Hackers love emergencies and times of general uncertainty. Why? Because people are scared, distracted, potentially desperate, and are therefore vulnerable—making them ideal targets.
As COVID-19 continues to spread and global concern about the pandemic rises, bad actors will be impersonating trusted institutions like healthcare organizations, insurance companies, banks, and airlines in order to steal money, harvest credentials, or install malware on your computer…and that’s just on the consumer side.
When it comes to business, trusted individuals and brands will be impersonated. For example, hackers will impersonate out-of-office CxOs and popular web conferencing applications, especially as organizations encourage and rely on remote-working.
Internally at Tessian, we’ve shared tips with our employees on how to spot this type of scam and what to do in case you’re targeted. We think it’s important to spread the message and raise awareness with everyone.
Consumers: What Should You Look For?
- Hackers will be impersonating trusted brands. Carefully inspect all emails, but be especially wary of those coming from healthcare organizations, insurance companies, banks, and airlines, especially those that ask you to “Confirm you are safe”, “Confirm you haven’t traveled to recently affected COVID-19 countries”, or anything similar.
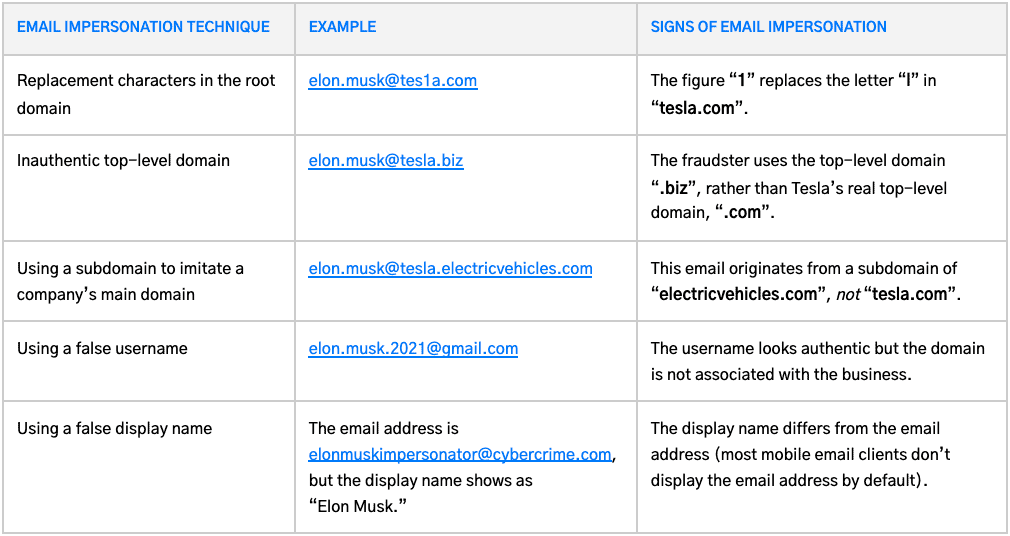
- Look beyond the Display Name and examine the full email address of every sender. While hackers can directly spoof an email address, they’ll often change, remove, or add one letter to the genuine email address, making the difference difficult to spot.
- The goal of a phishing attack is to steal money, harvest credentials, or install malware. That means hackers will motivate you to act, either by encouraging you to download an attachment, follow a link, transfer money, or respond with personal details. These are all red flags.
- While hackers can certainly craft perfectly believable correspondence, phishing emails may contain spelling errors or branding inconsistencies either in the logo, email template, or a landing page.
Employees: What Should You Look For?
- Hackers will be impersonating people within your organization and third-parties like suppliers or vendors. You should be cautious when responding to any internal email that mentions the sender being out-of-office and any third-party email that comes from a source you don’t recognize or that requires urgent action.
- Look beyond the Display Name and examine the full email address of every sender. While hackers can directly spoof an email address, they’ll often change, remove, or add one letter to the genuine email address, making the difference difficult to spot.
- The goal of a phishing attack is to steal money, harvest credentials, or install malware. That means hackers will motivate you to act, either by encouraging you to download an attachment, follow a link, transfer money, or respond with personal details. These are all red flags.
- While hackers can certainly craft perfectly believable correspondence, phishing emails may contain spelling errors, language or requests that are out-of-character, and branding inconsistencies.
These red flags are all a bit easier to spot when you have a bit more context. Below are just a few examples of phishing emails that you may see over the next few weeks.