-suite team only sees what matters to each of them, depending on their role:-
The CFO is concerned about potential financial impact.
The CRO focuses on risk insurance.
The General Council is worried about the compliance and regulatory fallout.
As a CISO, you’re probably thinking about the technology and potential vulnerabilities.
The CEO meanwhile, has to pick and mix from this salad bar of metrics and try and formulate a response. A breach will impact everyone in these areas, and so in a sense, they’re everyone’s problem. As the CISO, you need to work with your CEO to iron these out into specific, trackable metrics based on threat, money and time.
What’s the wrong metric to measure for cybersecurity?
We asked cybersecurity professionals via Twitter which was the one metric CEOs always asked about.
The thinking here being that bad actors might choose a softer, less secure target. So as long as we’re better protected than that guy over there, we’re ok. Sadly it doesn’t always work like that.
There are a few issues with this type of question. Firstly, that sort of data isn’t easy to come by, and secondly (and more importantly) security spend is a product of risk appetite, which varies from peer to peer. So you have to ask yourself, “do you feel lucky, punk?”.
As a CISO, putting the detail on the bones of risk, money and time, is what your CEO will want to hear. Tessian can help you with that, from numbers of threats stopped, to amount of time saved.
Andrew Webb
Senior Content Manager