Throughout this year, we saw just how quickly the threat landscape can change.
We all transitioned from the office to our homes overnight. Employees relied on email and other communication and collaboration tools more than ever. And hackers took advantage of the general fear and uncertainty around the pandemic and impersonated health care providers and government organizations.
But, at the same time, Tessian rolled out a number of important product updates to help keep our customers safe, wherever they worked.
Here are the most important product updates to Tessian’s Human Layer Security platform for 2020.
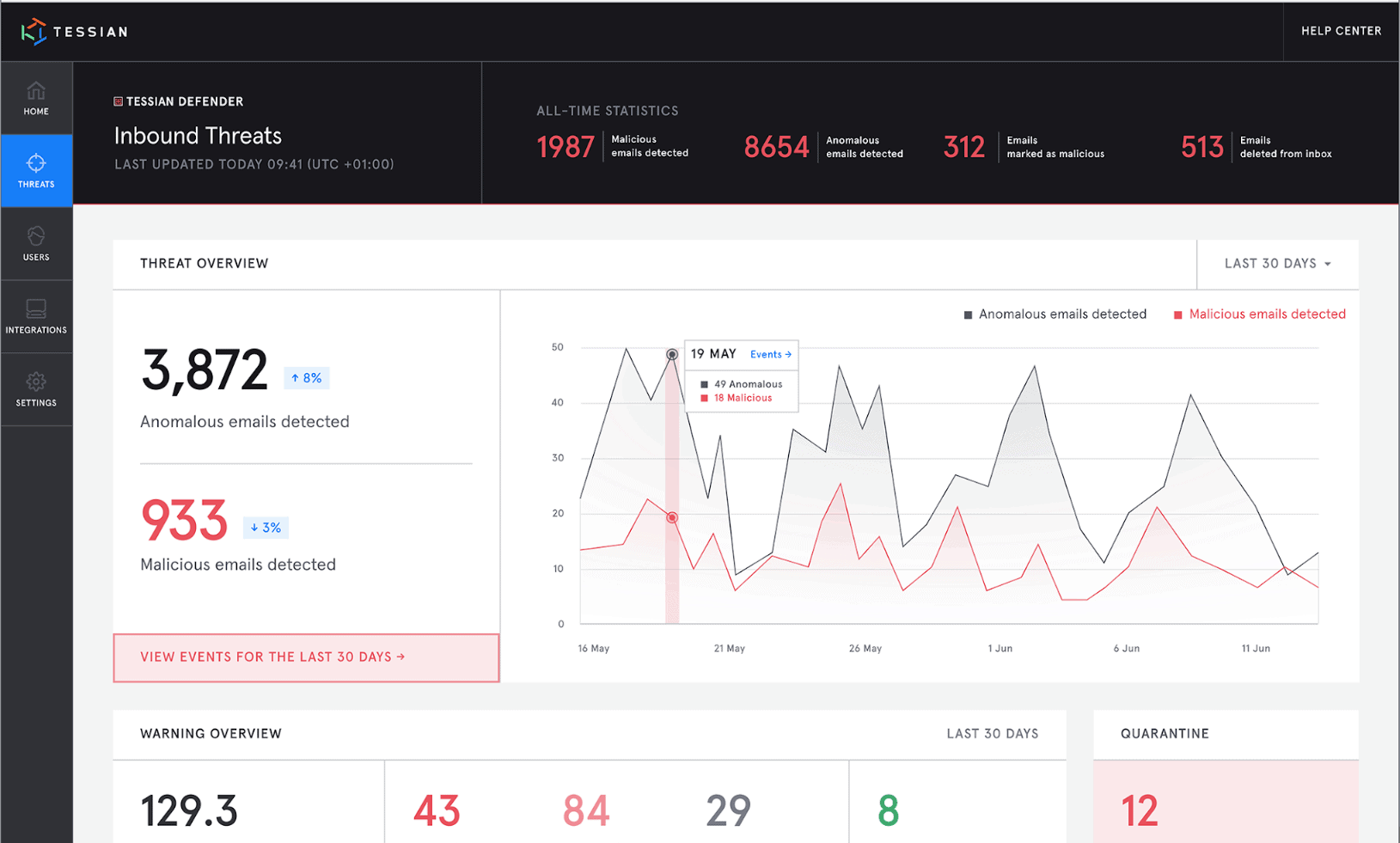
1. Human error, visualized. The new Human Layer Security Intelligence platform gives customers unprecedented visibility into their users’ risk
Tessian customers now have unprecedented visibility into their Human Layer risks. For example, breaking the rules, making mistakes, and being tricked.
The new HLS Intelligence (HLSI) platform automatically surfaces insights about risky employee behavior and high-risk security events, allowing security leaders to know where to focus their efforts. Customers can also benchmark their risk levels against industry peers to help them identify how and where they can improve their security posture.
Investigation and remediation are also effortless. Security teams can take immediate action, from the platform.
Finally, customers can use the Tessian API to receive real-time security events directly into their chosen SIEM or SOAR platform.
Want to learn more about HLSI? We outline all the key features of our new platform in this article.
The new Tessian Human Layer Security Intelligence platform surfaces insights about high-risk security events.
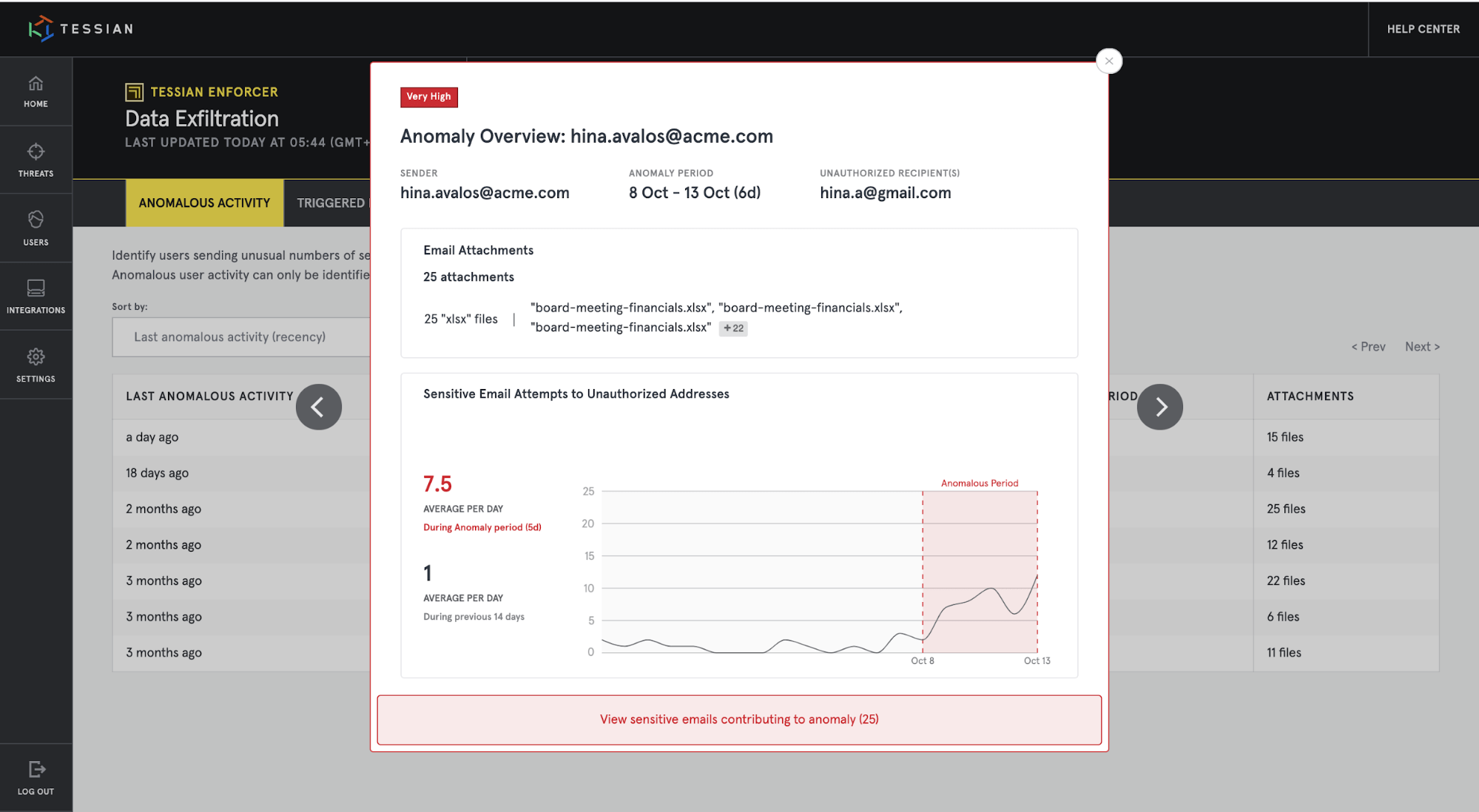
2. Effortless insider threat detection. Automatically detect high-risk data exfiltration activities.
Thanks to new features within Tessian Enforcer, customers can now automatically detect users who suddenly exfiltrate an unusually high amount of data. This allows security and compliance teams to easily spot bad leavers and insider threats, without spending time viewing and investigating individual cases of data exfiltration.
“What we saw after our Proof of Value with Tessian was exciting, but also quite scary. We saw things that we didn’t actually know were happening. Suddenly we had transparency and could see the true scope of the issues we had on email. But, we also saw how employee behavior changes with Tessian.”
Cas de Bie
CIO at Cordaan
Instead, Enforcer automatically analyzes patterns and spot trends that deviate from what’s considered “normal” for a particular employee.
For example, every month, an employee might send their paycheck to their personal email account. Enforcer tracks this behavior, but no action is needed. Why? Because this data isn’t sensitive. But, one day, the employee sends fifteen sensitive emails to his personal account. Enforcer recognizes that this is unusual for the user, and alerts the compliance team, who can take appropriate action.
No manual investigation required.
Tessian Enforcer analyzes and surfaces insights about anomalous employee behavior. In this Anomaly Overview, you can see that during a 6-day period, a particular employee sent much more sensitive information to unauthorized addresses than usual.
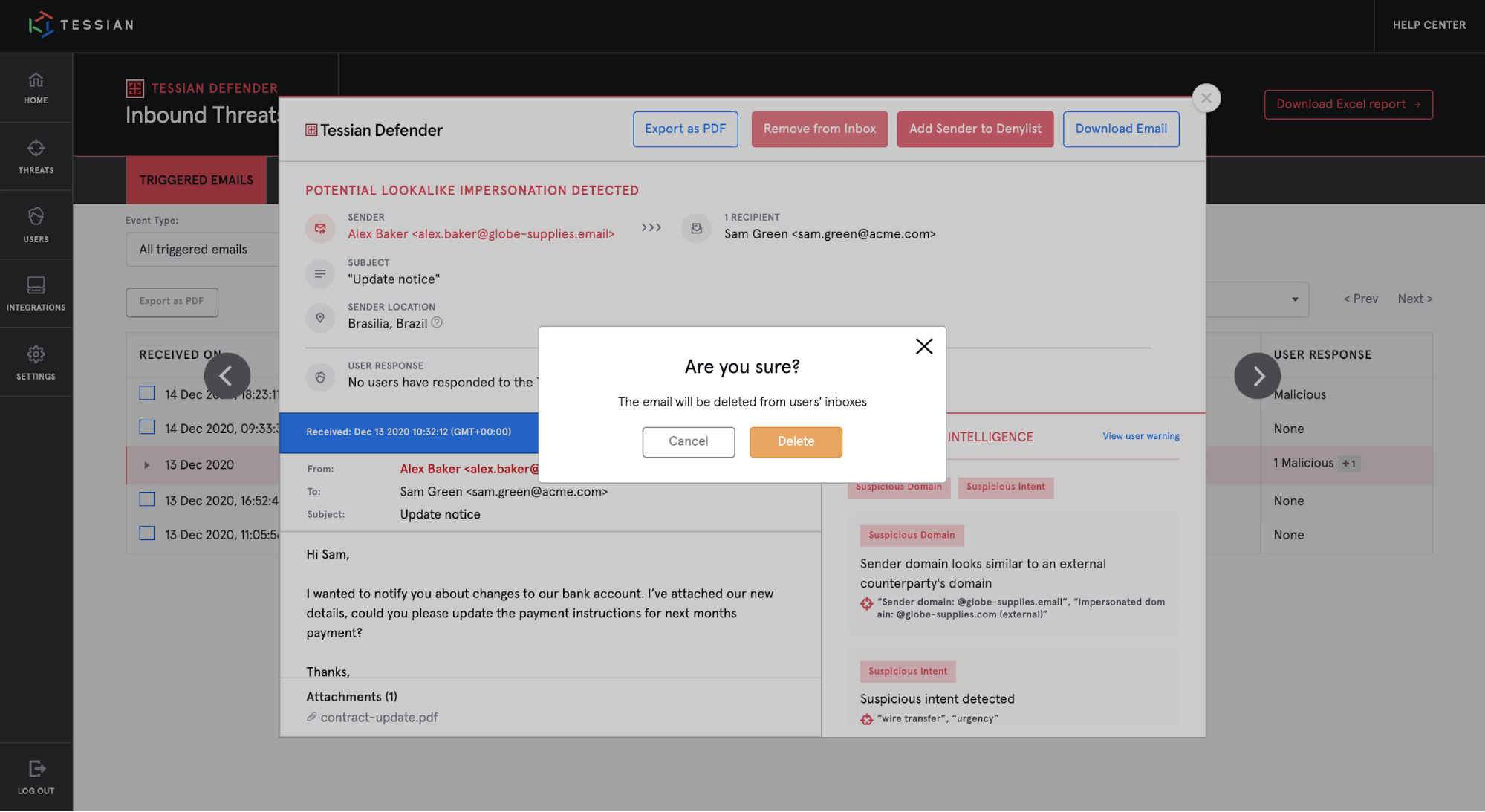
3. Easily identify and remediate attacks. Tessian Defender now provides extensive analysis and remediation tools to security teams
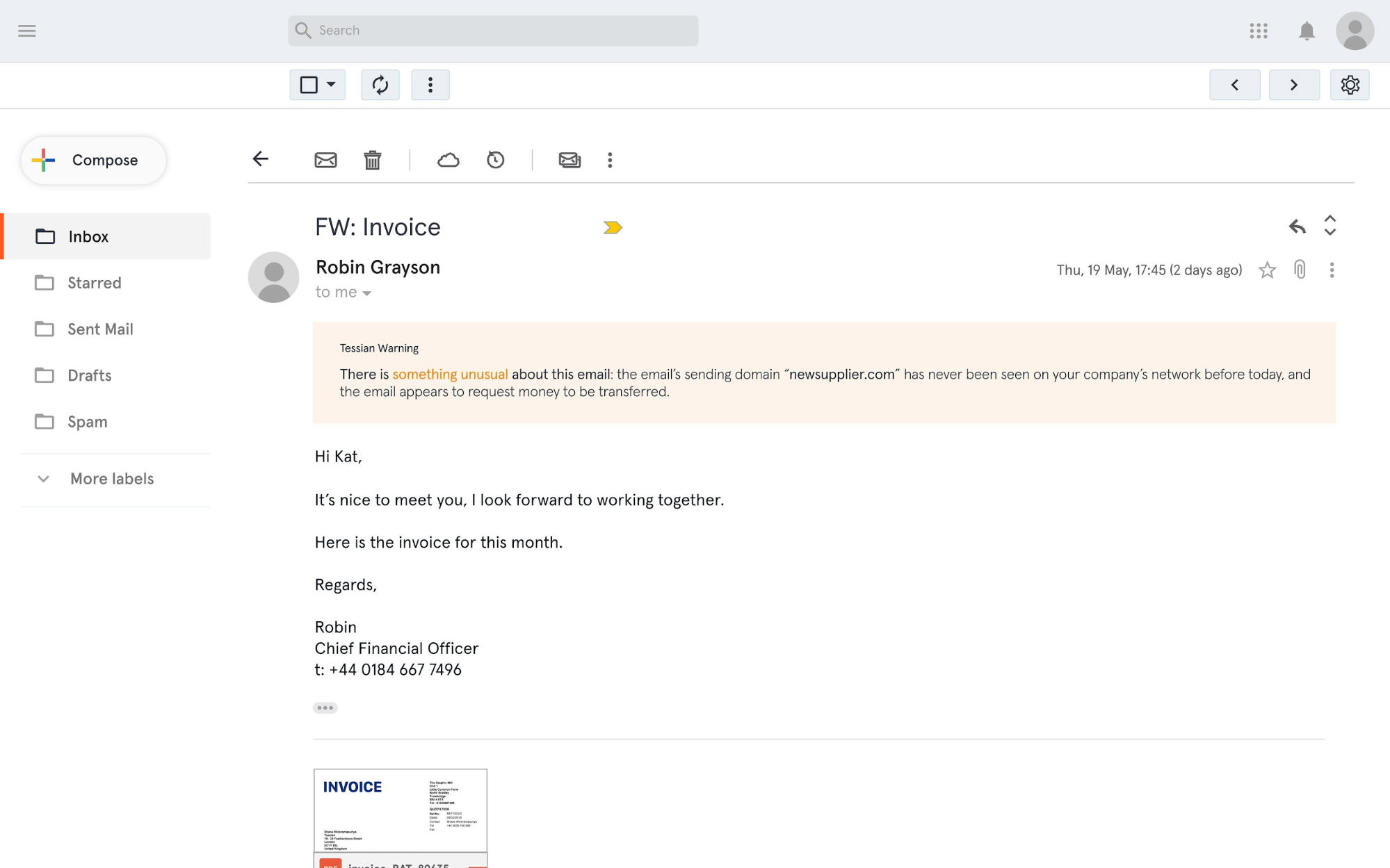
Email attacks are becoming more and more advanced and it’s increasingly complicated for security teams to decide if a suspicious email is a real attack, or a legitimate business email.
Defender now surfaces insights like the geolocation of a suspicious email’s sender to help security teams identify more threats, faster.
Security teams can also speed up their workflows with advanced remediation and prevention capabilities. For example, customers can now delete malicious emails in employees’ mailboxes – directly from the Tessian portal – saving precious time and reducing risk.
And, with Defender Quarantine, customers can also use Defender to proactively prevent threats with a single-click before they enter an employee’s mailbox.
Security teams can delete threats from employee inboxes with a single-click.
4. Leveling up Tessian’s machine learning. Tessian’s modules detect more risks than ever before, with record-low business interruptions
Throughout 2020, Tessian Defender’s machine learning improved to detect an ever-broader spectrum of advanced email attacks that evade legacy security systems.
Defender now protects against threats like brand impersonations and attacks where threat actors exploit Sendgrid vulnerabilities to send spoofed emails.
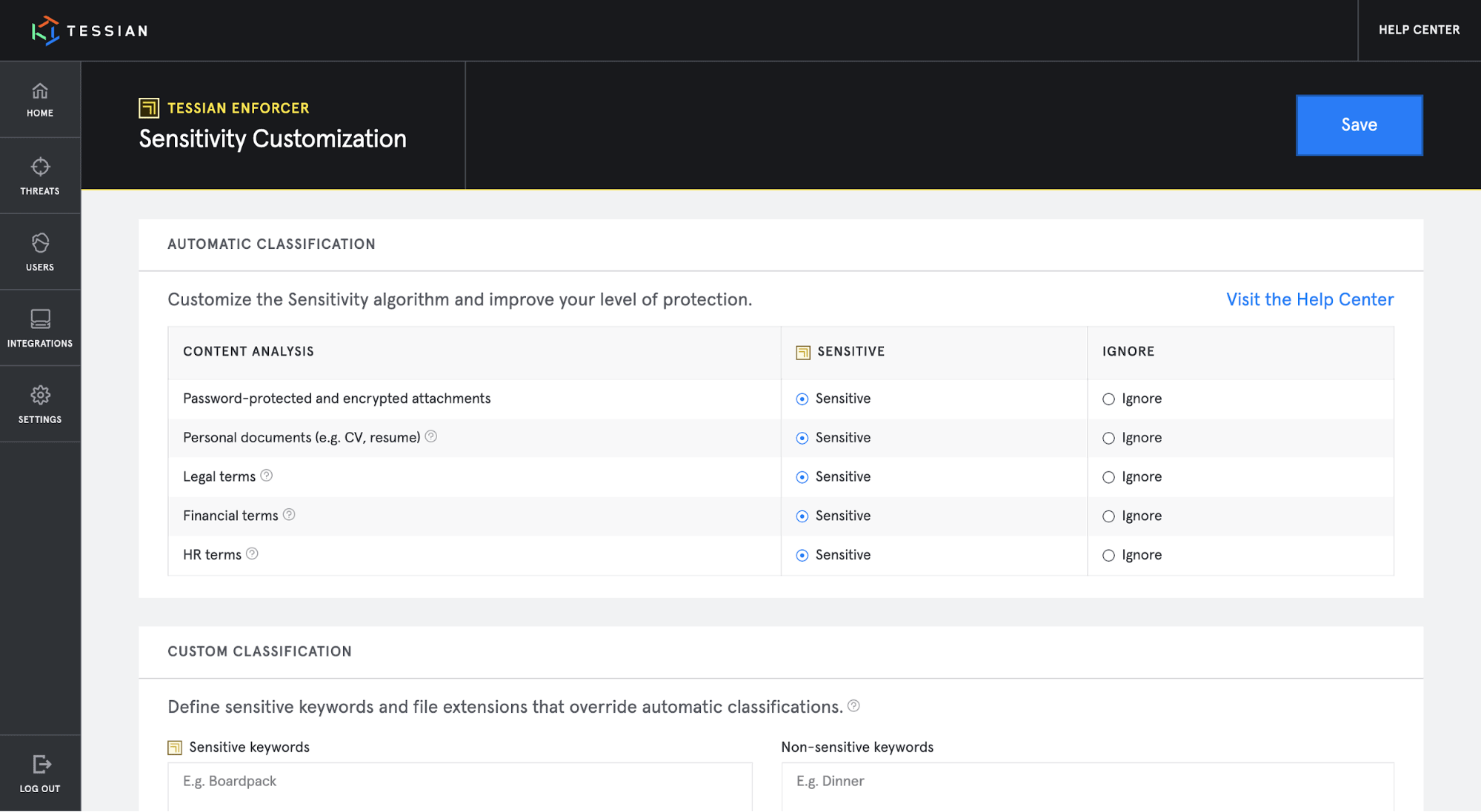
Tessian Enforcer also received a major upgrade, using a new Natural Language Processing (NLP) model that accurately classifies sensitive content in emails and detects topics such as financial, health, or HR data without needing to manually configure keywords or rules.
This means that customers receive significantly better protection against sensitive data-exfiltration attempts with fewer interruptions to their workflow.
Tessian Enforcer makes it easy for security teams to customize their DLP policies, ensuring sensitive content is always accurately classified.
5. In-the-moment learning opportunities. Customers can raise security awareness in their company with contextual warnings
Tessian doesn’t just prevent breaches in real-time. Our platform also educates users to improve their security reflexes and continually drive risk down.
Tessian customers can now educate, raise security awareness, and reinforce training and policies among their employees better than ever before, all while minimizing business interruptions.
“The product is unique in the market. I quickly realized that Tessian could help us give our employees a better understanding of advanced security threats in real-time.”
Erik Ruis
Head of IT at Polarcus
With Tessian Defender, organizations can now educate employees who receive unusual emails that meet specified conditions. For example, security teams might choose to alert employees who receive an email from a new sender that requests money.
Although these kinds of emails aren’t necessarily malicious, you may want to make your user aware of the fact that the sender is new.
With Tessian Enforcer, companies can also choose to show users a custom warning message whenever they try to exfiltrate data, whether done maliciously or accidentally. This allows businesses to easily educate employees or remind them of existing IT policies.
Tessian Defender can educate users and reinforce security training and policies with in-the-moment warnings that explain - in plain English - why an email is considered suspicious or malicious.
Protect your most valuable asset: your people
Tessian has created the world’s first Human Layer Security platform and exciting developments lie ahead as we build out a holistic platform to protect people using email and, eventually, other interfaces frequently used in the workplace.
Not yet a Tessian customer?
Across four modules, Tessian protects the Human Layer by detecting and preventing both inbound and outbound threats. This includes advanced spear phishing attacks, accidental data loss, and data exfiltration.
Tessian is quickly and easily deployed to Office 365, Exchange, and G-Suite, product updates are seamlessly rolled out for users and administrators, and the technology – which doesn’t disrupt workflow – was built with security and productivity in mind.
To understand how Tessian can fit into your existing security framework, check out our customer stories or request a demo now.
Harry Wetherald
Group Product Manager